[ad_1]
A hacking group dubbed the “Asylum Ambush” has been seen in recent attacks targeting small and medium businesses around the world, combining cyber espionage and cyber crime.
The particular threat cluster, believed to be operational since at least 2020, was first identified by Proofpoint in a March 2022 Report which focused on a phishing campaign against entities assisting the Movement of Ukrainian refugees.
ESET has published a new report on the actor today, revealing more details about the Asylum Ambush operations from the past year and highlighting updates on his victimology and toolset.
campaign 2023
Asylum Ambuscade typically launches its attacks with spear phishing emails sent to targets, containing malicious document attachments that execute malicious VBS code, and after June 2022, an exploit for CVE-2022-30190 (Follina).
The exploit initiates the download of an MSI installer that deploys the group’s Sunseed malware, a Lua-based downloader that also spawns an LNK file in the Windows startup folder for persistence.
Sunseed obtains the payload for the next stage, Akhbot, from the command and control server and continues to ping the server to receive and execute additional Lua code.
Asylum Ambuscade maintains an almost surprisingly broad targeting reach in 2023, targeting bank customers, cryptocurrency merchants, government entities, and various small and medium businesses in North America, Europe, and Central Asia.
ESET explains that the current infection chain continues to follow the same structure as during operations in 2022. However, security analysts have now noticed new vectors of compromise, including malicious Google ads that redirect users to sites running malicious JavaScript code.
Additionally, the threat actor began rolling out a new tool named “Nodebot” in March 2023, which appears to be the Node.js port of Ahkbot.
Malware functionality continues to include screenshot capture, password exfiltration from Internet Explorer, Firefox, and Chromium-based browsers, and scavenging for additional AutoHotkey plugins on the hacked device.
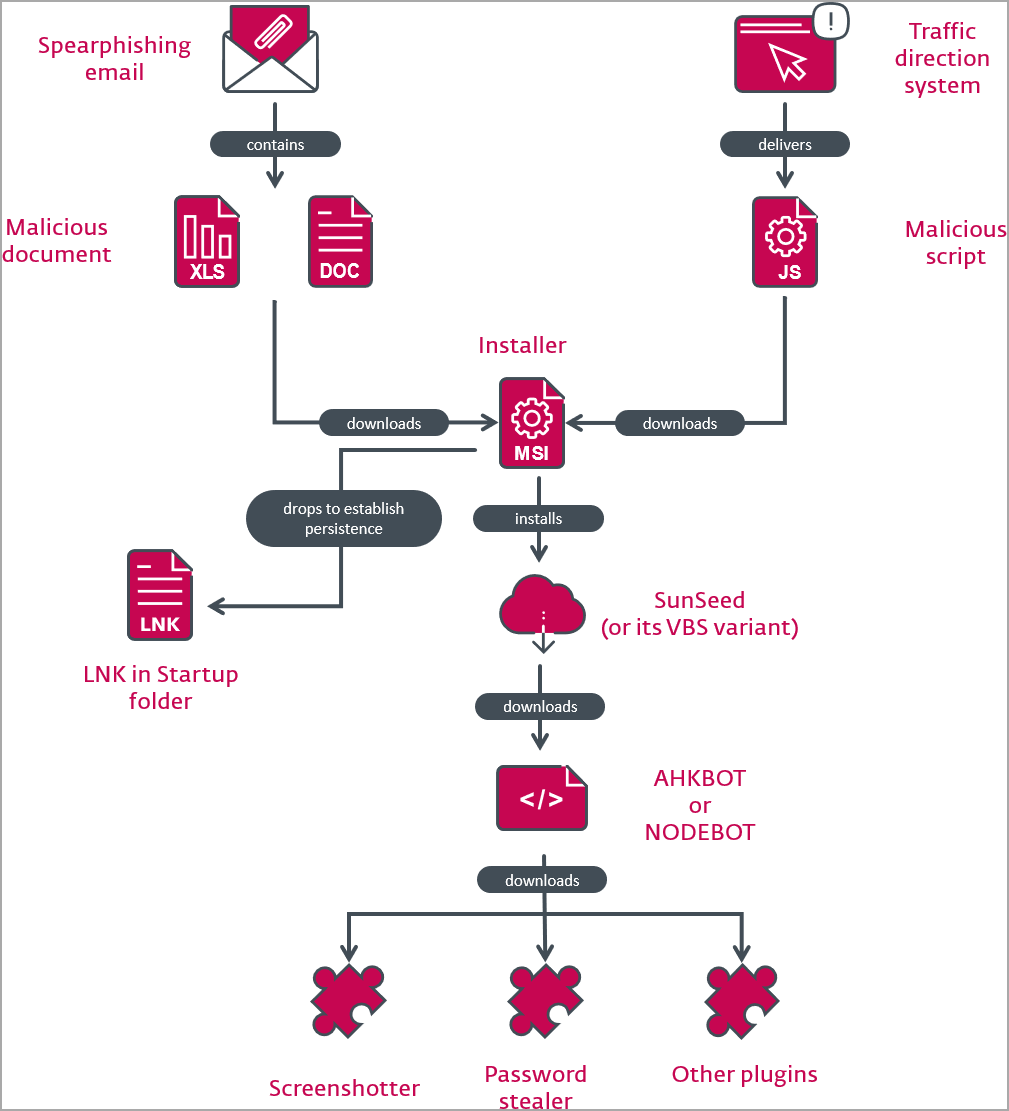
The plugins retrieved by the malware present specific functionality such as downloading a Cobalt Strike VMProtect loader, installing Chrome to support hVNC operations, starting a keylogger, deploying a infostealer Rhadamanthys, the launch of a commercially available RAT, etc.
ESET has counted 4,500 kills since it started tracking Asylum Ambush in January 2022, which equates to around 265 kills/month, making it a very prolific player and a serious threat to organizations around the world.
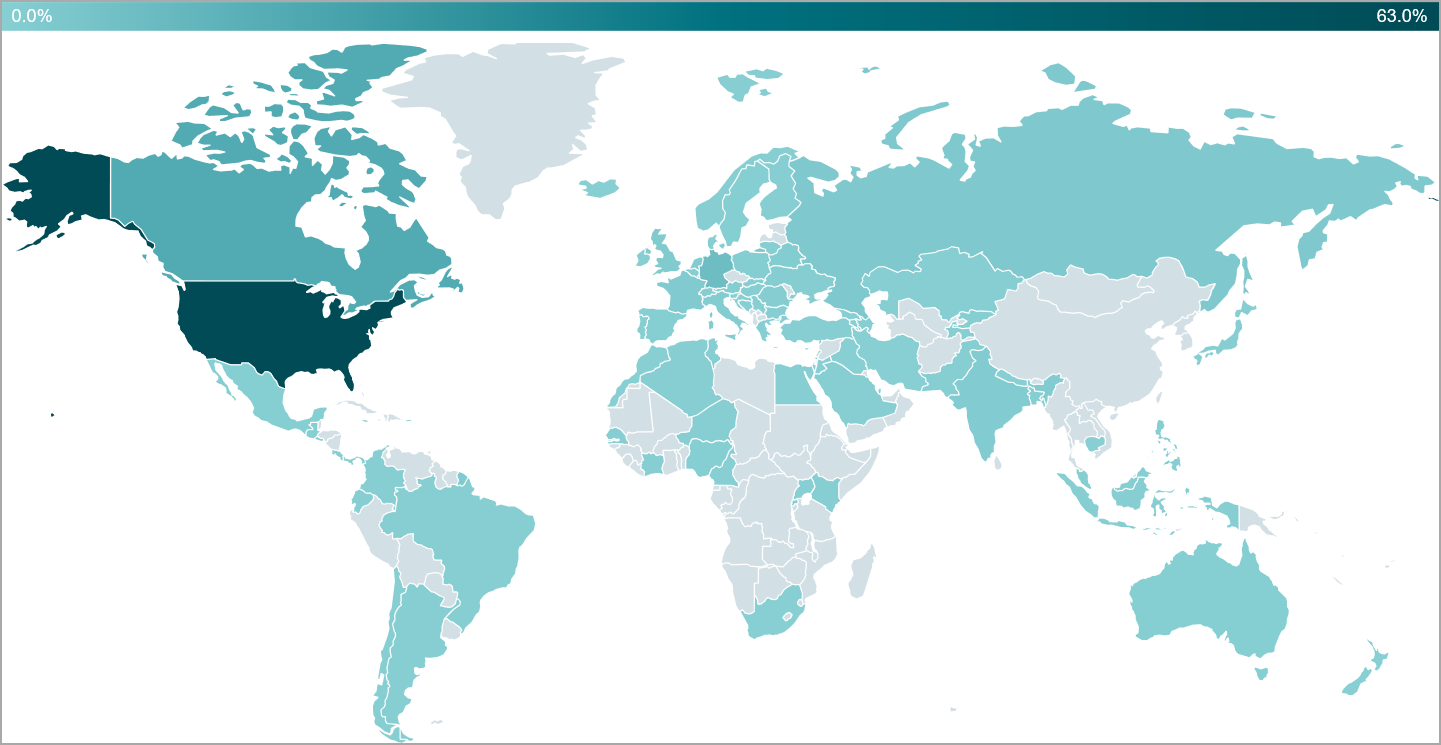
While threat actors are clearly targeting cryptocurrency traders and bank accounts for profit, compromising SMB entities could indicate cyber espionage.
The threat group may sell access to these companies’ network to ransomware affiliates for profit. However, ESET found no evidence to support this assumption.
In conclusion, the specific operational objectives of Asylum Ambuscade remain unclear.
[ad_2]
Source link
