[ad_1]

Chinese hacking group Mustang Panda has been seen deploying a new custom backdoor codenamed “MQsTTang” in attacks starting this year.
Mustang Panda is an Advanced Persistent Threat (APT) group known for targeting organizations around the world in data theft attacks using customized versions of the PlugX malware. The threat actors are also known as TA416 and Bronze President.
Mustang Panda’s new MQsTTang backdoor malware does not appear to be based on previous malware, indicating that hackers likely developed it to evade detection and make attribution more difficult.
ESET researchers discovered MQsTTang in a campaign that started in January 2023 and is still ongoing. The campaign targets governmental and political organizations in Europe and Asia, focusing on Taiwan and Ukraine.
Malware distribution is done through spear phishing emails, while payloads are downloaded from GitHub repositories created by a user associated with previous Mustang Panda campaigns.
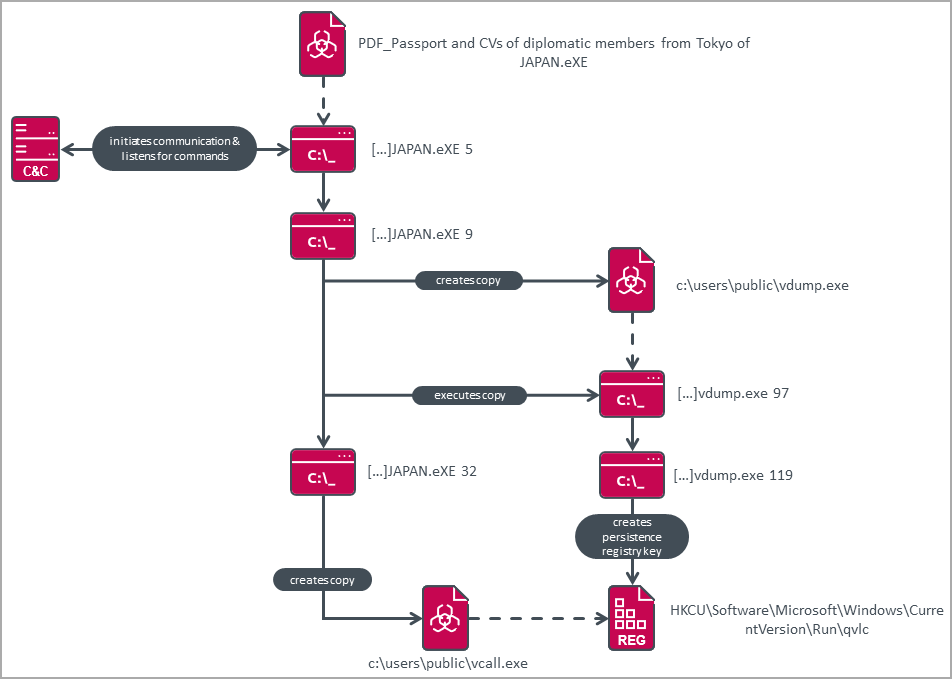
The malware is an executable compressed inside RAR archives, bearing diplomatic-themed names, such as scans of passports of members of diplomatic missions, embassy notes, etc.
The new MQsTTang backdoor
ESET characterizes MQsTTang as a “barebones” backdoor that allows the threat actor to execute commands remotely on the victim’s machine and receive their output.
“This new MQsTTang backdoor provides a sort of remote shell without any of the bells and whistles associated with other malware families in the group,” reads the ESET report.
On launch, the malware creates a copy of itself with a command line argument that performs various tasks, such as starting C2 communications, establishing persistence, etc.
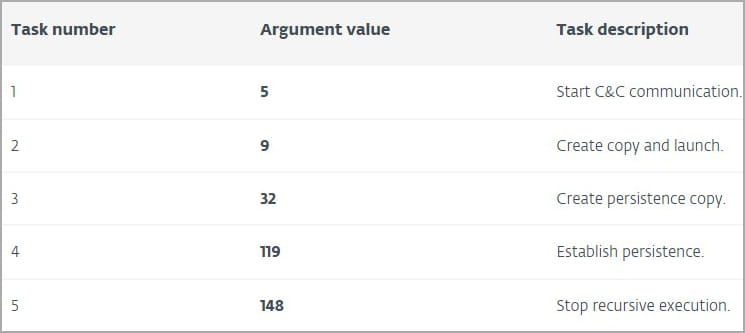
Persistence is established by adding a new registry key under “HKCU\Software\Microsoft\Windows\CurrentVersion\Run”, which launches the malware on system startup. After the restart, only communication task C2 is executed.
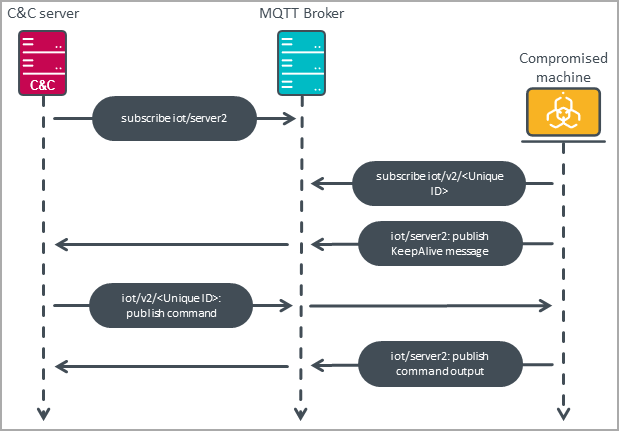
An unusual feature of the new backdoor uses the MQTT protocol for command and control server communications.
MQTT gives the malware good resistance to C2 drops, hides the attacker’s infrastructure by passing all communications through a broker, and makes it less likely to be detected by defenders looking for more commonly used C2 protocols .
To evade detection, MQsTTang checks for the presence of debuggers or monitoring tools on the host, and if it finds any, it modifies its behavior accordingly.
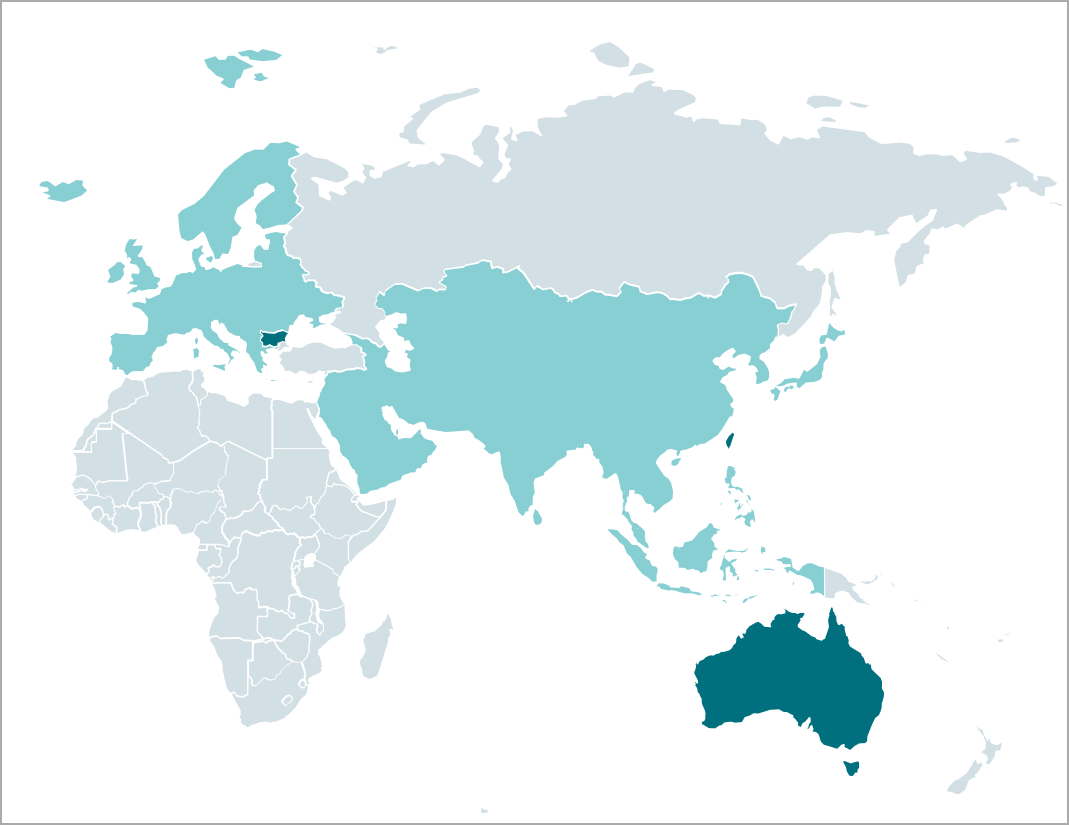
Another recent Mustang Panda operation was observed between March and October 2022 by Trend Micro analysts, who reported seeing significant targeting against organizations in Australia, Japan, Taiwan, and the Philippines.
In this campaign, the threat group used three malware strains, namely PubLoad, ToneIns and ToneShell, which are not present in the 2023 campaign spotted by ESET.
It remains to be seen if MQsTTang will be part of the group’s long-term arsenal or if it was specifically developed for a specific operation.
[ad_2]
Source link
