[ad_1]

The WooCommerce Stripe Gateway plugin for WordPress has been found to be vulnerable to a bug that allows any unauthenticated user to see order details placed through the plugin.
WooCommerce Stripe Payment is a payment gateway for WordPress e-commerce sites, which currently has 900,000 active installs. It allows websites to accept payment methods such as Visa, MasterCard, American Express, Apple Pay, and Google Pay through Stripe’s payment processing API.
Security analysts from Pile of patches discovered that the popular plugin is vulnerable to CVE-2023-34000, an unauthenticated and insecure IDOR (Direct Object Reference) flaw that could expose sensitive details to attackers.
The vulnerability could allow unauthenticated users to view payment page data, including PII (personally identifiable information), email addresses, shipping addresses, and the user’s full name.
The above data exposure is considered severe and could lead to additional attacks, such as account hijacking attempts and credential theft via targeted phishing emails.
The flaw stems from insecure handling of order objects and a lack of proper access control measures in the plugin’s ‘javascript_params’ and ‘payment_fields’ functions.
These code errors allow abusing any WooCommerce’s order detail display functions without checking request permissions or order ownership (user matching).
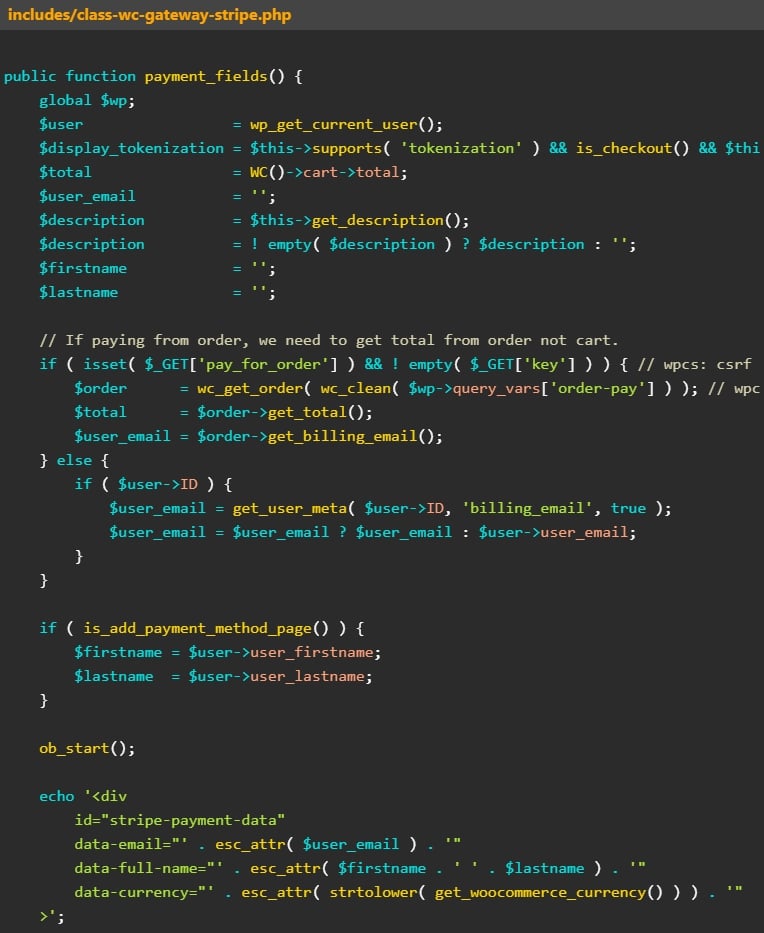
The flaw affects all versions of WooCommerce Stripe Gateway below 7.4.1, which is the version users are recommended to upgrade to.
Patchstack discovered and reported CVE-2023-34000 to the plugin vendor on April 17, 2023, and a patch with version 7.4.1 was released on May 30, 2023.
According WordPress.org Statisticsmore than half of the plugin’s active installs are currently using a vulnerable version, which results in a large attack surface, intended to attract the attention of cybercriminals.
There have been several cases of hackers attacking vulnerable WordPress plugins over the past few months, such as Elementor Pro, Advanced custom fields, Essential Addons for ElementorAnd Beautiful cookie consent bannerJust to name a few.
WordPress site admins should keep all their plugins up to date, disable unnecessary ones/used ones, and monitor their sites for suspicious activity like modifying files, changing settings, or creating new admin accounts.
[ad_2]
Source link
