[ad_1]

A phishing-as-a-service (PhaaS) platform dubbed ‘Caffeine’ makes it easy for threat actors to launch attacks, with an open registration process allowing anyone to jump in and launch their own campaigns of phishing.
Caffeine doesn’t require invites or referrals, or wannabe bad actors to get approval from an admin on Telegram or a hacking forum. Because of this, it removes much of the friction that characterizes almost all platforms of this type.
Another distinctive feature of Caffeine is that its phishing patterns target Russian and Chinese platforms, whereas most PhaaS platforms tend to focus on decoys for Western services.
Mandiant analysts discovered and tested caffeine thoroughly, and today reports that it is a worryingly feature-rich PhaaS given its low barrier to entry.
The cybersecurity firm first spotted Caffeine after investigating a large-scale phishing campaign conducted through the service, targeting one of Mandiant’s customers to steal Microsoft 365 account credentials.
Power phishing campaigns
Caffeine requires the creation of an account, after which the operator gets immediate access to the “Store”, which contains tools for creating phishing campaigns and an overview dashboard.
Then operators must purchase a subscription license, which costs $250 per month, $450 for three months, or $850 for six months, depending on features.
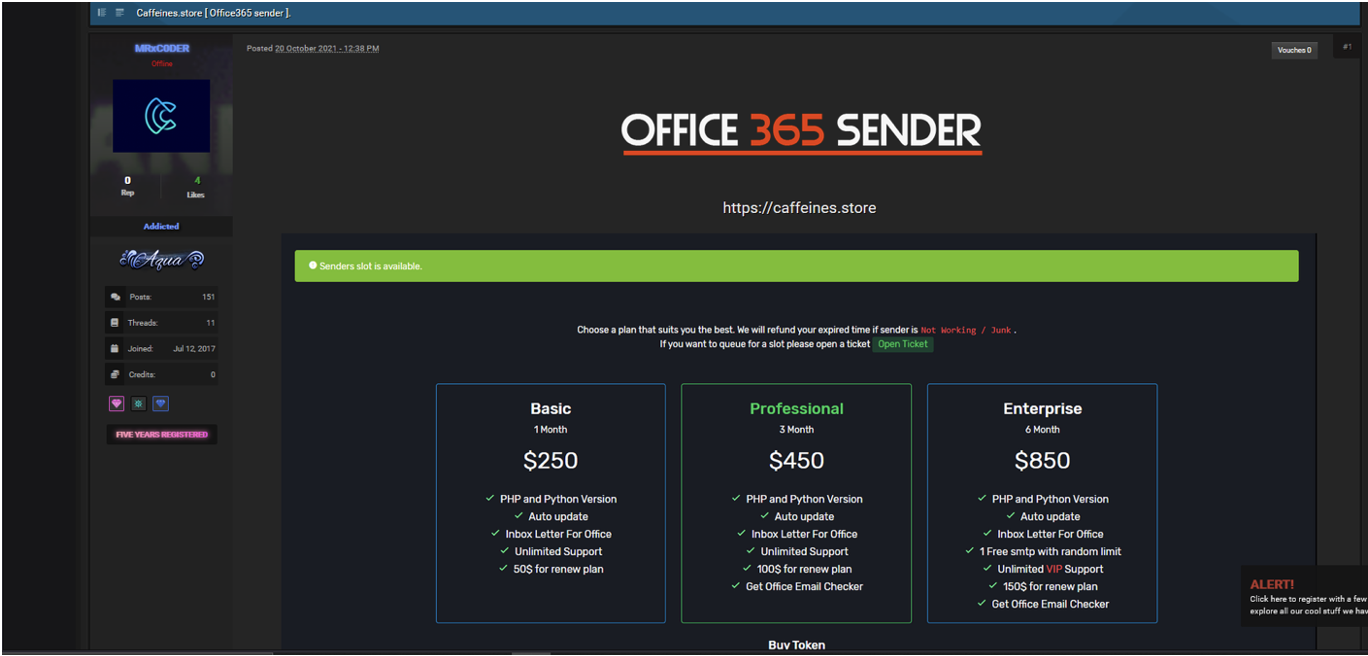
That’s about 3-5 times the cost of a typical PhaaS subscription, and Caffeine tries to make up for it by offering anti-detection and anti-analysis systems and customer support services.
In terms of phishing options, some of the advanced features offered by the platform include:
- Mechanisms to customize dynamic URL schemes to help dynamically generate pre-populated pages with victim-specific information.
- First stage campaign redirect pages and final lure pages.
- IP blocklist options for geo-blocking, blocking based on CIDR range, etc.
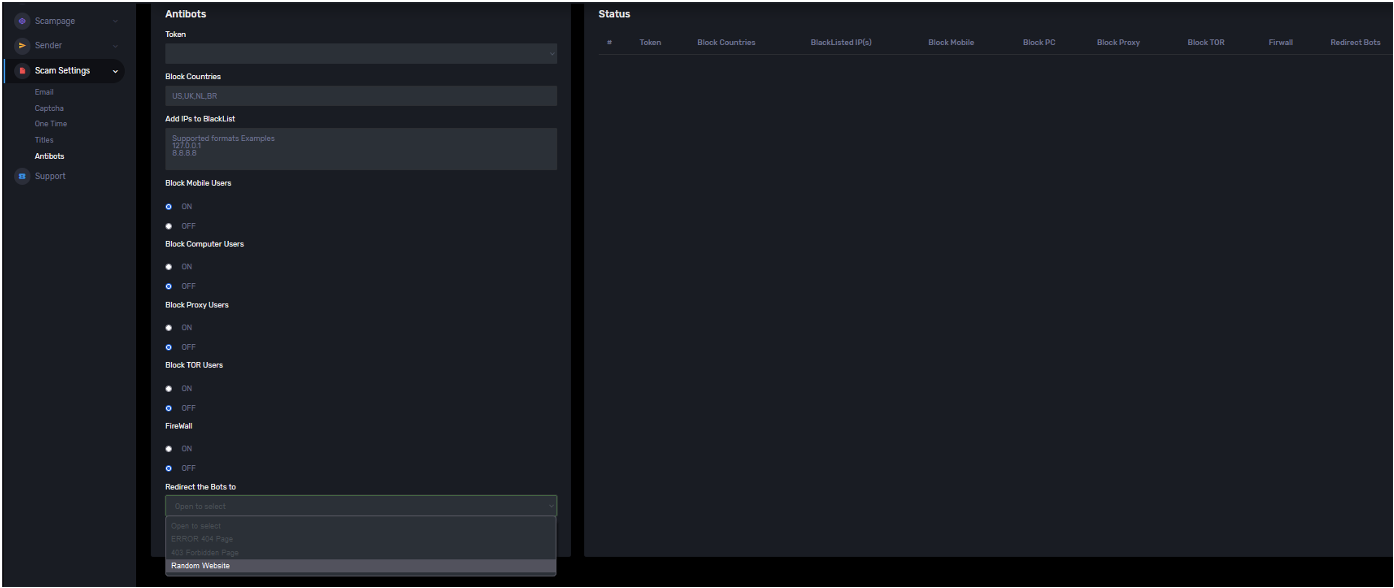
After defining the main parameters for the phishing campaign, operators will need to deploy the phishing kit, currently limited to a Microsoft 365 login page, and then select a phishing template.
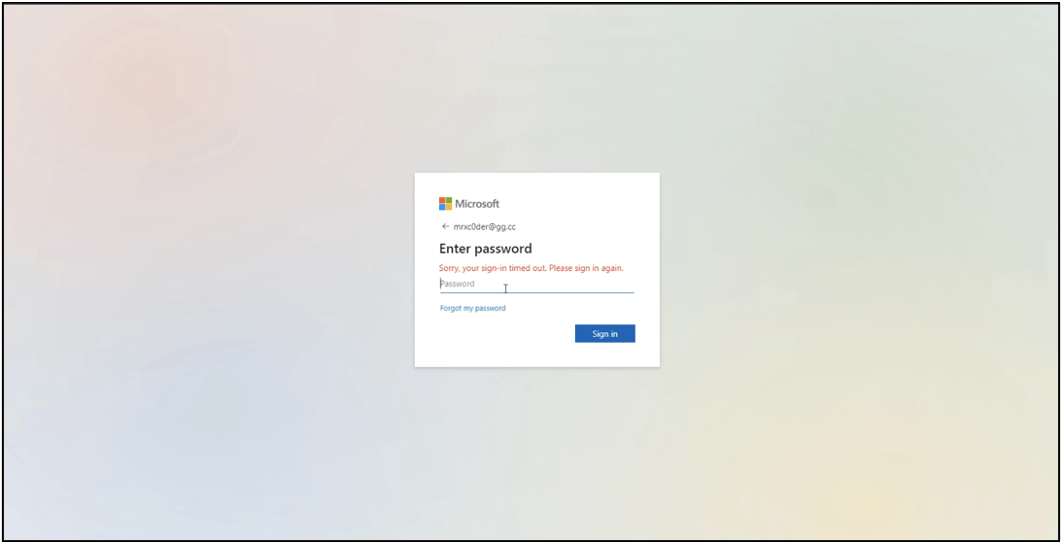
Caffeine offers several phishing model options, including Microsoft 365 and various decoys for Chinese and Russian platforms. Mandiant thinks more will be added soon.
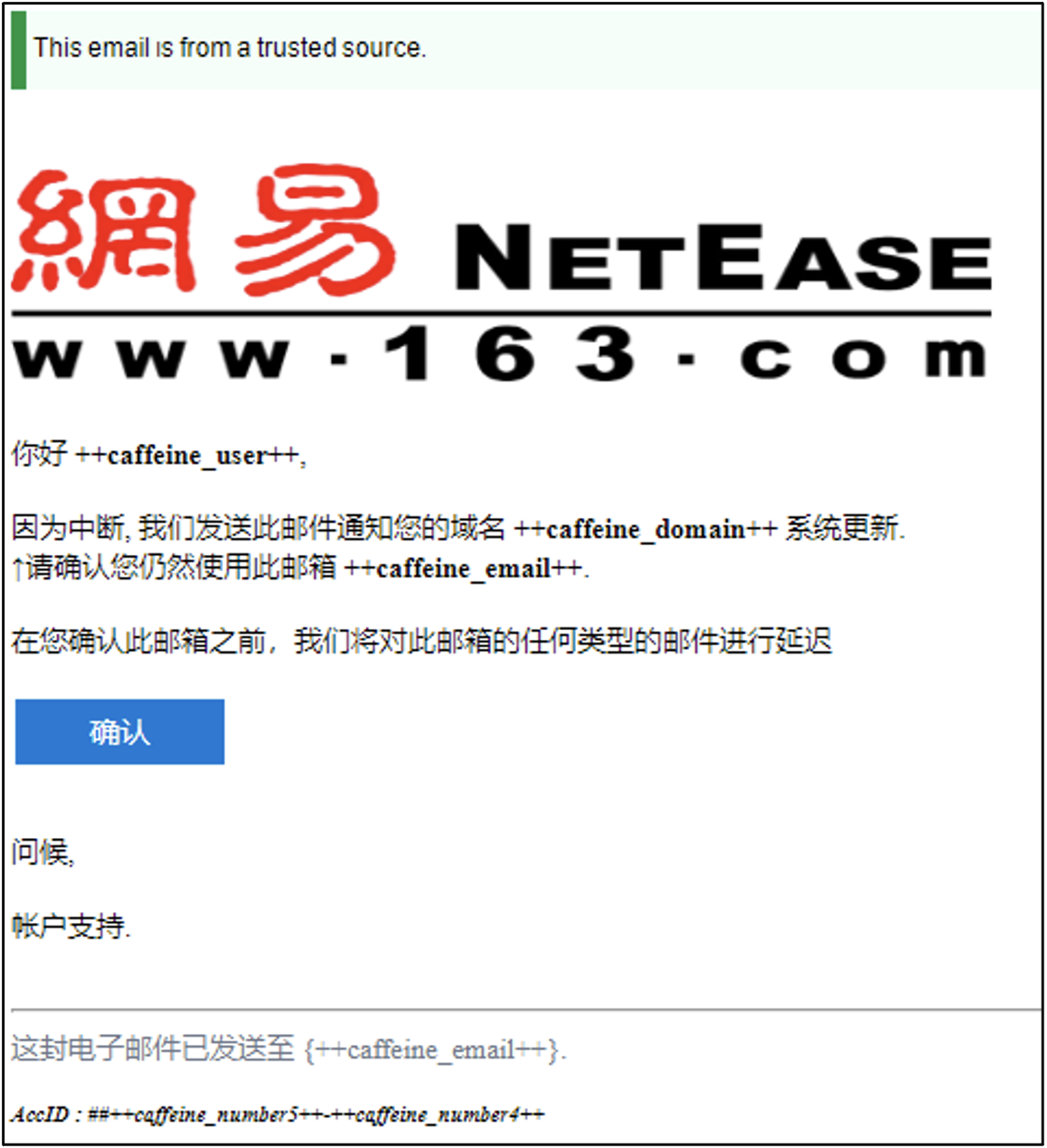
The platform also allows operators to use its own Python or PHP-based email management utility to send phishing emails to their targets, reducing the need for external tools.
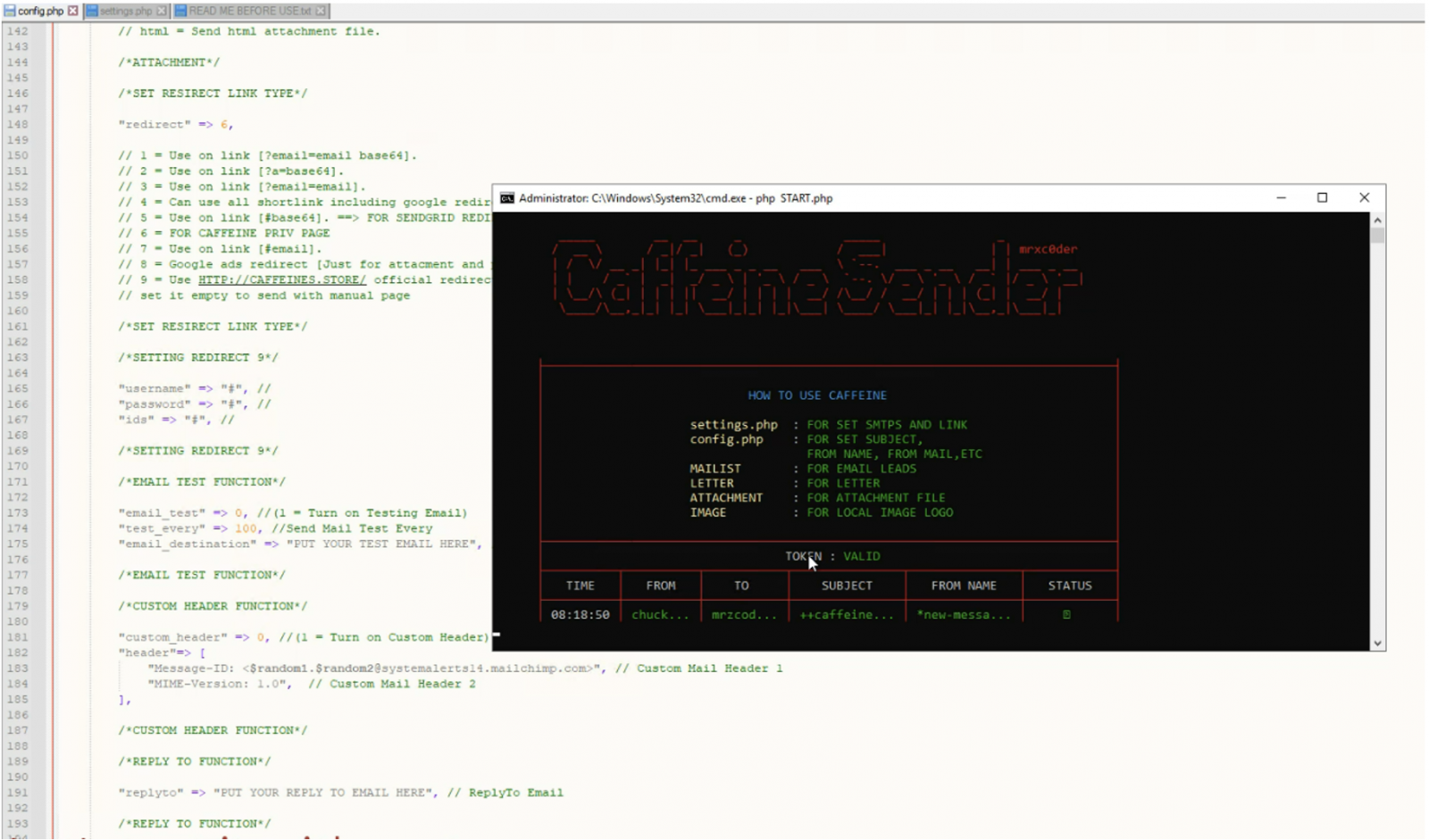
While Mandiant provides detection tips for intercepting Caffeine-backed phishing emails, analysts point to the possibility of scammers adopting new evasion techniques that could render the section of this report obsolete.
Unfortunately, caffeine is another option added to the choices available to low-skilled cybercriminals looking for automated rigs, which could become a bigger problem if more models are added to its collection.
[ad_2]
Source link
