[ad_1]

The malicious Mirai botnet is actively exploiting a TP-Link Archer A21 (AX1800) WiFi router vulnerability identified as CVE-2023-1389 to embed devices into DDoS (Distributed Denial of Service) swarms.
Researchers first abused the flaw when Pwn2Own Toronto hacking event in December 2022, where two separate hacking teams hacked into the device using different routes (local network And PALE access to interfaces).
The defect was disclosed to TP-Link in January 2023, with TP-Link post a fix last month in a new firmware update.
Attempts at exploitation in the wild have been detected by Zero Day Initiative (ZDI) starting last week, initially focusing on Eastern Europe and spreading around the world.
Exploited by the Mirai botnet
The CVE-2023-1389 vulnerability is a high-severity (CVSS v3:8.8) unauthenticated command injection flaw in the local API of the web management interface of the TP-Link Archer AX21 router.
The source of the problem is the lack of input sanitization in the local API that manages the language settings of the router, which does not validate or filter what it receives. This allows remote attackers to inject commands that need to be executed on the device.
Hackers can exploit the flaw by sending a specially crafted request to the router that contains a command payload as part of the country parameter, followed by a second request that triggers execution of the command.
The first signs of exploitation in the wild became evident on April 11, 2023, and malicious activity is now detected worldwide.
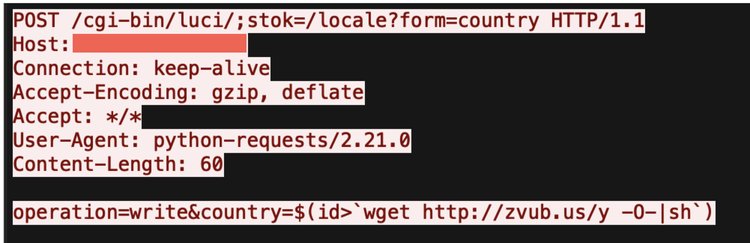
ZDI reports that a new version of the malicious Mirai botnet is now exploiting the vulnerability to gain access to the device. It then downloads the appropriate binary payload for the architecture of the router to recruit the device into its botnet.
The particular version of Mirai focuses on launching DDoS attacks, and its features indicate that it is primarily focused on game servers, having the ability to launch attacks against Valve Source Engine (VSE).
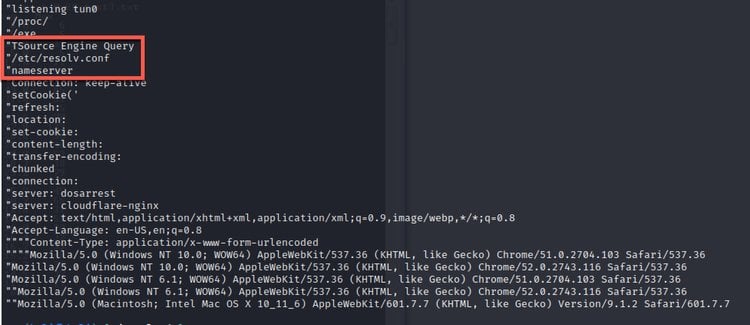
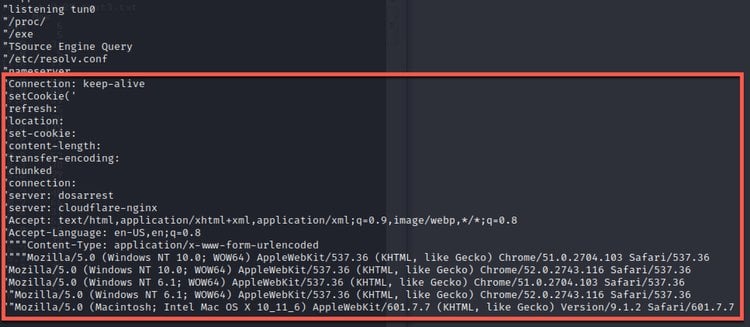
Another interesting aspect of this new malware version is that it can mimic legitimate network traffic, making it harder for DDoS mitigation solutions to distinguish between malicious and legitimate traffic to effectively reject unwanted traffic.
Fix TP-Link
TP-Link first attempted to resolve the issue on February 24, 2023, but the fix was incomplete and did not prevent exploitation.
Finally, the network equipment manufacturer released a firmware update on March 14, 2023 that addresses the risk of CVE-2023-1389, with version 1.1.4 Build 20230219.
Owners of the Archer AX21 AX1800 Dual Band WiFi 6 Router can download the latest firmware update for their device’s hardware version of this webpage.
Signs of an infected TP-Link router include overheating of the device, internet disconnections, inexplicable changes to the device’s network settings, and resetting of administrator user passwords.
[ad_2]
Source link
