[ad_1]

Several platform certificates used by OEM Android device vendors to digitally sign backend system apps have been used by threat actors to sign apps that contain malware.
OEM Android device manufacturers use platform certificates or platform keys to sign device master ROM images containing the Android operating system and associated applications.
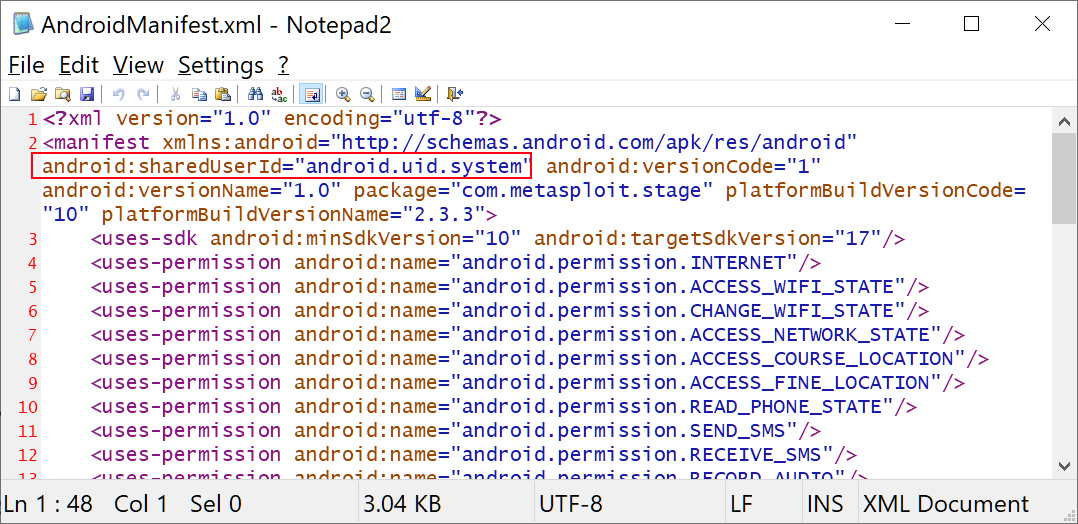
If apps, even malicious ones, are signed with the same platform certificate and given the highly privileged user ID “android.uid.system”, those apps will also gain system-level access to the android device.
Source: BleepingComputer
These privileges grant access to sensitive permissions not normally granted to applications, such as managing calls in progress, installing or removing packages, collecting device information, and other very important actions. sensitive.
As shared in a now public report on the Android Partner Vulnerability Initiative (AVPI) issue tracker, this misuse of platform keys was discovered by Łukasz Siewierski, a reverse engineer on Google’s Android security team.
“A platform certificate is the application signing certificate used to sign the “android” application on the system image. The “android” application runs with a highly privileged user credential – android. uid.system – and holds system permissions, including user data access permissions,” the Google reporter explains.
“Any other app signed with the same certificate can declare that it wants to run with the same user ID, giving it the same level of access to the Android operating system.”
Siewierski spotted several malware samples signed using these ten Android platform certificates and provided the SHA256 hashes for each of the samples and the digitally signed certificates.
At this time, there is no information on what led to the misuse of these certificates to sign malware – whether one or more threat actors stole them or whether an insider with authorized access signed APKs with vendor keys.
Also, there is no information about where these malware samples were found – whether they were found on the Google Play Store or whether they were distributed via third-party stores or during malicious attacks.
The package names for the ten listed malware examples signed with platform keys are listed below:
com.russian.signato.renewis
com.sledsdffsjkh.Search
com.android.power
com.management.propaganda
com.sec.android.musicplayer
com.houla.quicken
com.attd.da
com.arlo.fappx
com.metasploit.stage
com.vantage.ectronic.cornmuniLeaked certificates belong to Samsung, LG, Revoview and MediaTek
A search on VirusTotal for these hashes led BleepingComputer to discover that some of the abused platform certificates belong to Samsung Electronics, LG Electronics, Revoview, and Mediatek.
For the other certificates, it was not possible to determine to whom they belonged at the time.
Malware signed with their certificates includes those detected as HiddenAd Trojans, infostealers, Metasploit, and malware droppers that hackers can use to deliver additional malicious payloads to compromised devices.
Google notified all affected vendors of the abuse and advised them to rotate their platform certificates, investigate the leak to find out how it happened, and keep the number of signed apps to a minimum. with their Android platform certificates to avoid future incidents.
“All parties involved should rotate the platform certificate by replacing it with a new set of public and private keys. In addition, they should conduct an internal investigation to find the root cause of the problem and take measures to avoid that the incident does not happen again in the future,” the Google reporter added.
“We also strongly recommend minimizing the number of applications signed with the platform certificate, as this will significantly reduce the cost of rotating platform keys if a similar incident occurs in the future.”
An easy way to get an overview of all Android apps signed with these potentially compromised certificates is to use APKMirror to find them (a list of apps signed with Samsung certificate and one of LG-signed apps).
However, based on the results, even though Google stated that “all relevant parties have been notified of the findings and have taken corrective action to minimize user impact”, it appears that not all vendors have not followed Google’s recommendations since, at least in the case of Samsung. cases, leaked platform certificates are still used to digitally sign applications.
When we contacted Google about these compromised keys, Google told BleepingComputer that it had added detections for compromised keys as a result of Android build tests (BTS) and malware detections to Google Play Protect.
“OEM partners quickly implemented mitigations as soon as we reported the key compromise. End users will be protected by user mitigations implemented by OEM partners,” Google said in a statement to BleepingComputer. .
“Google has broad detections for malware in Build Test Suite, which scans system images. Google Play Protect also detects malware.”
“There is no indication that this malware is or was on the Google Play Store. As always, we advise users to ensure they are running the latest version of Android.”
[ad_2]
Source link
