[ad_1]

An 8Base ransomware gang is targeting organizations around the world in double extortion attacks, with a steady stream of new victims since early June.
The ransomware gang first emerged in March 2022, remaining relatively quiet with few notable attacks.
However, in June 2023, the ransomware operation saw a spike in activity, targeting numerous companies from various industries and carrying out double extortion.
So far, 8Base has listed 35 victims on its dark web extortion site, with some days claiming up to six victims at a time.
This is a notable increase from March and April, when the group only listed a handful of victims, as seen in the graph below.
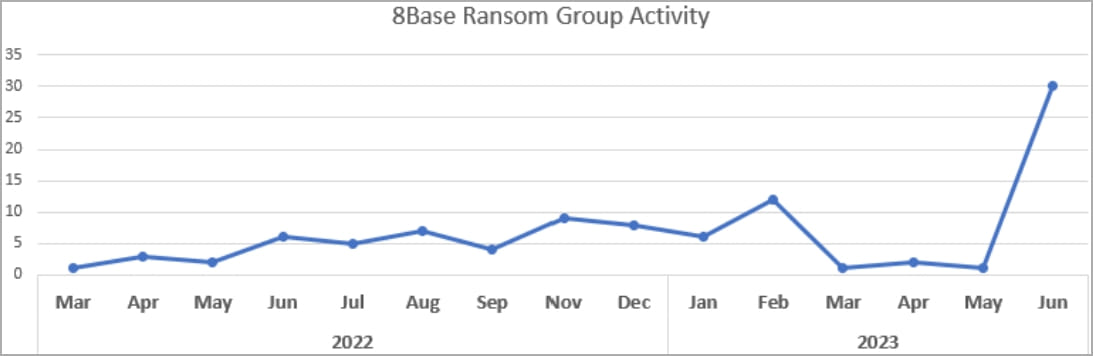
The gang’s data leak site launched in May 2023with the extortion gang claiming to be “honest and simple” pentesters.
“We are honest, straightforward pentesters. We offer businesses the most loyal terms for returning their data,” reads their data leak site.
“This list only contains companies that have overlooked the privacy and importance of their employee and customer data.”

Source: BleepingComputer
Links to other ransomware groups
In a new report by VMware’s Carbon Black team, the tactics seen in recent 8Base attacks indicate that this is a rebranding of a well-established ransomware organization, potentially RansomHouse.
RansomHouse is an extortion group that claims not to carry out encryption attacks, but instead partners with ransomware operations to sell their data. However, BleepingComputer is aware of threat actors use of ransomware in attackslike White Rabbit or MARIO, which has also been linked to the FIN8 cybercrime group.
VMware suspects that 8Base is an offshoot of RansomHouse based on the identical ransom notes used by both groups and the very similar language and content seen on the respective leak sites, where even the FAQ pages appear to have been cut and pasted.
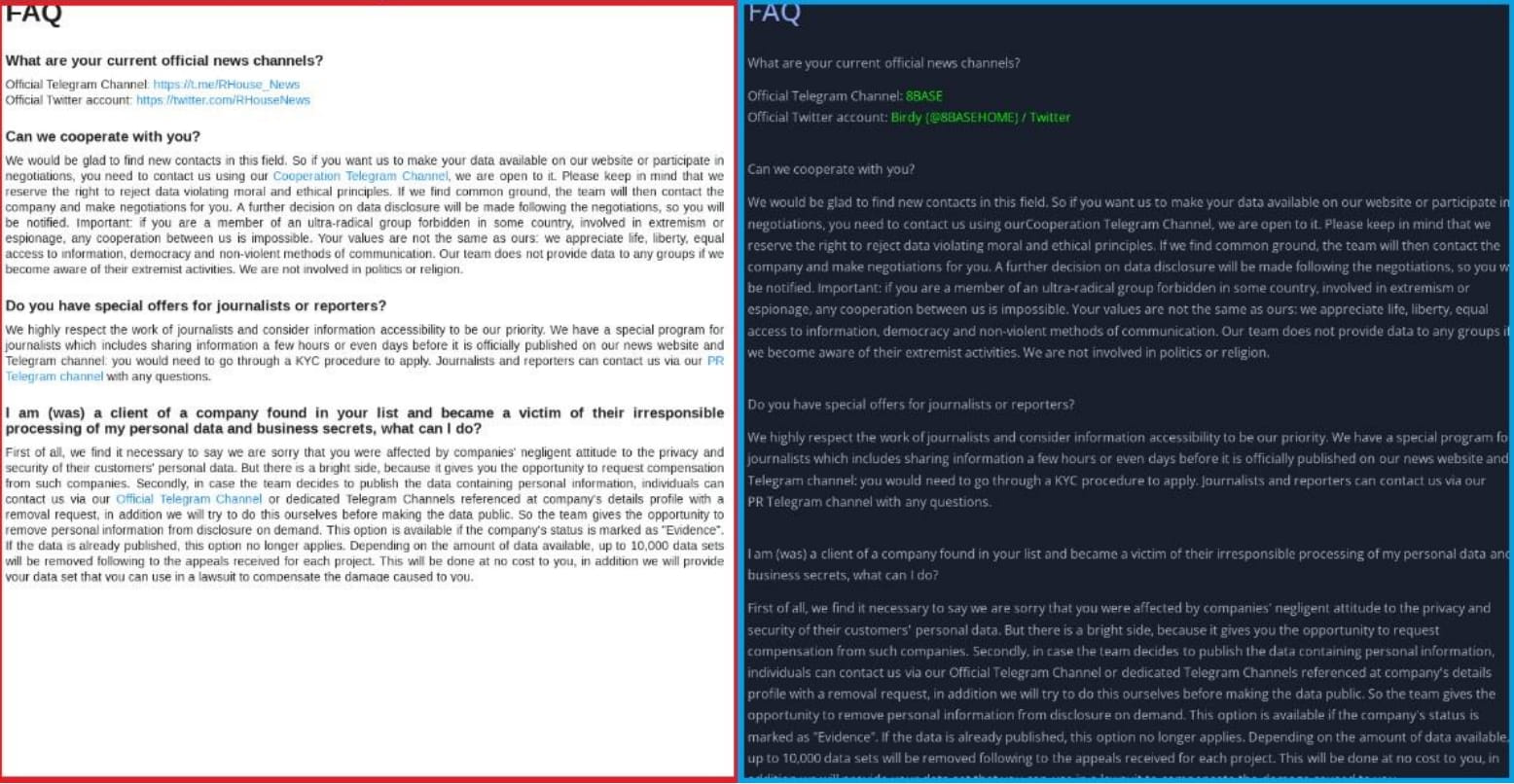
However, there is not enough evidence to determine whether 8Base was spawned by members of RansomHouse or just another ransomware operation copying patterns from an established group, which is not uncommon to see among threat actors.
From a technical point of view, 8Base uses a customized version of Phobos v2.9.1 ransomware, which is loaded via SmokeLoader.
Phobos is a Windows-targeted RaaS operation that first appeared in 2019 and shares many code similarities with the Dharma ransomware operation.
While encrypting files, the ransomware will append the .8base expansion in recent attacks. However, the ransomware expert Michael Gillespie told BleepingComputer that Phobos ransomware submissions on Identification ransomware also used the .eight extension in older attacks.
BleepingComputer discovered that in the new attacks that add the .8base extension and the old .eight extension attacks, the same contact email address “helpermail@onionmail.org” was used as early as June 2022.
Another notable discovery from VMware analysts is that 8Base uses the “admlogs25[.]xyz” for the payload hosting, which is associated with BC systema proxy malware used by several ransomware groups for C2 obfuscation.
These findings show that 8Base operators have been carrying out encryption attacks for at least a year but only recently made a name for themselves after launching their data leak site.
8Base is only just beginning to attract the attention of analysts, with many aspects of its technical nature remaining unknown or unclear.
VMware’s report contains Indicators of Compromise (IoCs) that defenders can use to protect their systems against this growing threat.
[ad_2]
Source link
