[ad_1]

A new malware-as-a-service (MaaS) operation named “DuckLogs” has emerged, giving low-skilled attackers easy access to several modules to steal information, log keystrokes, access clipboard data and remotely access the compromised host.
DuckLogs is completely web-based. It claims that thousands of cyber criminals pay a subscription to generate and launch more than 4000 versions of malware.
Operators seem to provide additional services to some clients, helping them distribute the payload, a tool to drop files and an extension changer.
The web panel shows that more than 2,000 cybercriminals are using the malicious platform and the current number of victims is over 6,000.
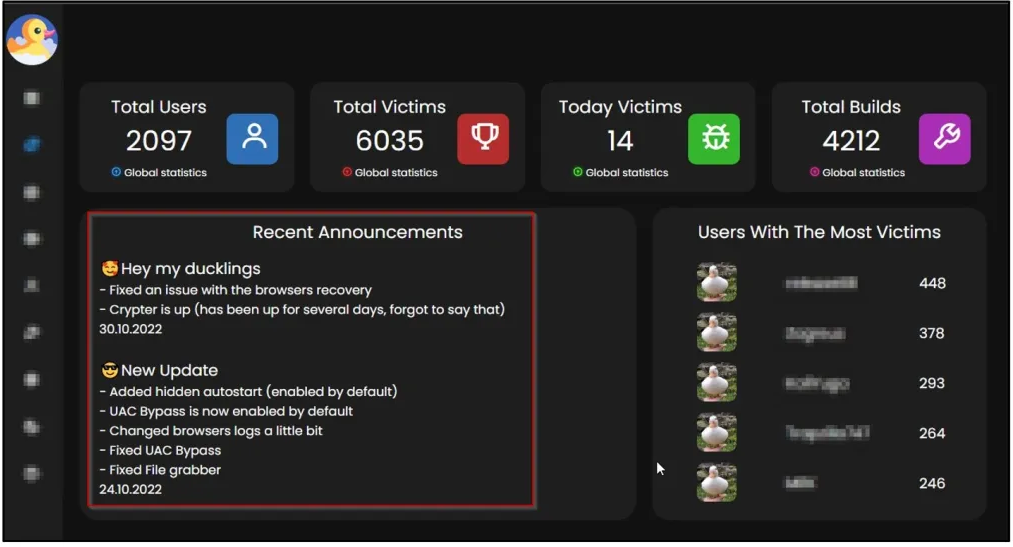
Cyble malware researchers detected DuckLogs malware and released a technical analysis of their discoveries.
Features of DuckLogs
DuckLogs primarily includes an information stealer and a Remote Access Trojan (RAT) component, but it contains over 100 individual modules that target specific applications.
Below is a list of some of the data and applications targeted by the information theft component:
- Hardware and software information
- Files stored on local drives
- Account identifiers and cookies stored in web browsers
- Thunderbird and Outlook emails
- Discord, Telegram, Signal and Skype messaging data
- NordVPN, ProtonVPN, OpenVPN and CrypticVPN Account Data
- FileZilla and TotalCommander data
- Steam, Minecraft, Battle.Net and Uplay accounts
- Metamask, Exodus, Coinomi, Atomic and Electrum cryptocurrency wallets
The RAT component supports functions that retrieve files from the command and control (C2) server and run them on the host, show a crash screen, shut down, restart, sign out or lock the device, or open URLs in the browser.
Other DuckLogs modules provide logging of keystrokes to steal sensitive information, a clipper (typically used to hijack cryptocurrency transactions), and a tool for taking screenshots.
Cyble researchers claim that the malware also supports Telegram notifications, encrypted logs and communications, code obfuscation, process mining to launch payloads in memory, persistence mechanism and workaround for Windows User Account Control.
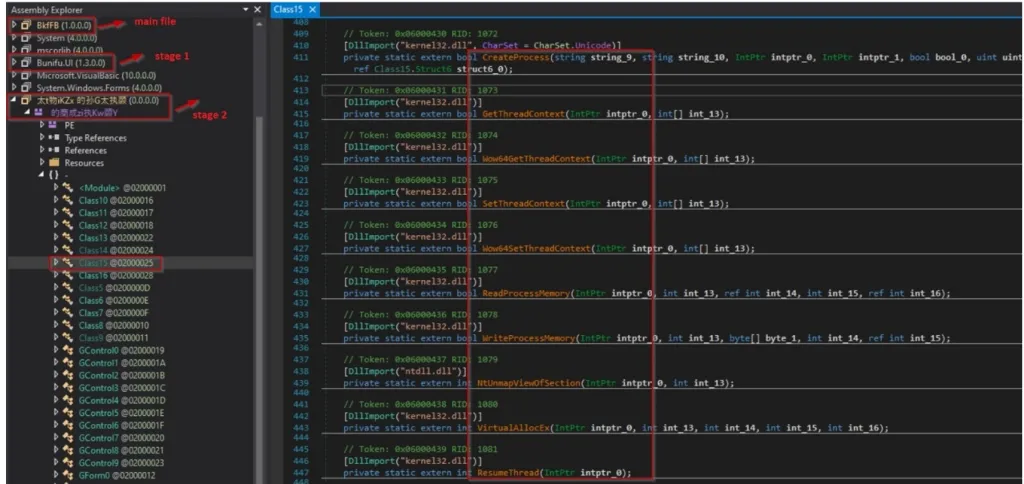
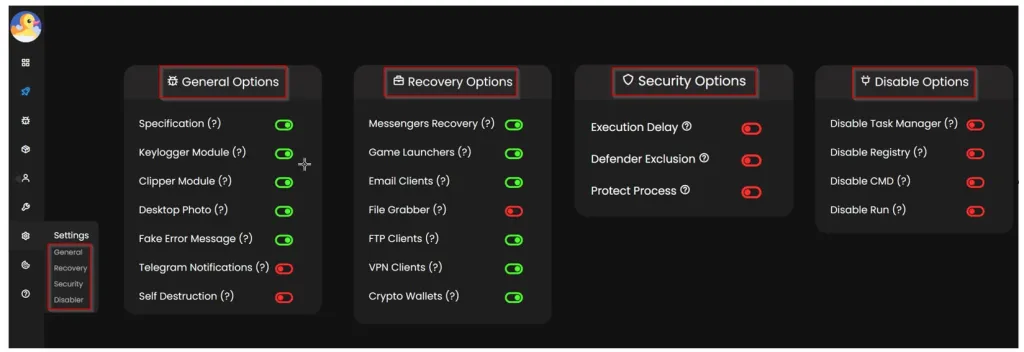
The web panel is currently available on four clearnet domains and appears to provide powerful payload creation functionality with options for modules and functions to add to the final version of the malware.
Additionally, the builder offers anti-evasion choices, such as adding an exclusion for Windows Defender, a payload execution timeout, or disabling task manager on the host.
Cyble says the initial infection vector is likely to be via email (spam, phishing). Researchers recommend users to verify the authenticity of suspicious messages and not to open links from untrusted sources.
Additionally, sensitive data copied to the clipboard should be carefully inspected after pasting it to ensure that hackers have not altered details such as the destination of a transaction.
Another useful precaution is to avoid downloading executables from torrents or shady sites, and to keep security software up to date.
[ad_2]
Source link
