[ad_1]

Cybercriminals are increasingly turning to a new Go-based infostealer named “Aurora” to steal sensitive information from browsers and cryptocurrency apps, exfiltrate data directly from drives, and load additional payloads.
According to the cybersecurity firm SEKOIAat least seven notable cybergangs with significant activity have adopted Aurora exclusively, or along with Redline and Raccoon, two other well-established information-stealing malware families.

Source: SEKOIA
The reason for this sudden rise in Aurora’s popularity is its low detection rate and general unknown status, which makes its infections less likely to be detected.
Simultaneously, Aurora offers advanced data theft functionality and presumably infrastructural and functional stability.
aurora history
Aurora was first announced in April 2022 on Russian-speaking forums, presented as a botnet project with state-of-the-art information theft and remote access features.
As KELA reported earlier this year, the Aurora author was looking to form a small team of testers to make sure the final product is good enough.
However, at the end of August 2022, SEKOIA noticed that Aurora was advertised as a thief, so the project abandoned its goal of creating a multi-tool.
Feature highlights listed in promotional posts are:
- Polymorphic compilation that does not require encryption wrappers
- Server-side data decryption
- Targets over 40 cryptocurrency wallets
- Automatic seed phrase deduction for MetaMask
- Reverse lookup for collecting passwords
- Works on TCP sockets
- Communicate with C2 only once, when verifying the license
- Small fully native payload (4.2 MB) requiring no dependencies
The above features are geared towards high-level stealth, which is Aurora’s main advantage over other popular info stealers.
The rental cost for the malware was set at $250 per month or $1,500 for a lifetime license.
Analysis of thieves
When running, Aurora runs several commands through WMIC to collect basic host information, take a desktop image, and send it to C2.
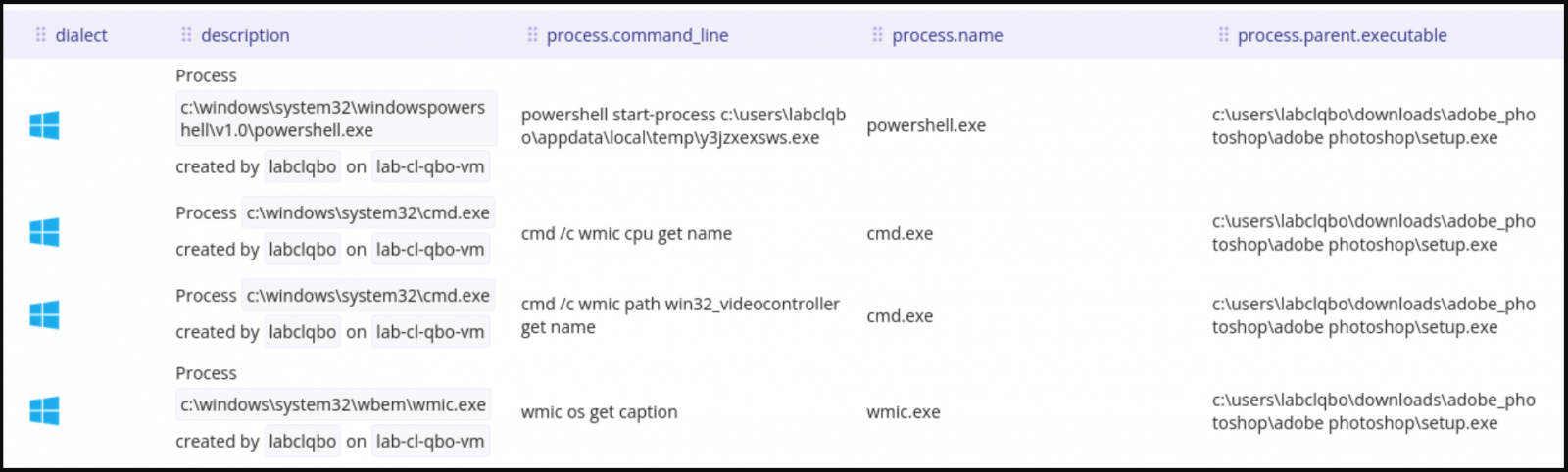
Source: SEKOIA
Next, the malware targets data stored in multiple browsers (cookies, passwords, history, credit cards), cryptocurrency browser extensions, cryptocurrency wallet desktop apps, and Telegram.
Targeted desktop wallet apps include Electrum, Ethereum, Exodus, Zcash, Armory, Bytecoin, Guarda, and Jaxx Liberty.
All stolen data is bundled into a single base64 encoded JSON file and exfiltrated to C2 via TCP ports 8081 or 9865.
SEKOIA reports that they could not confirm the existence of a working file recoverer as promised by the malware author.
However, analysts have observed Aurora’s malware loader using “net_http_Get” to drop a new payload onto the filesystem using a random name and then using PowerShell to execute it.
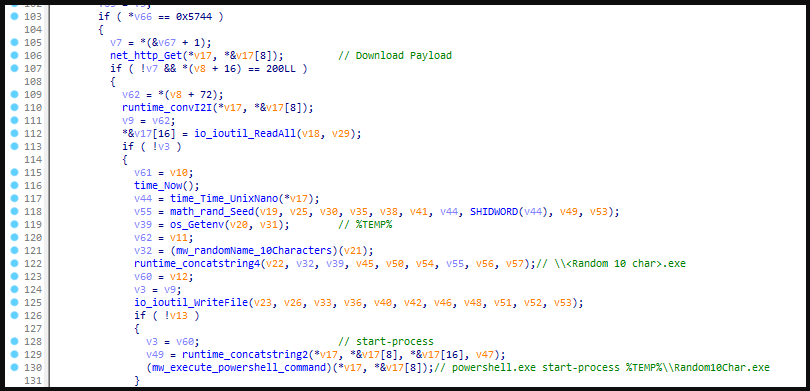
Source: SEKOIA
Current distribution
Currently, Aurora is being distributed to victims through different channels, which is to be expected given the involvement of seven separate operators.
SEKOIA has noticed cryptocurrency phishing sites promoted via phishing emails and YouTube videos that link to fake software and cheat catalog sites.
.png)
Source: BleepingComputer
For a complete list of IoCs (Indicators of Compromise) and sites used for Aurora distribution, see SEKOIA GitHub Repository.
[ad_2]
Source link
