[ad_1]

This week’s reports illustrate how threat actors view Microsoft Exchange as a prime target to gain initial access to corporate networks to steal data and deploy ransomware.
CrowdStrike researchers reported this week that the Play ransomware operation used a new Microsoft Exchange attack dubbed “OWASSRF” which chained exploits for CVE-2022-41082 and CVE-2022-41080 to gain initial access to corporate networks.
The ransomware operation then used this access to steal data and encrypt devices on the network.
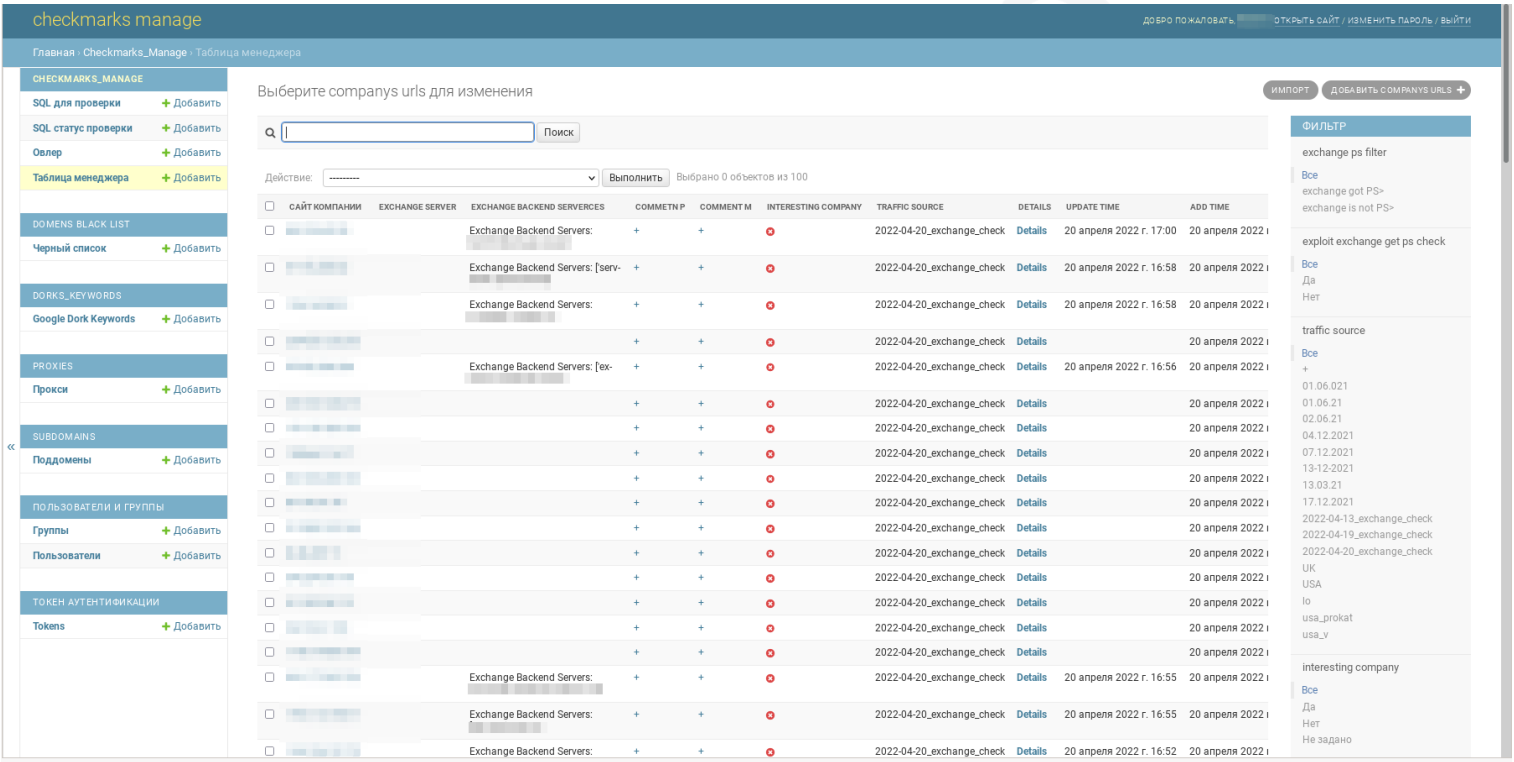
As another example of Microsoft Exchange heavily targeted by threat actors, ProDaft revealed this week that the Hacking group FIN7 has created an auto-attack platform called ‘Checkmarks’ which targets Microsoft Exchange.
This platform automatically scans Exchange servers, exploits vulnerabilities to access them, and then downloads data from the server.
FIN7 would then assess the company to determine if it was valuable enough to deploy ransomware.
Source: Pro Daft
TrendMicro also confirmed this week our September report that a Conti cell known as Zeon rebranded as Royal Ransomware.
Other reports this week highlighted various ransomware operations:
Contributors and those who provided new ransomware information and stories this week include: @BleepinComputer, @FourBytes, @billtoulas, @DanielGallagher, @demonslay335, @struppigel, @jorntvdw, @LawrenceAbrams, @malwhunterteam, @VK_Intel, @PolarToffee, @fwosar, @Ionut_Ilascu, @Seifreed, @malwareforme, @serghei, @IBMSecurity, @PRODAFT, @CrowdStrike, @LabsSentinel, @Fortinet, @zscaler, @TrendMicroand @pcrisk.
December 19, 2022
Play ransomware claims attack on German hotel chain H-Hotels
The Play ransomware gang has claimed responsibility for a cyberattack on H-Hotels (h-hotels.com) that resulted in communication outages for the company.
How Reveton Ransomware-as-a-Service Changed Cybersecurity
In 2012, Reveton ransomware appeared. It is believed to be the first ever Ransomware-as-a-Service (RaaS) operation. Since then, RaaS has enabled gangs with basic technical skills to launch indiscriminate attacks. Today, almost anyone can create highly effective malware campaigns.
December 20, 2022
Ransomware gang uses new Microsoft Exchange exploit to breach servers
Play ransomware threat actors are using a new exploit chain that bypasses ProxyNotShell URL rewrite mitigations to achieve Remote Code Execution (RCE) on vulnerable servers through Outlook Web Access (OWA ).
Nokoyawa Ransomware: Rust or Collapse
The Nokoyawa ransomware was discovered in February 2022, sharing code with another ransomware family known as Karma. The lineage of Nokoyawa ransomware can further be traced back to Nemty ransomware. Original version of Nokoyawa ransomware was written in C programming language and file encryption used asymmetric elliptic curve cryptography (ECC) with SECT233R1 (aka NIST B-233) curve using open library Tiny-ECDH source combined with one Salsa20 symmetric key per file. . Nokoyawa ransomware 2.0 still uses Salsa20 for symmetric encryption, but the elliptical curve has been replaced by Curve25519.
New STOP ransomware variants
Risk found new STOP ransomware variants that add the .isal or .isza expansions.
December 21, 2022
Conti Team One Splinter Group resurfaces as Royal Ransomware with callback phishing attacks
Royal ransomware may have first been observed by researchers around September 2022, but it got the cyber criminals behind it: dubbed it Zeon ransomware, until they renamed it Royal ransomware.
New HardBit 2.0 ransomware
PCrisk found HardBit 2.0 ransomware which adds the .hardbit2 extension and removes ransom notes named How to restore your .txt files.
New variant of STOP ransomware
PCrisk has found a new STOP ransomware variant that adds the .iswr extension.
December 22, 2022
Vice Society ransomware group moves to new custom encryptor
The Vice Society ransomware operation switched to using custom ransomware encryption that implements a strong hybrid encryption scheme based on NTRUEncrypt and ChaCha20-Poly1305.
FIN7 Hackers Create Auto-Attack Platform to Breach Exchange Servers
Notorious hacking group FIN7 uses an automated attack system that exploits Microsoft Exchange and SQL injection vulnerabilities to breach corporate networks, steal data, and select targets for ransomware attacks based on financial size .
Ransomware Roundup – Play Ransomware
Play is a relative newcomer to ransomware gaming, having first been detected in June 2022. In this report, Play refers to both the group that develops and distributes it and the name of the ransomware executable. Like many other carriers in this space, Play has adopted the double extortion methodology of encrypting endpoints and/or other valuable infrastructure within an organization and then threatening to leak data exfiltrated from those machines on the Internet if a ransom is not paid.
It’s all for this week ! Hope everyone is having a great holiday and we will be back after the new year!
[ad_2]
Source link
