[ad_1]

A new collection of malicious Android apps posing as harmless file managers had infiltrated the official Google Play app store, infecting users with the Sharkbot banking trojan.
Apps do not carry the malicious payload upon installation to evade detection when submitted to Google Play, but later fetch it from a remote resource.
Since Trojan apps are file managers, it is less likely to arouse suspicion when asking for dangerous permissions to load Sharkbot malware.
Fake file managers infect Android
Sharkbot is dangerous malware that attempts to steal online bank accounts by displaying fake login forms above legitimate login prompts in banking apps. When a user attempts to log into their bank using one of these fake forms, credentials are stolen and sent to threat actors.
The malware is constantly evolving, appearing on the Play Store below various disguises Where loaded from trojan applications.
In a new report from Bitdefender, analysts discovered the new Android Trojan apps disguised as file managers and reported them to Google. All have since been removed from the Google Play Store.
However, many users who downloaded them previously may still have them installed on their phones or may still be suffering from undiscovered malware infections.
The first malicious application is “X-File Manager” from Victor Soft Ice LLC (com.victorsoftice.llc), downloaded 10,000 times via Google Play before Google finally removed it.
The app performs anti-emulation checks to evade detection and will only load Sharkbot on UK or Italian SIM cards, so it is part of a targeted campaign.
The list of mobile banking apps targeted by the malware is shown below, but as Bitdefender notes, threat actors can update this list remotely at any time.
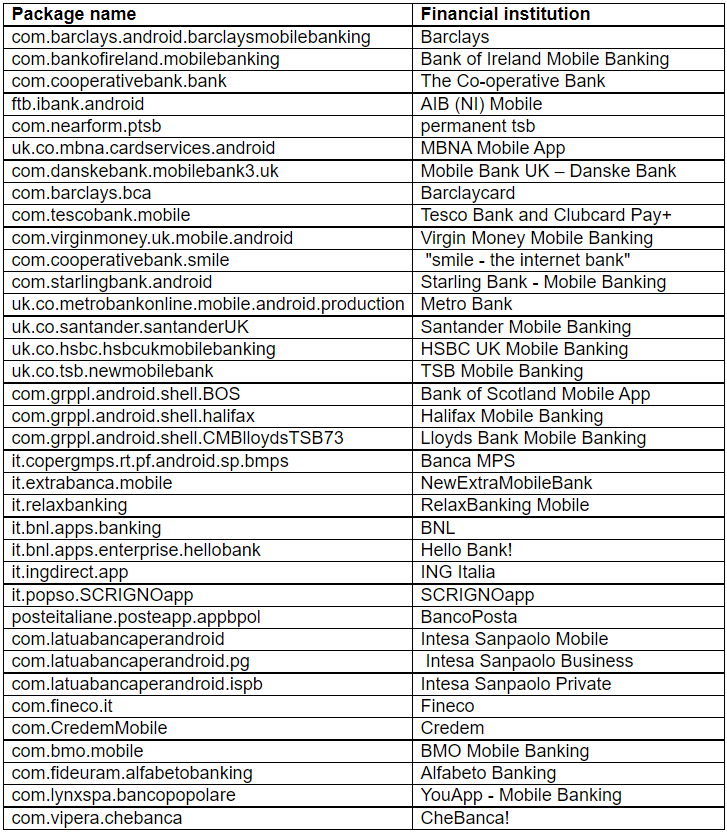
Bitdefender’s telemetry data reflects the narrow targeting of this campaign, as most of the victims of the particular Sharkbot distribution wave are in the UK, followed by Italy, Iran, and Germany.
The rogue app asks the user to grant risky permissions such as reading and writing external storage, installing new packages, accessing account details, deleting packages (for erasing traces), etc.
However, these permissions seem normal and expected in the context of file management apps, so users are less likely to treat the request with caution.
Sharkbot is recovered as a fake program update, which X-File Manager prompts the user to approve before installation.
The second malicious application that installs the banking Trojan is “FileVoyager” from Julia Soft Io LLC (com.potsepko9.FileManagerApp), downloaded 5,000 times via Google Play.
FileVoyager features the same operating model as X-File Manager and targets the same financial institutions in Italy and the UK.
Another Sharkbot loading app spotted by Bitdefender is “LiteCleaner M” (com.ltdevelopergroups.litecleaner.m), which amassed 1,000 downloads before being spotted and removed from the Play Store.
Currently, this app is only available through third-party app stores like APKSOS. The same third-party app store hosts a fourth Sharkbot loader named “Phone AID, Cleaner, Booster 2.6” (om.sidalistudio.developer.app).
If these apps are installed, Android users should remove them immediately and change the passwords of all online banking accounts they use.
As threat actors distributed these apps directly from Google Play, the best way to protect yourself is to keep the Play Protect service enabled so that malicious apps are removed as soon as they are detected.
Additionally, an Android mobile security antivirus app would help detect malicious traffic and apps, even before they are reported to Google Play.
[ad_2]
Source link
