[ad_1]

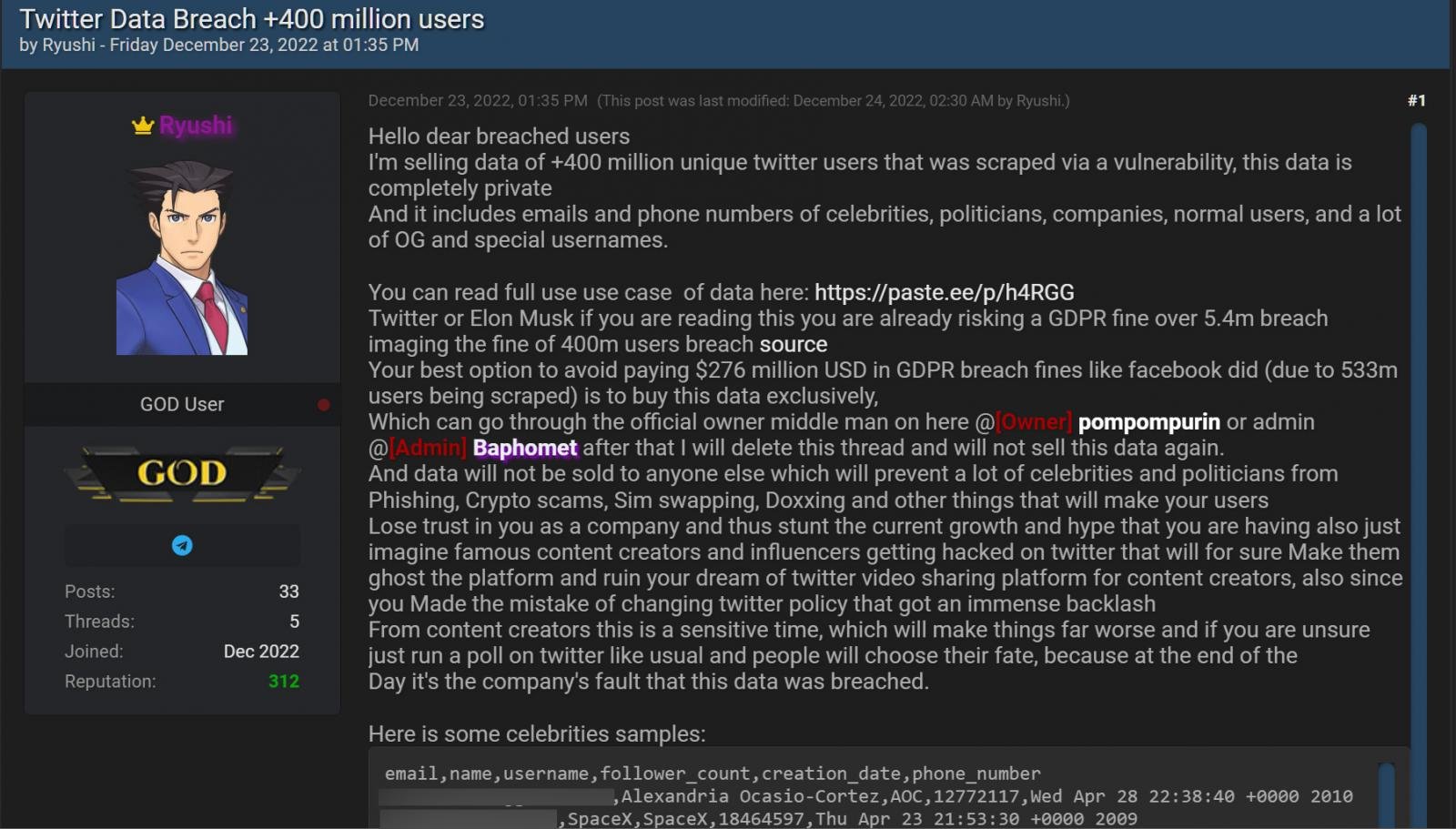
A threat actor claims to sell the public and private data of 400 million Twitter users recovered in 2021 using a now patched API vulnerability. They’re asking for $200,000 for an exclusive sale.
The alleged data dump is being sold by a malicious actor named “Ryushi” on the Breached hacking forum, a site commonly used to sell user data stolen during data breaches.
The threat actor claimed to have harvested data from over 400 million unique Twitter users using a vulnerability. They warned Elon Musk and Twitter that they would have to buy the data before it resulted in a hefty fine under EU GDPR privacy law.
“Twitter or Elon Musk, if you’re reading this you already risk a GDPR fine of over 5.4 million violations, imagining the fine of 400 million violating users,” Ryushi wrote in a post on the forum.
“Your best option to avoid paying $276 million in fines for GDPR violations like Facebook did (due to 533 million deleted users) is to buy that data exclusively.”
Source: BleepingComputer
The threat actor also linked to a position explaining how this data could be exploited by other threat actors for phishing attacks, cryptographic scams and BEC attacks.
The forum post includes sample data for thirty-seven celebrities, politicians, journalists, businesses and government agencies, including Alexandria Ocasio-Cortez, Donald Trump JR, Mark Cuba, Kevin O’Leary and Piers Morgan. Additionally, a larger sample of 1,000 Twitter user profiles was later leaked.
User profiles contain public and private Twitter data, including users’ email addresses, names, usernames, number of followers, creation date, and phone numbers. Although all of the leaked profiles appear to have associated email addresses, many do not have phone numbers.
While almost all of this data is publicly available to any Twitter user, phone numbers and email addresses are private information.
Threat actor Ryushi told BleepingComputer that they were trying to sell the Twitter data exclusively to one person/Twitter for $200,000 and would then delete the data. If an exclusive purchase is not made, they will sell copies to multiple people for $60,000 per sale.
When asked if they had contacted Twitter to redeem the data, they told BleepingComputer that they had contacted Twitter and made calls but received no response.
Data collected using API vulnerability now patched
The threat actor confirmed to BleepingComputer that he harvested private phone numbers and email addresses using an API vulnerability that Twitter patched in January 2022 and was previously associated with a 5.4 million user data breaches.
The vulnerability allowed a person to feed large lists of phone numbers and email addresses into a Twitter API and receive an associated Twitter user ID. The threat actor then used this ID along with another IP address to retrieve users’ public profile data, creating a Twitter user profile consisting of public and private data.
“I previously had access to the same exploit used for the 5.4 million data leak. I spoke with the vendor and he confirmed it was in the Twitter login stream,” the actor said. of threat to BleepingComputer.
“So when checking for duplicate, it leaked user ID which I converted using another API to username and other info.”
Although Twitter patched the vulnerability in January 2022, it has now been confirmed to have been used by multiple threat actors to extract private information from Twitter users.
Regarding this new leak, BleepingComputer could not confirm that two of the leaked Twitter profiles are valid.
However, Alon Gal of threat intelligence firm Hudson Rock said he had independently verified that the leaked samples appeared legitimate.
“Please note: at this stage it is not possible to fully verify that there are indeed 400,000,000 users in the database.” tweeted Hudson Rock.
“Based on independent verification, the data itself appears to be legitimate and we will monitor any developments.”
This leak of Twitter user data comes at a bad time for the social media company, as an EU privacy watchdog, the Irish Data Protection Commission (DPC), has said. started an investigation in the recent publication of the 5.4 million user records stolen in 2021 using this vulnerability.
Another malicious actor claimed to have also used this vulnerability to scrape data of 17 million alleged users. However, this leak is still private and not being sold.
BleepingComputer contacted Twitter with further questions regarding the sale of this data, but a response was not immediately available.
[ad_2]
Source link
