[ad_1]

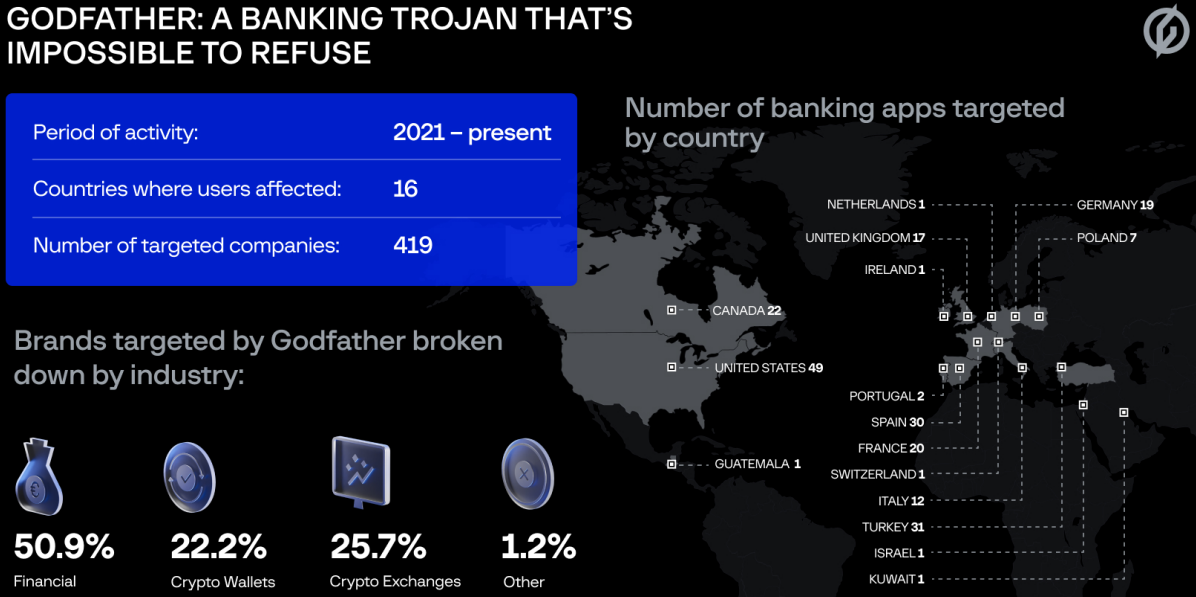
An Android banking malware codenamed “Godfather” is targeting users in 16 countries, attempting to steal account credentials for more than 400 online banking sites and cryptocurrency exchanges.
The malware generates login screens overlaid on banking and crypto exchange app login forms when victims attempt to log into the site, tricking the user into entering their credentials on well-designed HTML phishing pages .
The Godfather Trojan was discovered by Group-IB analysts, who believe it is the successor to Anubis, a once widely used banking Trojan that has gradually fallen into disuse due to its inability to circumvent new Android defenses.
ThreatFabric first discovered Godfather in March 2021, but it has undergone massive upgrades and code improvements since then.
As well, Cyble published a report yesterday highlighting an increase in Godfather activity, pushing an app that mimics a popular music tool in Turkey, downloaded 10 million times via Google Play.
Target banks around the world
Group-IB discovered limited distribution of the malware in Google Play Store apps; however, the main distribution channels have not been discovered, so the initial infection method is largely unknown.
Nearly half of all apps targeted by Godfather, 215, are banking apps, and most of them are in the US (49), Turkey (31), Spain (30), Canada (22), France (20), Germany (19) and the United Kingdom (17).
Besides banking apps, Godfather is targeting 110 cryptocurrency exchange platforms and 94 cryptocurrency wallet apps.
Interestingly, the Trojan is configured to check the system language, and if it is set to Russian, Azerbaijani, Armenian, Belarusian, Kazakh, Kyrgyz, Moldovan, Uzbek, or Tajik, it stops working.
This is a strong indication that the authors of Godfather are Russian speakers, possibly residing in the CIS (Commonwealth of Independent States) region.
The Godfather
Once installed on the device, Godfather mimics “Google Protect”, a standard security tool found on all Android devices. The malware even goes so far as to emulate a scanning action on the device.
The purpose of this scan is to request access to the accessibility service from what appears to be a legitimate tool. Once the victim approves the request, the malware can issue itself all the permissions it needs to perform malicious behavior.
This includes access to SMS and notifications, screen recording, contacts, calls, writing to external storage, and reading device status.
Additionally, the accessibility service is abused to prevent the user from removing the trojan, exfiltrating Google Authenticator OTPs (one-time passwords), fulfilling orders, and stealing field content PIN code and password.
Godfather exfiltrates a list of installed applications to receive corresponding injections (fake HTML login forms to steal credentials) from the C2 server.
The malware can also generate fake notifications from apps installed on the victim’s device to direct the victim to a phishing page, so they don’t have to wait for the target app to open .
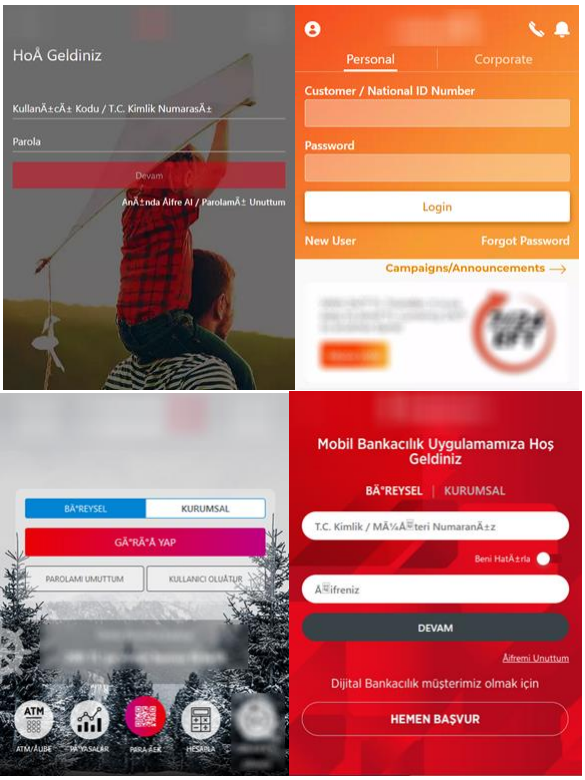
For apps not listed, Godfather can use its screen recording features to capture the credentials entered by the victim in the fields.
Additionally, the malware also accepts the following commands from C2, which it executes with administrator privileges on the device:
- startUSSD – Executes a USSD request
- sentSMS – Send SMS from an infected device (not addressed in later malware versions)
- startApp – Launch a C2-defined application
- cahcecleaner – Clear application cache for any application determined by C2
- BookSMS – Send SMS to all contacts. Probably used for propagation. Not implemented in the latest version.
- startforward/stopforward – Activate/deactivate call forwarding to a number specified by the C2
- openbrowser – open an arbitrary webpage
- startsocks5/stopsocks5 – Enable/disable a SOCKS5 proxy
- killbot – Self-removal
- startPush – Show push notifications which, when clicked, open a web page with a fake (phishing) page.
Apart from the above, the Trojan has modules that allow it to perform actions such as keylogging, launching a VNC server, screen recording, screen lock , exfiltrating and blocking notifications, enabling silent mode, establishing a WebSocket connection, and dimming the screen. .
Login to Anubis
The Anubis source code was leaked in 2019, so Godfather could be either a new project by the same authors or new malware created by a new threat group.
The similarities extend to the method of receiving the C2 address, the processing and implementation of C2 commands, the Web Fakes module, the proxy module and the screenshot module.
Godfather omitted the inclusion of Anubis’ file encryption, audio recording, and GPS tracking modules, but added a VNC module, implemented a new communication protocol and traffic encryption algorithm, and added a system for stealing Google Authenticator codes.
Overall, Godfather is a dangerous and feature-rich trojan built on proven Anubis malware code, targeting a long list of Android apps and users around the world.
To protect against this threat, only download apps from Google Play, keep your device updated, use an AV tool, make sure Play Protect is active, and keep the number of installed apps to a minimum.
[ad_2]
Source link
