[ad_1]

A new version of ViperSoftX information-stealing malware has been discovered with a wider range of targets, including password managers KeePass and 1Password.
The report comes from researchers at Trend Microwhich state that ViperSoftX now targets more cryptocurrency wallets than before, can infect different browsers in addition to Chrome, and is also starting to target password managers.
Finally, the latest version of the information-stealing malware offers stronger code encryption and features to evade detection by security software.
Global targeting
ViperSoftX is an information-stealing malware that steals various data from infected computers. The malware is also known to install a malicious extension named as VenomSoftX on the Chrome browser.
In the latest version analyzed by Trend Micro, targeted browsers now include Brave, Edge, Opera, and Firefox as well.
The malware was first documented in 2020 as a JavaScript-based RAT (Remote Access Trojan) and cryptocurrency hacker. However, in November 2022, Avast reported that ViperSoftX was circulating a new, much more powerful version.
Avast said at the time that it detected and stopped 93,000 attacks against its customers between January and November 2022, with most of the victims residing in the United States, Italy, Brazil and India.
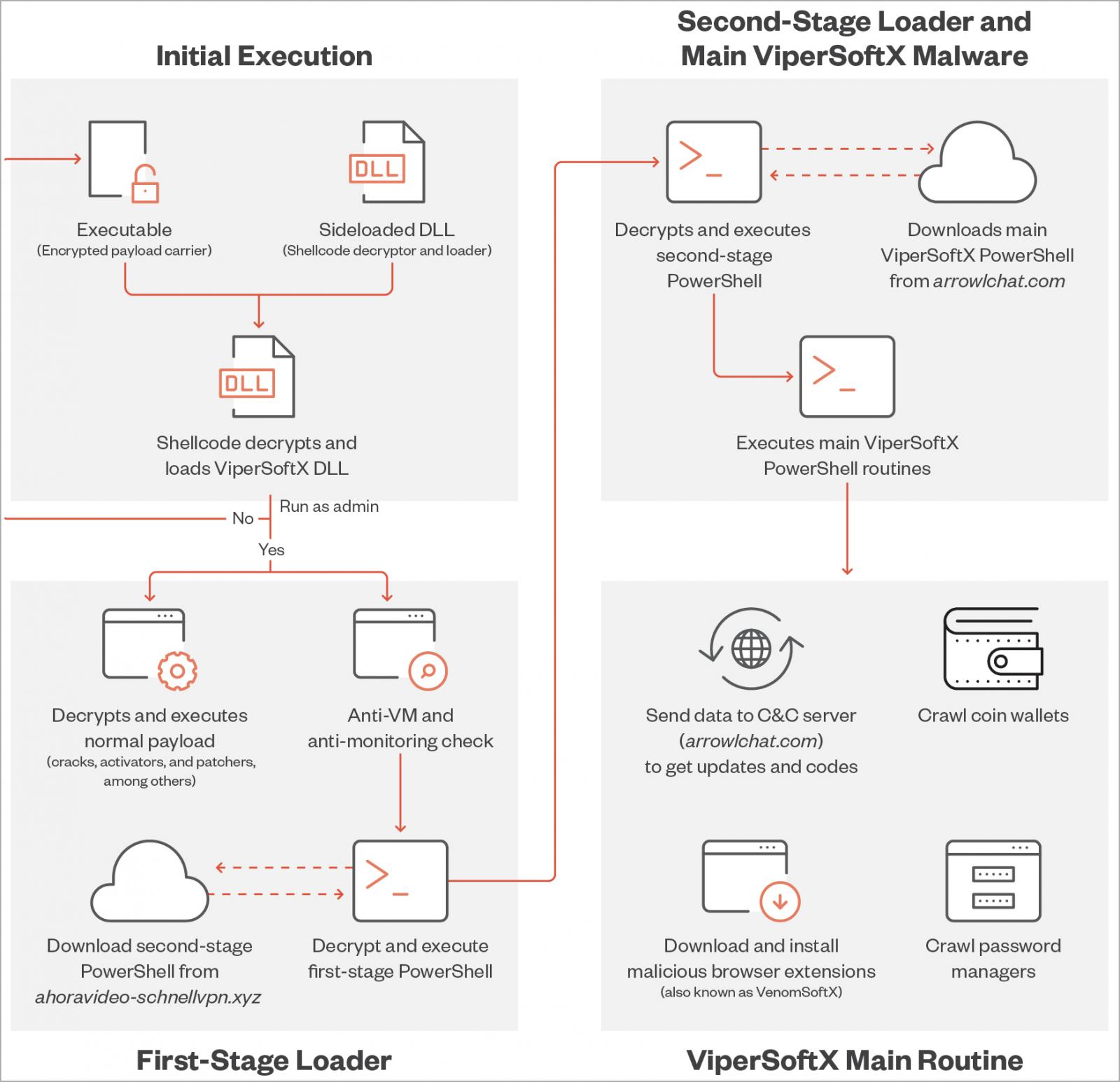
This week, Trend Micro reported that ViperSoftX is targeting both the consumer and enterprise sectors, with Australia, Japan, the United States, India, Taiwan, Malaysia, France and Italy accounting for more 50% of detected activity.
According to analysts’ observations, malware usually arrives as software cracks, activators or key generators, hiding in seemingly benign software.
Expanded targets
In the version documented by Avast, VenomSoftX targeted Blockchain, Binance, Kraken, eToro, Coinbase, Gate.io, and Kucoin crypto wallets.
However, in the latest variant, Trend Micro has spotted an increased functionality that steals the following additional wallets:
- Arsenal
- Atomic Wallet
- Binance
- Bitcoin
- Blockstream Green
- Coinomi
- Delta
- Electrum
- Exodus
- Guard
- Freedom Jaxx
- Ledger Live
- Trezor Bridge
- Coin98
- Coinbase
- Metamask
- Encrypt
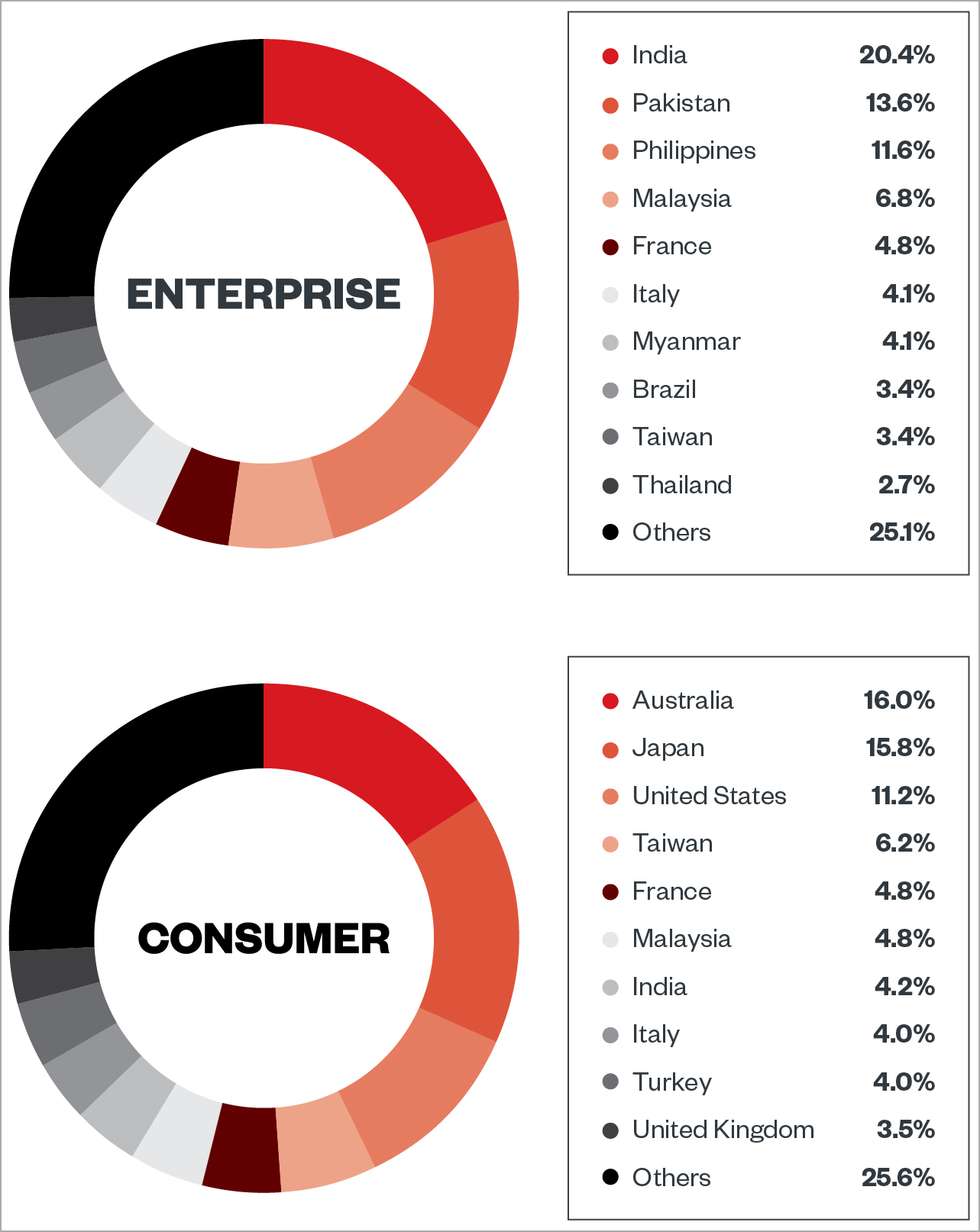
Of particular note, Trend Micro also reports that ViperSoftX now checks files associated with two password managers, namely 1Password and KeePass 2, which attempt to steal data stored in their browser extensions.
Analysts checked whether the malware incorporated an exploit for CVE-2023-24055, which allows passwords stored in plain text to be recovered, but found no evidence of the exploit.
However, Trend Micro told BleepingComputer that it’s possible that if password managers are detected, threat actors could target them with malicious activity in the later stages of the attack.
“At the time of writing, there were no clear details that we could gather from the malware codes, except to send the data collected when obtaining the configuration files. The KeePass section of the code does not was not present in reports from external researchers, so we know this is a later addition,” Trend Micro told BleepingComputer.
“It is only apparent that after gathering this information (setting up wallets and passwords) he will send it to his C2 if it exists.”
“One angle we are looking at though is the likelihood of receiving another set of codes/commands that would act as remote functions to proceed with other functions (since it has the ability to function as a backdoor).
Better Protection
The new version of ViperSoftX uses several anti-detection, anti-analysis and stealth enhancement features, from now using DLL side-loading to run on the target system in the context of ‘a trusted process, avoiding triggering alarms.
Upon arrival, the malware also looks for specific virtualization and monitoring tools such as VMWare or Process Monitor and anti-virus products such as Windows Defender and ESET before proceeding with the infection routine.
What’s most interesting is the malware’s use of “byte mapping” to encrypt its code, remapping the byte arrangement of the shellcode to render decryption and analysis without having the correct map much more complicated and time-consuming.
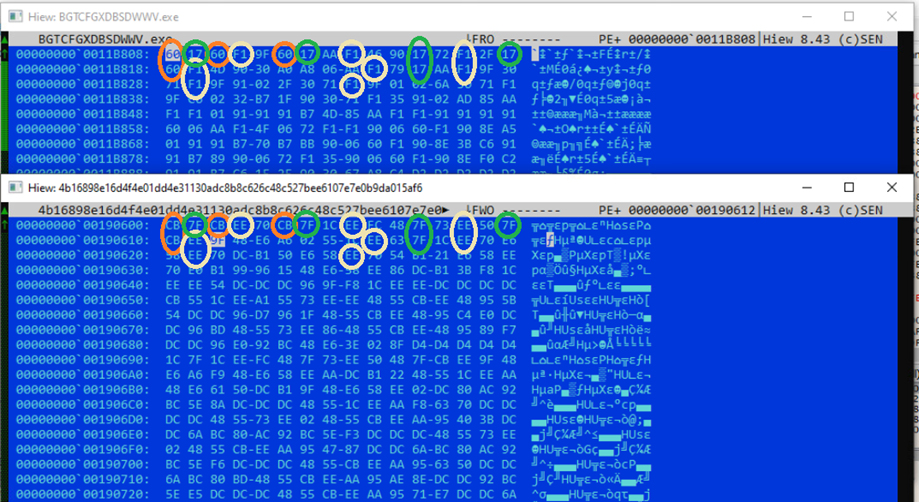
“We also found that each sideloader DLL has its own executable and bytemap pair, and attempting to decrypt it returns incorrectly rearranged shellcode if used with another ViperSoftX-linked executable” , explains Trend Micro in the report.
“This ensures that the shellcode will not be decrypted without the correct DLL since the latter contains the correct bytemap.”
Finally, ViperSoftX offers a new communication blocker on web browsers, which makes it more difficult to analyze C2 infrastructure and detect malicious traffic.
[ad_2]
Source link
