[ad_1]

The premium WordPress plugin “Gravity Forms”, currently used by over 930,000 websites, is vulnerable to unauthenticated PHP object injection.
Gravity Forms is a custom form builder for website owners to use to create a payment, registration, file upload or other form required for interactions or transactions between visitors and the site.
On its website, Gravity Forms claims it’s used by a wide variety of major companies, including Airbnb, ESPN, Nike, NASA, PennState, and Unicef.
The vulnerability, which is identified as CVE-2023-28782, affects all plugin versions from 2.73 and below.
The flaw was discovered by PatchStack on March 27, 2023 and patched by the vendor with the release of version 2.7.4, which was made available on April 11, 2023.
Administrators of websites using Gravity Forms are advised to apply the available security update as soon as possible.
Fault Details
The issue stems from this lack of user-supplied input checks for the ‘maybe_unserialize’ function and can be triggered by submitting data to a form created with Gravity Forms.
“Because PHP allows object serialization, an unauthenticated user could pass ad-hoc serialized strings to a vulnerable deserialization call, resulting in arbitrary injection of PHP objects into application scope”, warn PatchStack in report.
“Note that this vulnerability could be triggered on a default installation or configuration of the Gravity Forms plugin and only requires a created form containing a list field.”
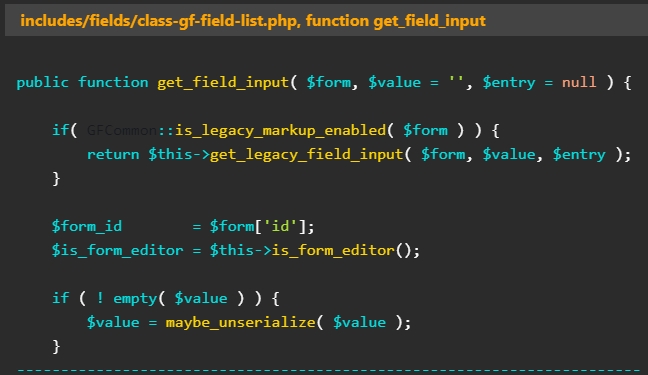
Despite the potential severity of CVE-2023-28782, PatchStack analysts could not find any String POP (Property Oriented Programming) in the vulnerable plugin, somewhat mitigating the risk.
However, the risk remains high if the same site uses other plugins or themes that contain a POP string, which is not uncommon given the wide range of WordPress plugins and themes available and the varying levels of code quality and security awareness among developers.
In these cases, exploiting CVE-2023-28782 could lead to arbitrary file access and modification, user/member data exfiltration, code execution, and more.
The plugin vendor fixed the flaw by removing the use of the ‘maybe_unserialize’ function from the Gravity Forms plugin in version 2.74.
It is also important to apply all updates on all active plugins and themes on your WordPress site, as security patches can eliminate attack vectors, like POP chains, which could be exploited in this case to launch damaging attacks.
[ad_2]
Source link
