[ad_1]

The Akira ransomware operation uses a Linux encryptor to encrypt VMware ESXi virtual machines in double extortion attacks against companies around the world.
Akira first appeared in March 2023targeting Windows systems in various industries including education, finance, real estate, manufacturing and consulting.
Like other ransomware gangs targeting businesses, threat actors steal data from hacked networks and encrypt files to perform double extortion on victims, demanding payouts of up to millions of dollars.
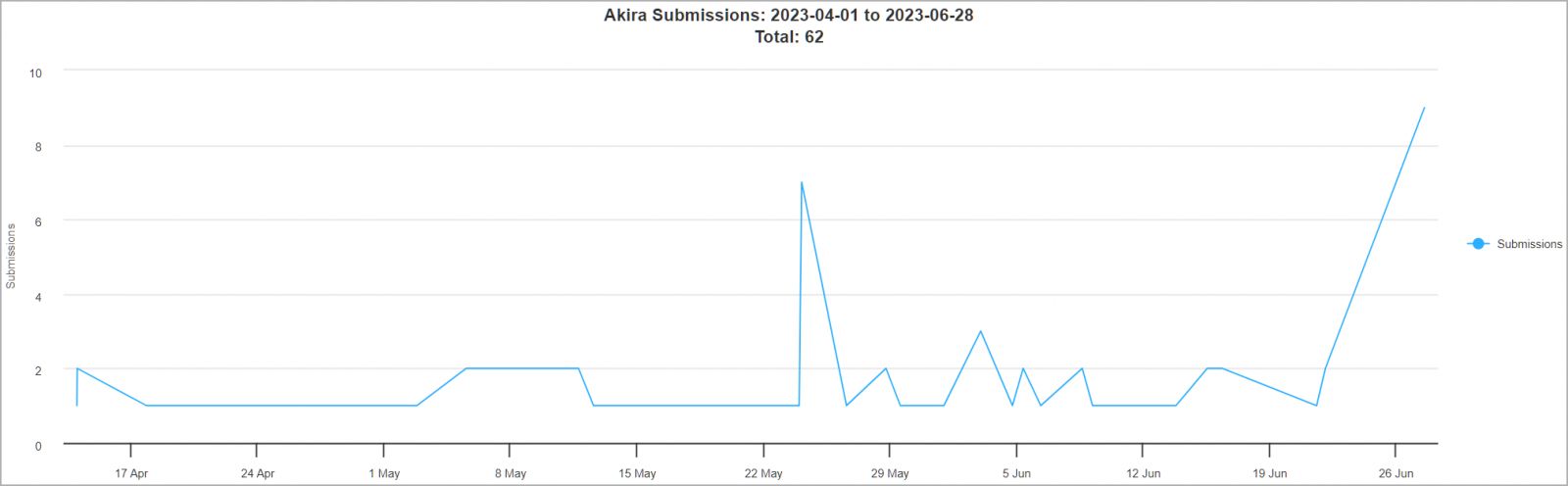
Since its launch, the ransomware operation has claimed more than 30 victims in the United States alone, with two distinct spikes in activity in Identification ransomware submissions at the end of May and today.
Source: BleepingComputer
Akira targets VMware ESXi
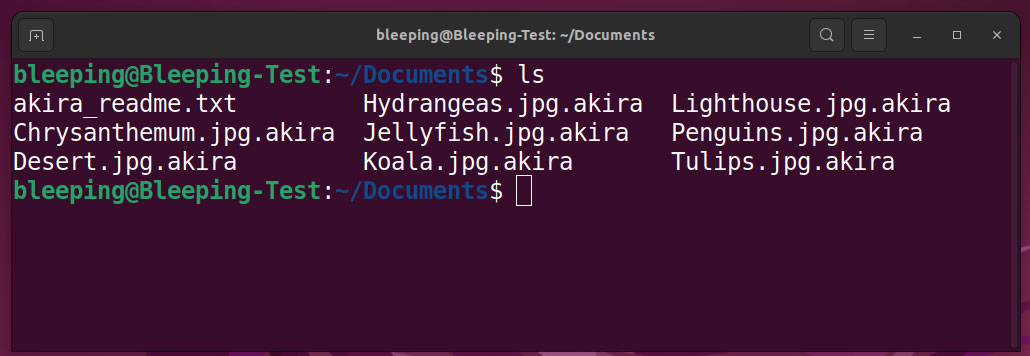
Linux version of Akira was first discovered by a malware analyst rivalrywho shared a sample of the new encryptor on VirusTotal last week.
BleepingComputer’s analysis of the Linux encryptor shows it has the project name “Esxi_Build_Esxi6”, indicating that threat actors designed it specifically to target VMware ESXi servers.
For example, one of the project’s source code files is /mnt/d/vcprojects/Esxi_Build_Esxi6/argh.h.
Over the past few years, ransomware gangs have increasingly created custom Linux encryptors to encrypt VMware ESXi servers as the company uses virtual machines for servers to improve device management and security. efficient use of resources.
By targeting ESXi servers, a threat actor can encrypt many servers running as virtual machines with a single run of the ransomware encryptor.
However, unlike other VMware ESXi encryptors analyzed by BleepingComputer, Akira’s encryptors do not contain many advanced features, such as automatically shutting down virtual machines before encrypting files using the esxcli command.
That said, the binary supports a few command line arguments that allow an attacker to customize their attacks:
- -p –encryption_path (targeted file/folder paths)
- -s –share_file (targeted network drive path)
- – n –encryption_percent (encryption percentage)
- –fork (create child process for encryption)
The -n parameter is particularly noteworthy because it allows attackers to set the amount of encrypted data on each file.
The lower this setting, the faster the encryption, but the more likely it is that victims will be able to recover their original files without paying ransom.
Source: BleepingComputer
When encrypting files, the Linux Akira encryptor will target the following extensions:
.4dd, .accdb, .accdc, .accde, .accdr, .accdt, .accft, .adb, .ade, .adf, .adp, .arc, .ora, .alf, .ask, .btr, .bdf, .cat, .cdb, .ckp, .cma, .cpd, .dacpac, .dad, .dadiagrams, .daschema, .db-shm, .db-wa, .db3, .dbc, .dbf, .dbs, .dbt, .dbv, .dbx, .dcb, .dct, .dcx, .dlis, .dp1, .dqy, .dsk, .dsn, .dtsx, .eco, .ecx, .edb, .epim, .exb, .fcd, .fdb, .fic, .fmp, .fmp12, .fmps, .fp3, .fp4, .fp5, .fp7, .fpt, .frm, .gdb, .grdb, .gwi, .hdb, .his, .idb, .ihx, .itdb, .itw, .jet, .jtx, .kdb, .kexi, .kexic, .kexis, .lgc, .lwx, .maf, .maq, .mar, .mas, .mav, .mdb, .mdf, .mpd, .mrg, .mud, .mwb, .myd, .ndf, .nnt, .nrmlib, .ns2, .ns3, .ns4, .nsf, .nv2, .nwdb, .nyf, .odb, .oqy, .orx, .owc, .p96, .p97, .pan, .pdb, .pdm, .pnz, .qry, .qvd, .rbf, .rctd, .rod, .rodx, .rpd, .rsd, .sas7bdat, .sbf, .scx, .sdb, .sdc, .sdf, .sis, .spq, .sqlite, .sqlite3, .sqlitedb, .temx, .tmd, .tps, .trc, .trm, .udb, .usr, .v12, .vis, .vpd, .vvv, .wdb, .wmdb, .wrk, .xdb, .xld, .xmlff, .abcddb, .abs, .abx, .accdw, .adn, .db2, .fm5, .hjt, .icg, .icr, .lut, .maw, .mdn, .mdt, .vdi, .vhd, .vmdk, .pvm, .vmem, .vmsn, .vmsd, .nvram, .vmx, .raw, .qcow2, .subvo, .bin, .vsv, .avhd, .vmrs, .vhdx, .avdx, .vmcx, .isoStrangely, the Linux locker seems to ignore the following folders and files, all related to Windows folders and executables, indicating that the Linux variant of Akira was ported from the Windows version.
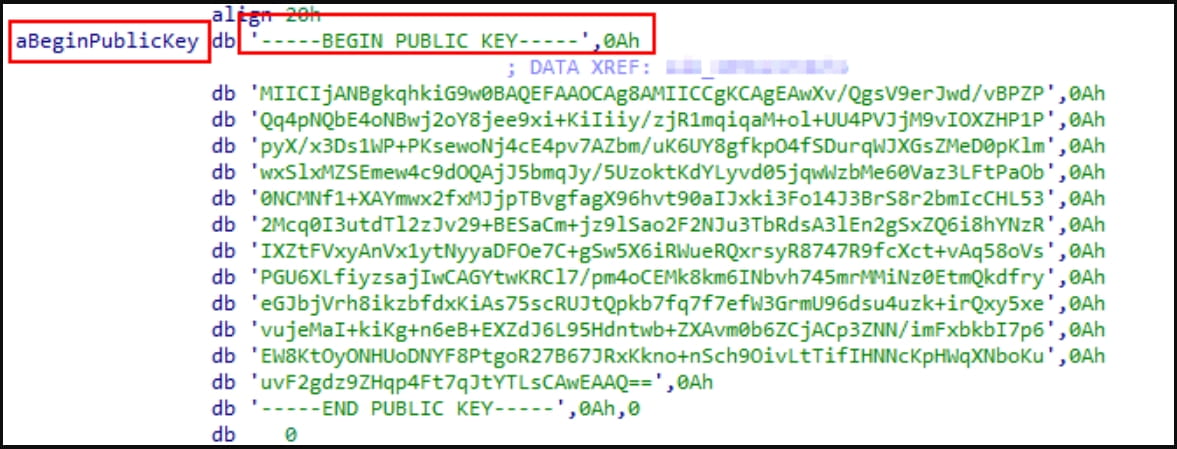
winnt, temp, thumb, $Recycle.Bin, $RECYCLE.BIN, System Volume Information, Boot, Windows, Trend Micro, .exe, .dll, .lnk, .sys, .msiCyble analysts, who also published a report about the Linux version of Akira today, explain that the encryptor includes a public RSA encryption key and leverages several symmetric key algorithms for file encryption, including AES, CAMELLIA, IDEA-CB, and DES.
The symmetric key is used to encrypt victims’ files and is then encrypted with the RSA public key. This prevents access to the decryption key unless you have the private RSA decryption key held only by the attackers.
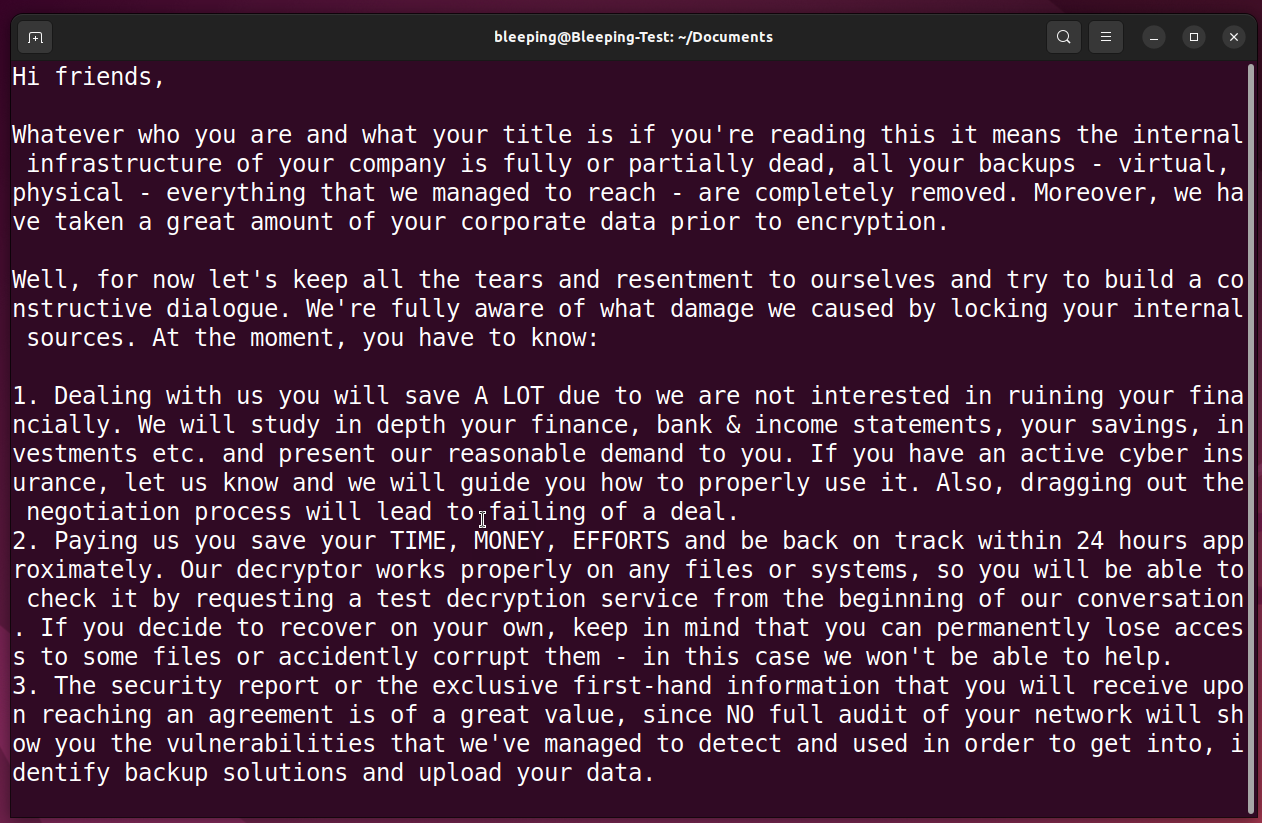
Encrypted files must be renamed to have the .akira extension, and a hard-coded ransom note named akira_readme.txt will be created in every folder on the encrypted device.
Source: BleepingComputer
The widening scope of Akira’s targeting is reflected in the group’s recently announced death toll, which only makes the threat more serious for organizations around the world.
Unfortunately, adding Linux support is a growing trend among ransomware groups, many of which use easily accessible tools to do so, as it is an easy and almost foolproof way to increase profits.
Other ransomware operations that use Linux ransomware encryptors, most targeting VMware ESXi, include Royal, basta black, LockBit, BlackMatter, AvosLocker, REvil, Hello Kitty, RansomEXXAnd Hive.
[ad_2]
Source link
