[ad_1]

Chinese state-backed hackers have developed a Linux variant for the SideWalk backdoor used against Windows systems belonging to academic targets.
The malware is attributed with high confidence to the threat group SparklingGoblin, also tracked as Earth Baku, which is believed to be connected to the cyber espionage group APT41.
Targeting the university sector
The SideWalk Linux backdoor has been observed in the past, initially tracked as StageClient by security researchers from cybersecurity firm ESET.
An early variant of the malware was spotted by researchers from 360 Netlab, the threat intelligence team of Chinese internet security firm Qihoo 360, and detailed two years ago in a blog post on the Specter botnet hitting IP cameras.
After analyzing Specter and StageClient, ESET researchers determined that both malware had the same root and were Linux variants of SideWalk.
In 2021, Trend Micro researchers documented new tools from a cyber espionage campaign attributed to APT41/Earth Baku, including the SideWalk backdoor, which they track as ScrambleCross.
ESET notes in a report today that while SideWalk Linux has been used against multiple targets in the past, their telemetry data shows that the variant they discovered was deployed against a single victim in February 2021, a university in Hong Kong.
SparkGoblin has focused on the same target in the past, compromising the same university in May 2020, when student protests.
“The group has continuously targeted this organization over an extended period of time, successfully compromising several key servers, including a print server, an email server, and a server used to manage student schedules and class registrations” – ESET
Although SparklingGoblin primarily attacks targets in East and Southeast Asia, the group has also struck organizations outside of these regions, focusing on the academic sector.
SideWalk for Windows ready for Linux
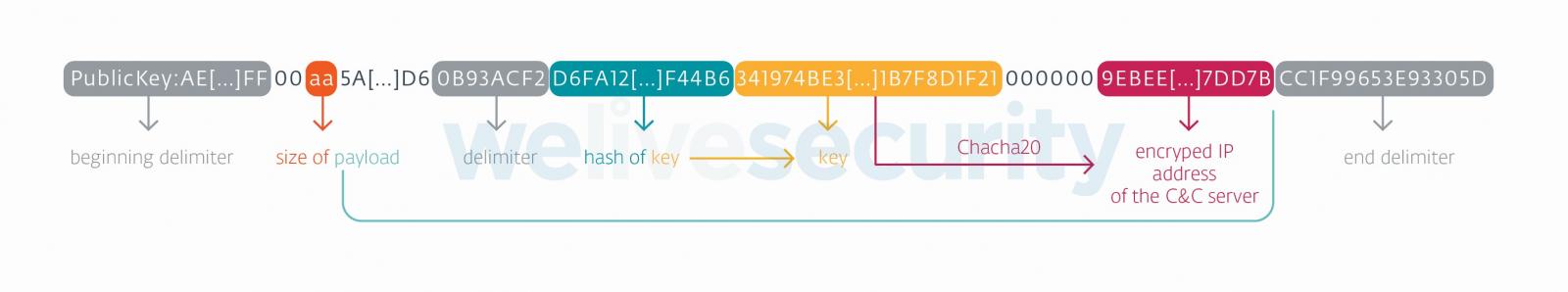
While reviewing the SideWalk variants for Linux and Windows, ESET noticed “striking” similarities in their operation, implementation of multiple components, and dropped payloads on the compromised system.
The researchers say that both variants implemented the ChaCha20 encryption algorithm to “use a counter with an initial value of 0x0B”, which is unique to SideWalk.
On Windows and Linux, the malware uses the same five threads, running simultaneously, for specific tasks:
- [StageClient::ThreadNetworkReverse] – fetch proxy configurations for alternative connections to command and control (C2) server
- [StageClient::ThreadHeartDetect] – close the connection to the C2 server when commands are not received within the specified time
- [StageClient::ThreadPollingDriven] – send heartbeat commands to C2 server if there is no information to provide
- [StageClient::ThreadBizMsgSend] – check data to send in message queues for all other threads and process it
- [StageClient::ThreadBizMsgHandler] – check pending messages from C2 server
ESET researchers also found that the Linux and Windows variants for SideWalk had the same payload delivered via the dead-drop resolution string hosted in a Google Docs file.
source: ESET
Another piece of evidence linking the two variants of SideWalk to the same threat actor was that they both used the same encryption key to transport data from the infected machine to the C2 server.
SparklingGoblin has the capabilities to develop malware tailored to its needs, as evidenced by the SideWalk Linux variant. However, the group also has access to implants seen in operations attributed to other Chinese hacking groups.
ESET researchers say SparklingGoblin has access to ShadowPad backdoor and Winnti malware.
[ad_2]
Source link
