[ad_1]

A new malware distribution campaign is underway to impersonate the CapCut video editing tool to push various strains of malware to unsuspecting victims.
CapCut is ByteDance’s official video editor and creator for TikTok, supporting music mixing, color filters, animation, slow-motion effects, picture-in-picture, stabilization, and more.
It has over 500 million downloads on Google Play alone and its website receives over 30 million visits per month.
The app’s popularity, combined with nationwide bans in Taiwan, India and elsewhere, has caused users to seek other ways to download the program.
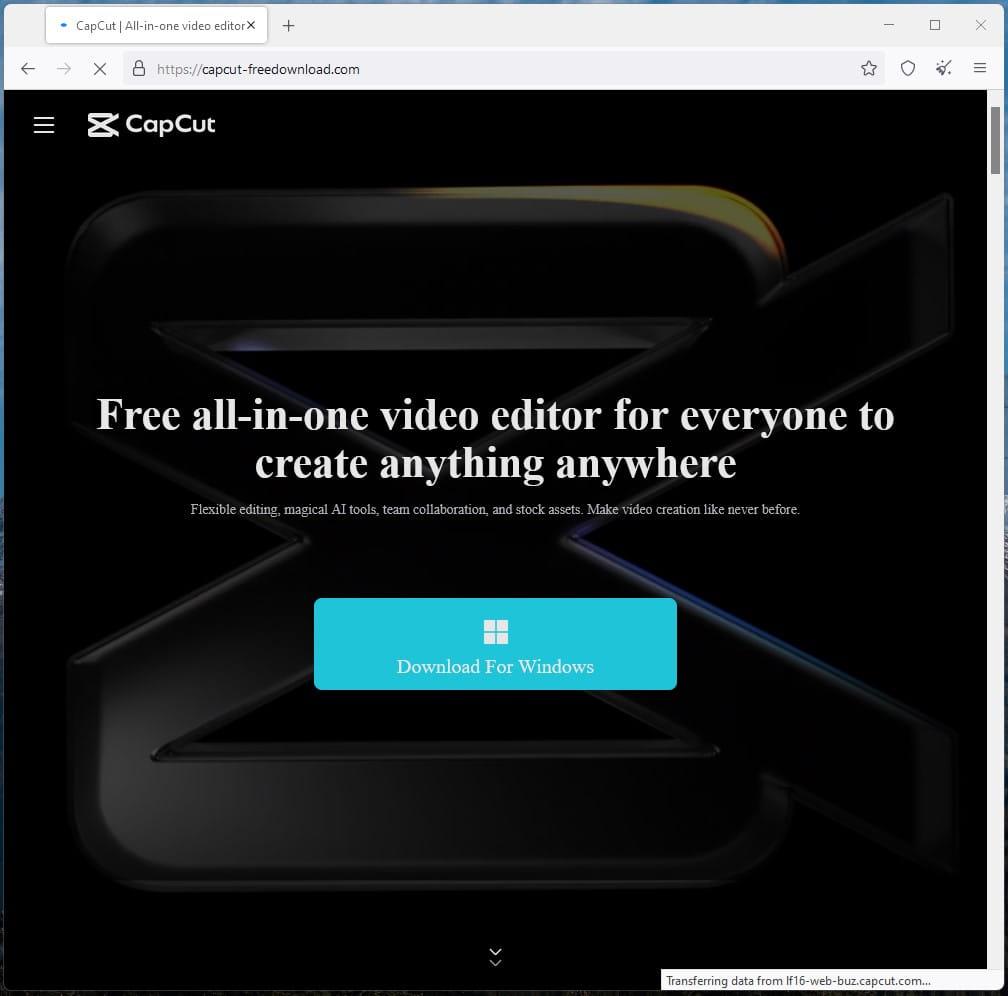
However, threat actors exploit this by creating websites that distribute malware disguised as CapCut installers.
The malicious websites were discovered by Cyblewho reports seeing two campaigns distributing different strains of malware.
No specific information on how victims are directed to these sites has been provided, but typically threat actors use Black Hat SEO, search ads, and social media to promote the sites.
Source: BleepingComputer
The offending websites are:
- capcut-freedownload[.]com
- capcutfreedownload[.]com
- capcut-video-editor[.]com
- capcutdownload[.]com
- capcutpc-download[.]com
At the time of writing, all areas have since been taken offline.
First campaign
The first campaign spotted by Cyble analysts uses fake CapCut sites featuring a download button that delivers a copy of the Offx Stealer to the user’s computer.
The Steler binary was compiled on PyInstaller and will only work on Windows 8, 10 and 11.
When the victim runs the downloaded file, they get a fake error message claiming that the launch of the application failed. However, Offx Stealer continues to run in the background.
The malware will attempt to extract passwords and cookies from web browsers and specific file types (.txt, .lua, .pdf, .png, .jpg, .jpeg, .py, .cpp, and .db ) from the user’s desktop folder.
It also targets data stored in messaging apps like Discord and Telegram, cryptocurrency wallet apps (Exodus, Atomic, Ethereum, Coinomi, Bytecoin, Guarda, and Zcash), and remote access software like UltraViewer and AnyDesk.
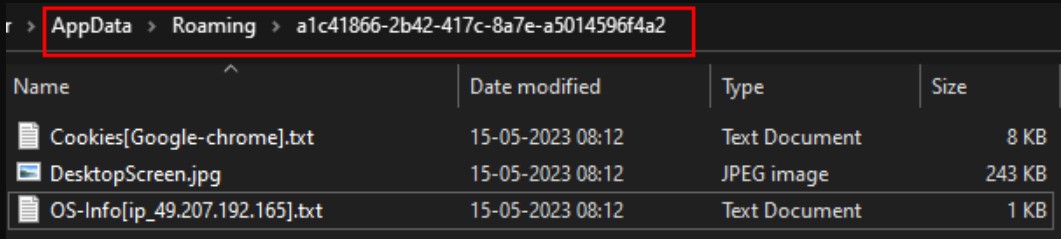
All stolen data is saved in a randomly generated directory in the %AppData% folder, compressed, and then sent to malware operators on a private Telegram channel. Threat actors also use AnonFiles file hosting service for redundancy in the exfiltration step.
After the stolen files are handed over to the attackers, the local directory created to temporarily house the data is deleted to erase all traces of the infection.
Second campaign
The second campaign involving fake CapCut sites drops a file named “CapCut_Pro_Edit_Video.rar” on victims’ devices, containing a batch script which, in turn, triggers a PowerShell script when opened.
Cyble says that at the time of his scan, no antivirus engine would flag the batch file as malicious, so the loader is very stealthy.
The PowerShell script decrypts, unpacks, and loads the final payload: Redline Stealer and a .NET executable.
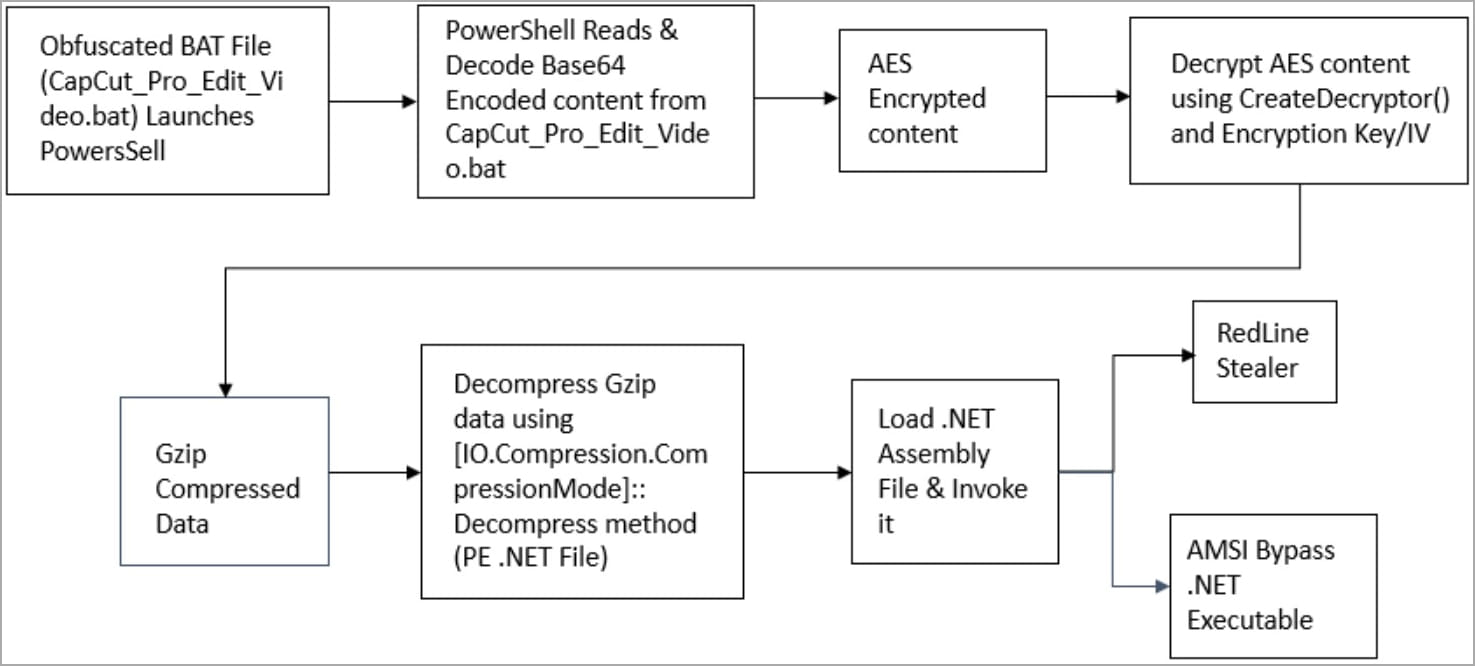
Redline is a widely deployed information stealer that can retrieve data stored in web browsers and applications, including credentials, credit cards, and auto-complete data.
The role of the .NET payload is to bypass the Windows AMSI security feature, allowing Redline to run undetected on the compromised system.
To stay safe from malware, download software directly from official sites rather than sites shared in forums, social media or direct messages, and also make sure to avoid promoted results when searching software tools on Google.
In this case, CapCut is available via capcut.com, google play (for Android), and the App store (for iOS).
[ad_2]
Source link
