[ad_1]

New information-stealing malware named “RisePro” is being distributed via fake crack sites operated by PrivateLoader pay-per-install (PUP) malware distribution service.
RisePro is designed to help attackers steal victims’ credit cards, passwords, and crypto wallets from infected devices.
The malware was spotted by analysts at Breaking point and Sekoia this week, the two cybersecurity companies confirming that RisePro is a previously undocumented information stealer, now distributed via fake software cracks and key generators.
Flashpoint reports that threat actors have already started selling thousands of RisePro logs (packets of data stolen from infected devices) on Russian dark web markets.
Additionally, Sekoia discovered numerous code similarities between PrivateLoader and RisePro, indicating that the malware distribution platform is likely now releasing its own infostealer, either for itself or as a service.
Currently, RisePro is available for purchase through Telegram, where users can also interact with the developer and infected hosts (Telegram bot).
RisePro Details and Capabilities
RisePro is C++ malware that Flashpoint claims may be based on the Vidar password-stealing malware, as it uses the same system of built-in DLL dependencies.
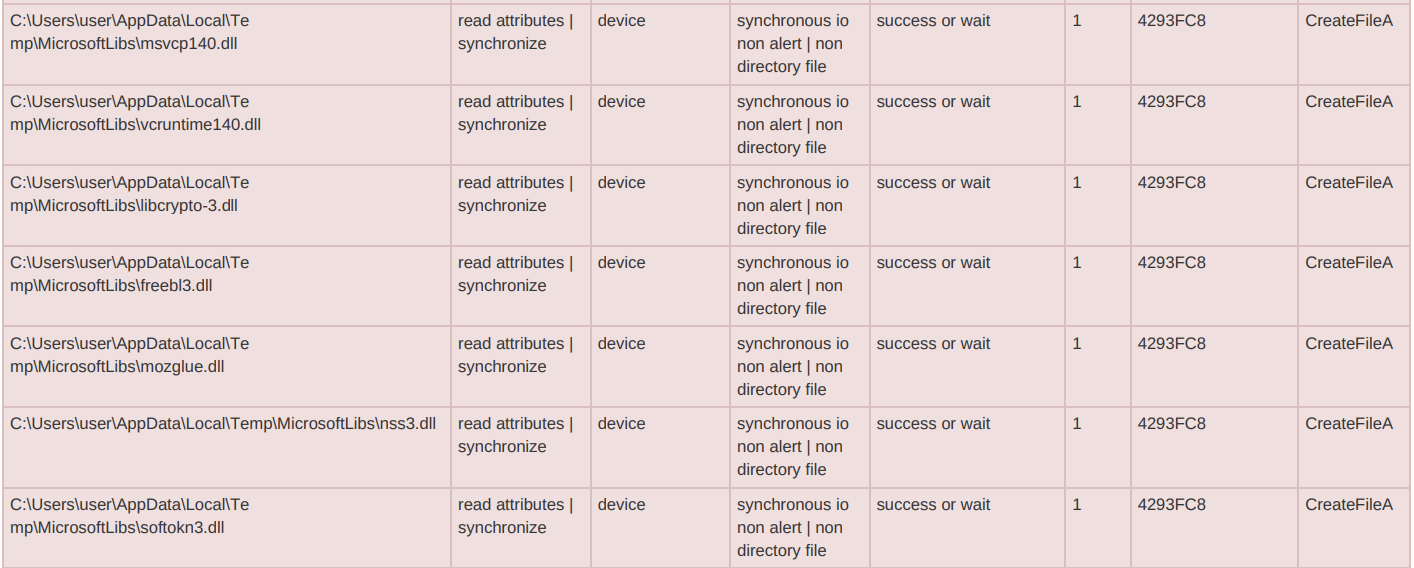
Sekoia further explains that some RisePro samples embed the DLLs, while in others the malware fetches them from the C2 server via POST requests.
The information thief first fingerprints the compromised system by examining the registry keys, writes the stolen data to a text file, takes a screenshot, packs it all into a ZIP archive, then sends the file to the attacker’s server.
RisePro attempts to steal a wide variety of data from apps, browsers, crypto wallets, and browser extensions, as listed below:
- Web browsers: Google Chrome, Firefox, Maxthon3, K-Melon, Sputnik, Nichrome, Uran, Chromodo, Netbox, Comodo, Torch, Orbitum, QIP Surf, Coowon, CatalinaGroup Citrio, Chromium, Elements, Vivaldi, Chedot, CentBrowser, 7start, ChomePlus, Iridium, Amigo, Opera, Brave, CryptoTab, Yandex, IceDragon, BlackHaw, Pale Moon, Atom.
- Browser extensions: Authenticator, MetaMask, Jaxx Liberty Extension, iWallet, BitAppWallet, SaturnWallet, GuildWallet, MewCx, Wombat, CloverWallet, NeoLine, RoninWallet, LiqualityWallet, EQUALWallet, Guarda, Coinbase, MathWallet, NiftyWallet, Yoroi, BinanceChainWallet, TronLink, Phantom, Oxygen, PaliWallet , PaliWallet, Bolt X, ForboleX, XDEFI Wallet, Maiar DeFi Wallet.
- Software: Discord, battle.net, AuthyDesktop.
- Cryptocurrency assets: Bitcoin, Dogecoin, Anoncoin, BBQCoin, BBQCoin, DashCore, Florincoin, Franko, Freicoin, GoldCoin (GLD), IOCoin, Infinitecoin, Ixcoin, Megacoin, Mincoin, Namecoin, Primecoin, Terracoin, YACoin, Zcash, devcoin, digitalcoin, Litecoin, Redcoin.
In addition to the above, RisePro can scan file system folders for interesting data such as receipts containing credit card information.
Link to PrivateLoader
PrivateLoader is a pay-per-install malware distribution service disguised as software cracks, key generators, and game mods.
Threat authors provide the sample of malware they wish to distribute, targeting criteria, and payment to the PrivateLoader team, which then uses its network of counterfeit and hacked websites to distribute malware.
The service was first spotted by Intel471 in February 2022, while in May 2022, Trend Micro observed PrivateLoader pushing a new Remote Access Trojan (RAT) named ‘NetDooka.’
Until recently, PrivateLoader almost exclusively distributed RedLine or Raccoon, two popular information stealers.
With the addition of RisePro, Sekoia now reports finding loading capabilities in the new malware, also pointing out that this part of its code has a lot of overlap with that of PrivateLoader.
Similarities include string obfuscation technique, HTTP message obfuscation, and HTTP and port configuration.
.png)
A likely scenario is that the same people behind PrivateLoader developed RisePro.
Another hypothesis is that RisePro is the evolution of PrivateLoader or the creation of a dishonest former developer who now promotes a similar PUP service.
Based on the evidence collected, Sekoia could not determine the exact connection between the two projects.
[ad_2]
Source link
