[ad_1]

A 10-year-old Windows vulnerability is still being exploited in attacks to make executables appear to be legitimately signed, with Microsoft’s patch still opt-in after all these years. Even worse, the patch is removed after upgrading to Windows 11.
On Wednesday evening, news broke that the VoIP communications company 3CX has been compromised to distribute trojanized versions of its Windows desktop application in a large-scale supply chain attack.
As part of this supply chain attack, two DLLs used by the Windows desktop application were replaced with malicious versions that download additional malware onto computers, such as an information-stealing Trojan.
One of the malicious DLLs used in the attack is usually a legitimate Microsoft-signed DLL named d3dcompiler_47.dll. However, threat actors modified the DLL to include an encrypted malicious payload at the end of the file.
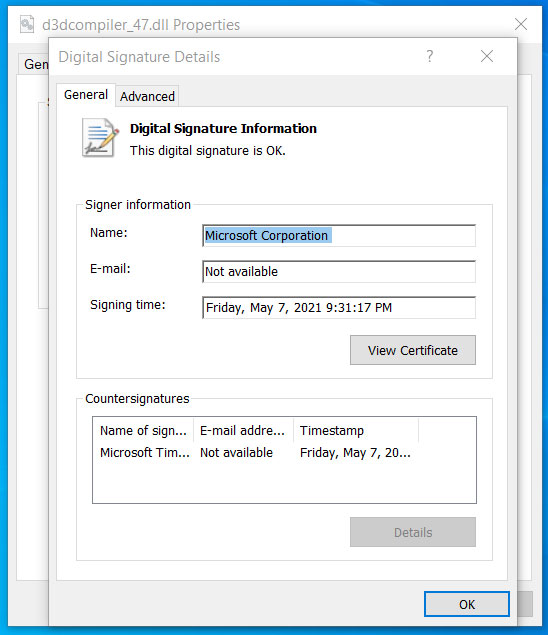
As noted for the first time yesterday, although the file was modified, Windows still showed it as correctly signed by Microsoft.
Source: BleepingComputer
Code signing an executable, such as a DLL or EXE file, is intended to assure Windows users that the file is genuine and has not been modified to include malicious code.
When a signed executable is modified, Windows displays a message stating that “the digital signature of the object has not been verified”. However, even though we know that the d3dcompiler_47.dll dll has been modified, it still shows as signed in Windows.
After contacting Will DormanSenior Vulnerability Analyst at ANALYGENCE, regarding this behavior and sharing the DLL, we were told that the DLL exploits the CVE-2013-3900 flaw, a “WinVerifyTrust signature validation vulnerability”.
Microsoft first disclosed this vulnerability on December 10, 2013 and explained that adding content to an EXE’s authenticcode signing section (WIN_CERTIFICATE structure) in a signed executable is possible without invalidating the signature.
For example, Dorman explained in tweets that the Google Chrome installer adds data to the Authenticode framework to determine whether you have chosen to “send usage statistics and crash reports to Google”. When Google Chrome is installed, it checks the Authenticode signature for this data to determine if diagnostic reporting should be enabled.
Microsoft eventually decided to make the fix optional, presumably because it would invalidate legitimate, signed executables that stored data in an executable’s signature block.
“On December 10, 2013, Microsoft released an update for all supported versions of Microsoft Windows that changes the way signatures are verified for binaries signed with the Windows Authenticode signature format,” the disclosure explains. Microsoft for CVE-2013-3900.
“This change can be activated on an opt-in basis.”
“When enabled, the new Windows Authenticode signature verification behavior will no longer allow extraneous information in the WIN_CERTIFICATE structure, and Windows will no longer recognize non-compliant binaries as signed.”
It is now almost ten years later, with the vulnerability known to be exploited by many threat actors. Yet, there remains an opt-in fix that can only be activated by manually editing the Windows registry.
To enable the fix, Windows users on 64-bit systems can make the following registry changes:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\Wintrust\Config]
“EnableCertPaddingCheck”=”1”
[HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Cryptography\Wintrust\Config]
“EnableCertPaddingCheck”=”1”
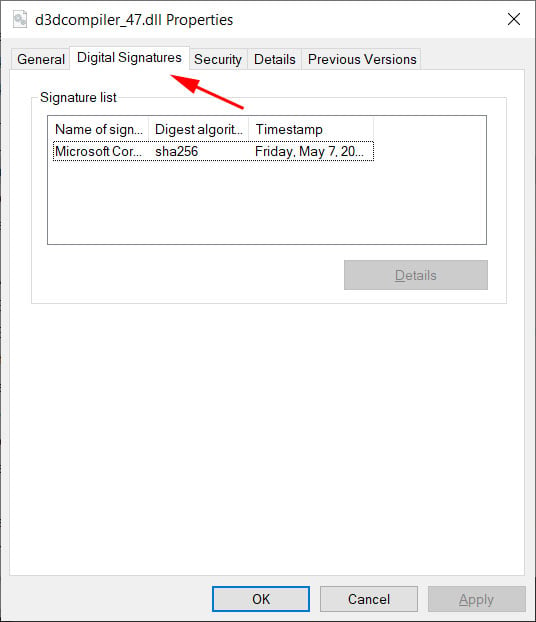
Once these registry keys are enabled, you can see how Microsoft differently validates the signature in the malicious d3dcompiler_47.dll DLL used in the 3CX supply chain attack.
 |
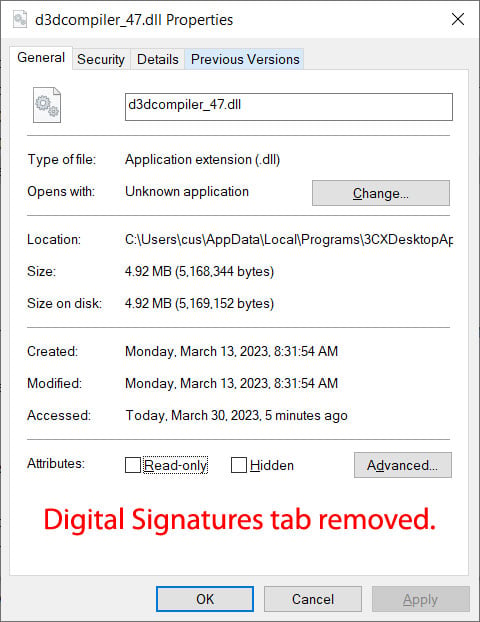 |
To make matters worse, even if you add the registry keys to apply the fix, they will be deleted once you upgrade to Windows 11, again making your device vulnerable.
As the vulnerability has been used in recent attacks, such as 3CX supply chain and a Zloader Malware Distribution Campaign in January, it became clear that it needed to be fixed, even though it bothered the developers.
Unfortunately, most are unaware of this flaw and will look at a malicious file and assume it is trustworthy because Windows flags it as such.
“But when a fix is optional, the masses will be unprotected,” Dormann warned.
I activated the optional fix, used the computer as usual throughout the day, and encountered no issues that made me regret my decision.
While this can cause a problem with some installers, like Google Chrome, not showing up as signed, the extra protection is worth it.
BleepingComputer has contacted Microsoft about continued abuse of this flaw and this is an opt-in fix only but has not received a response.
[ad_2]
Source link