[ad_1]

Password security, like hacker methods, continues to evolve. As computing power increases, previously best-practice passwords become increasingly vulnerable. Password managers have done their best to stay up to date, providing increased encryption security and better password recommendations.
But, the attacks are unpredictable and can even lead to compromises of the password managers themselves, such as LastPass in 2022. Even with a strong passphrase and secret key, a phishing or ransomware attack can steal access to your system without you even realizing it. This begs the question, what could you do to help protect yourself against this?
Enter Double Blind Password Policy
More and more people rely solely on technology for better password security. What if there was a safer solution? Most people can easily remember a short PIN or a word, but struggle with longer passwords. A common recommendation is to use a different password for each site, which usually requires a password manager.
Double-blind password strategy, also known as “horcruxing”, “password splitting”, or “partial passwords”, involves storing the long, complex part of a password in a password manager password and keep the short unique identifier, such as a PIN code. code or word, to yourself.
To log in to a service or website, use the password manager to fill in the complex part and add the easy-to-remember unique ID.
For example, let’s say your short phrase is abc5. You would store your randomly generated complex passwords in your password manager and use them as follows.
- 2k2kasdf9! become 2k2kasdf9!abc5
- a23k3k234# become a23k3k234#abc5
- !213kk1vk1v2k!@3 become !213kk1vk1v2k!@3abc5
Splitting the password into two parts makes it much harder for an attacker to gain full access, even if they have stolen the passphrase and secret from your password manager.
Since the password manager never knows the abc5 part of the password, attackers will never have the full picture and access, even if they hack into your password manager.
Does this mean that everyone has to adapt this strategy?
Each security method has its pros and cons. For example, some websites only allow short passwords.
If you’re aiming for the minimum password length of 12 characters recommended by NIST 800-63B guidelines and you add a 5-character word, such as “guard”, to the end of the password, a service with a limit 16-character password may not be compatible.
Additionally, one of the best features of using password managers is the ability to automatically fill and submit authentication forms.
But, with the double-blind password policy, it’s important to make sure your password manager only auto-populates, because submitting the form without the unique ID will fail. This can sacrifice some usability for security.
This method may only work for certain environments and should be adopted by users. If an organization uses a password manager, password splitting may not be effective if a shared vault is used, as the ID will also need to be widely shared manually.
Additionally, people entering and leaving require password changes not only for what is stored, but also for everyone who has access to learn the new login – a real headache.
Avoid Common Password Mistakes
With so many different strategies and recommendations over time, even the double-blind password strategy may not always work as expected.
Despite this method, a user can still create an insecure password or use one that has already been compromised. Increased computing power means that even random passwords with different characters are more likely to be cracked.
The following table shows the approximate times it would take an attacker with a modest amount of modern hardware and software to crack MD5 passwords of varying length and complexity.
Any attacker or group of attackers with more resources would be able to accelerate these times by investing in additional hardware capacity.
With ransomware payouts running into the millions of dollars, the extra installation expense can be considered easily worth it.
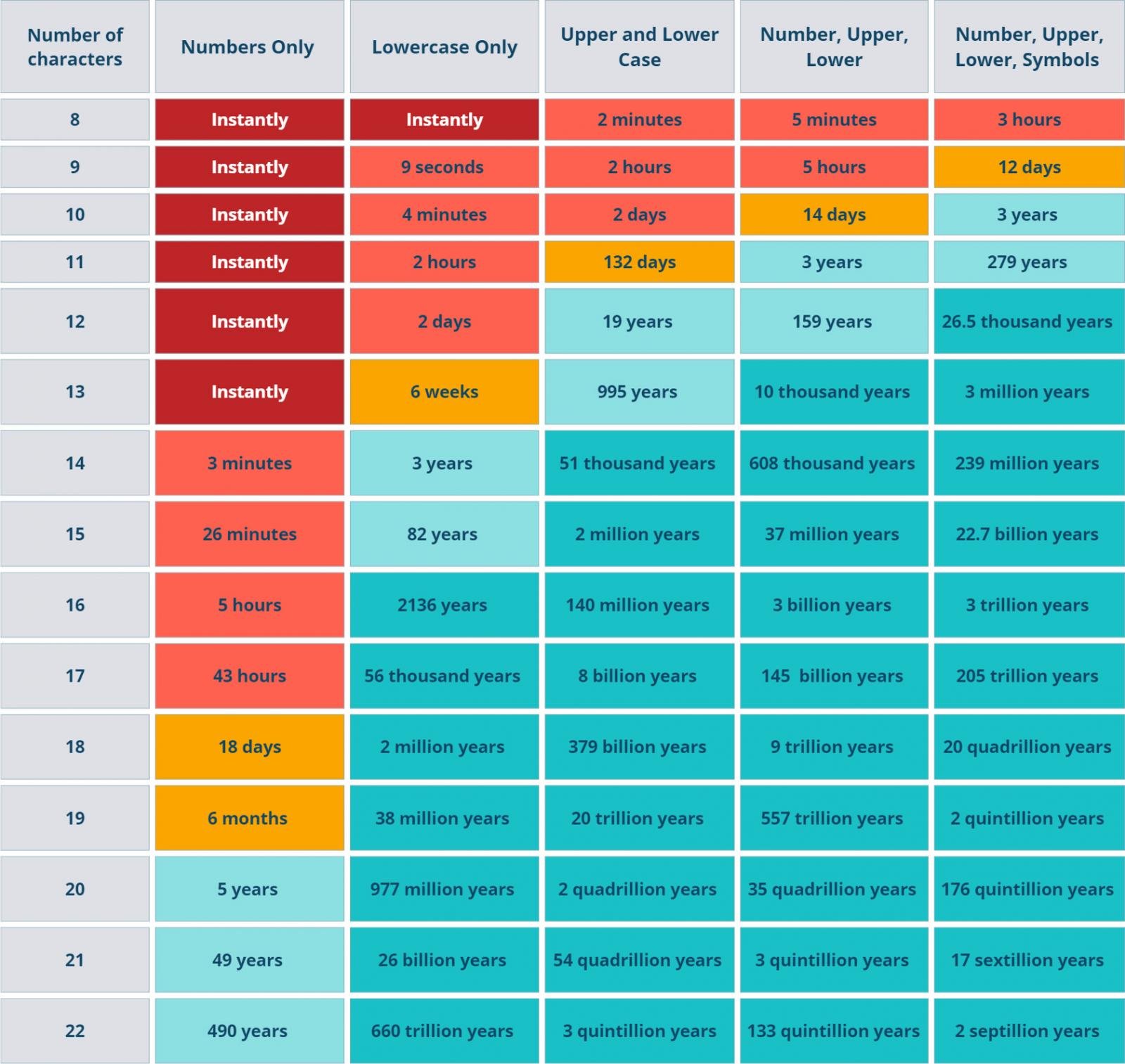
Source: Special forces
Any of the following common mistakes can result in a password that exposes your organization to password vulnerabilities:
- Use short and simple passwords, such as repeated sequences, common words or easily decipherable phrases.
- Not changing a password after a breach can be a major problem. This is especially true in scenarios where the unique identifier, known only to the user, could be compromised by potential threat actors.
- Not using multi-factor authentication (MFA) can leave you vulnerable to token theft or phishing attempts.
MFA, Password Breach Protection, and Specops Password Policy
Having a strong Active Directory password policy is the foundation of a secure password strategy. Other techniques and tools such as a double-blind password policy, password manager, and many more can be used, but organizations should start by securing their front line.
Specops password policy can help your organization establish a strong password policy and meet security compliance requirements
. As NIST 800-63B recommendations recommend, services like Specops Password Policy with Protection by violated password helps protect your users and your organization from the use of compromised passwords.
Combined with MFA, strategies like double-blind password policy can be effective, but only if end users fully embrace the practice.
For most organizations, a cleaner and therefore more secure approach would be MFA combined with a tool like Specops Password Policy with Breached Password Protection to protect your organization from potential breaches and ensure you don’t become a victim without overcomplicating the process. process.
Specops Password Policy helps users create stronger passwords in Active Directory with dynamic and informative customer feedback so they can see first-hand how to improve password security without the need for a double-blind approach.
Password policies evolve with cybersecurity challenges
Over the years, many password strategies have been proposed. While the double-blind password policy is secure, it’s only effective if users fully embrace the policy, so it’s probably best used for personal use.
To keep your organization’s end users safe and prevent password-related vulnerabilities, it’s important to start with a strong password policy, avoid using previously compromised passwords, and integrate MFA authentication where possible.
Sponsored and written by Specops software
[ad_2]
Source link
