[ad_1]

The FBI and CISA have issued a joint advisory to warn that the Bl00dy Ransomware gang is also actively exploiting a PaperCut remote code execution vulnerability to gain initial access to networks.
The US Cybersecurity and Infrastructure Security Agency mentions that the threat actor has focused its attacks on the education sector, which has significant public exposure of the flaw.
“In early May 2023, according to FBI information, the Bl00dy Ransomware gang gained access to victim networks in the educational institutions subsector where PaperCut servers vulnerable to CVE-2023-27350 were exposed to the Internet,” read it security consulting
“Ultimately, some of these operations led to data exfiltration and encryption of victim systems.”
The PaperCut flaw is identified as CVE-2023-27350 and is a critical severity remote code execution (RCE) weakness affecting PaperCut MF and PaperCut NG, print management software used by approximately 70,000 organizations in over from 100 countries.
The vulnerability has been actively exploited since at least April 18, 2023about a month after its public disclosure in March.
Although the vulnerability was fixed in versions 20.1.7, 21.2.11 and 22.0.9 of PaperCut NG and MF, companies took time to install the update, which left them exposed to attacks.
Microsoft also reported earlier this week that Iranian hacking groups, including the state-sponsored “Muddywater,” had join the operation of CVE-2023-27350 to bypass user authentication and perform remote execution on their targets.
Unfortunately, the availability of proof-of-concept (PoC) exploits for the PaperCut flaw, some of which are less detectedfurther increases the risk for organizations.
Bl00dy against education
According to CISA, the educational institutions subsector is responsible for approximately 68% of PaperCut servers exposed to the Internet. However, the number of unpatched and therefore vulnerable endpoints is still unknown.
Recently observed Bl00dy ransomware attacks have been successful against some industry targets, leveraging CVE-2023-27350 to bypass user authentication and access the server as administrators.
This access was then used to spawn new ‘cmd.exe’ and ‘powershell.exe’ processes with the same elevated privileges to remotely access the device and use it as a launch pad to spread laterally across the network .
Meanwhile, ransomware actors steal data and encrypt target systems, leaving notes demanding payment in exchange for a working decryptor and promising not to post or sell the stolen data.
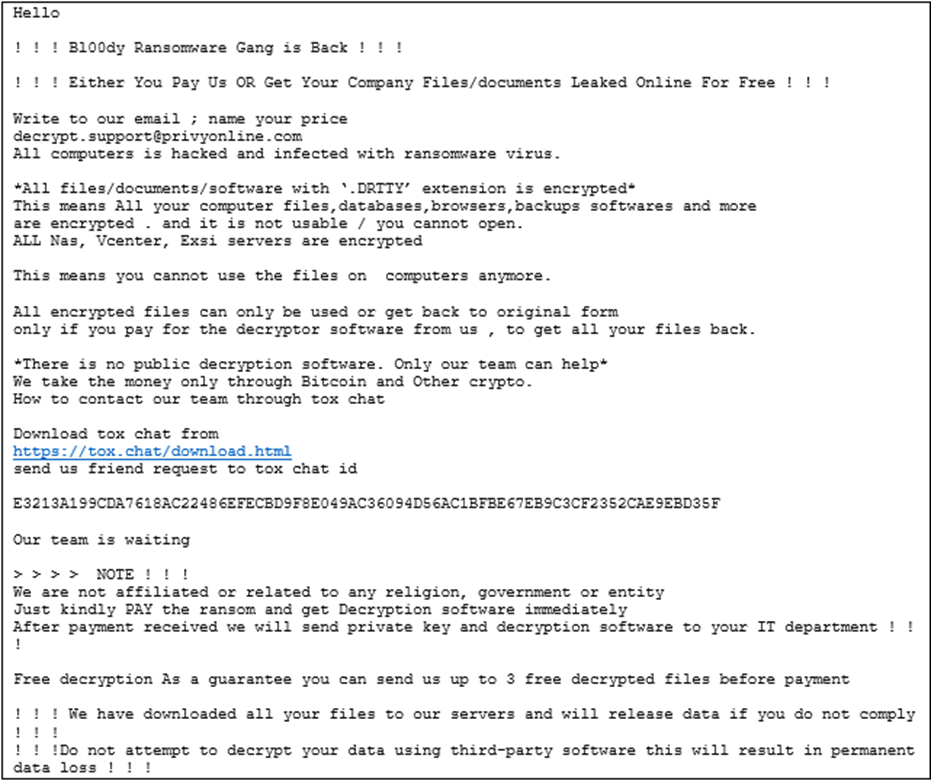
THE How Bl00dy ransomware works launched in May 2022 and uses an encryptor based on the leaked LockBit source code rather than developing their own software.
They have also been seen using ciphers based on leaked source code from Babuk [VirusTotal] and continued [VirusTotal].
The CISA bulletin provides comprehensive details on the signs of exploits left on targeted servers, network traffic signatures, and child processes that need to be monitored to help organizations stop these attacks.
However, the recommended action is always to apply security updates available on PaperCut MF and NG servers, which address all security vulnerabilities exploited by threat actors.
[ad_2]
Source link
