[ad_1]

One of the biggest security threats is password cracking. Are you an IT system administrator concerned about the security of your organization’s data?
In this article, we’ll provide an overview of password cracking, discuss the importance of strong passwords, and detail the top 5 password cracking techniques used by hackers.
We will also provide real-life examples of password cracking attacks and their impact, along with recommendations for improving password security.
Whether you’re a seasoned IT pro or just starting out, you need to understand these password cracking techniques to better secure your organization’s data.
What happens in a password crack
Many users may have seen the password cracking depicted in the movies as a quick and impressive feat. But, it’s much less flashy and potentially much more time-consumingaccording to this Hive 2022 report. Password cracking typically involves brute-forcing a password using a variety of methods.
To understand password cracking, you must first understand how passwords are stored. There are two main ways to store passwords: encryption and hashing.
Encryption transforms plaintext into reversible ciphertext, allowing password managers to store and display the original password in plaintext.
On the other hand, hashing is the typical method used to store passwords for online services.
Since service operators do not need to reverse passwords, only to verify that they are correct, the passwords are hashed. Hash algorithms convert plaintext values to ciphertext in a one-way process.
Before attempting to crack a password, an attacker must retrieve the ciphertext value, often through man-in-the-middle attacks, hacked credential databases, or attempted of phishing.
Ultimately, the attacker can begin their work once the ciphertext value has been obtained, usually as a hash value.
Password Hacking Techniques and Tools of the Trade
Once an attacker has obtained the hash, the next step is to crack the password. Most password cracking techniques involve brute force password entry, but there are ways to make this process more effective and easier.
Brute forcing
Sometimes the only way to find a password is to try every possible combination of letters, numbers, and symbols. If the password is random, many other techniques to make work easier may not work.
This approach is the least effective, but it may be the only option when all else fails.
An attacker can use a computer or a group of computers to try all possible variants. The longer the password, the harder and longer the cracking process becomes.
By way of example, here are some recent discoveries of the Hive Report 2023 how long passwords with lowercase and uppercase letters compared to more complex passwords (i.e., numbers, uppercase and lowercase letters, and symbols in an MD5 hash) take to complete crack.
|
Characters |
Lowercase and uppercase letters |
Complex passwords |
|
8 characters |
22 minutes |
8 hours |
|
9 characters |
19 hours |
3 weeks |
|
10 characters |
1 month |
5 years |
|
11 characters |
5 years |
500 years |
|
12 characters |
300 years |
34,000 years |
Rainbow painting
Since hashing algorithms are publicly known, it is possible to create massive lists of pre-computed password hashes against which a stolen hash can be compared. Instead of generating a new hash for each variant, look up the stolen hash in a table to see if it matches.
There are many different hashing methods and nearly endless password variations, which can quickly make it very difficult to manage and store tables like this. There is another technique known as password salting which can also throw a wrench in this technique. If the server adds random values to the beginning and end of a hash (values known only to the server), the resulting hashes will no longer match the known values.
Dictionary Attack
To make it easier to brute force a password, attackers can use dictionaries of common words and phrases and names of companies, sports teams, etc. This narrows the list of potential password choices.
In the past, users were advised to change their password often (for example, every 90 days) and to use complex passwords.
But this led users to choose passwords such as !yoda2023#, which makes the job of a password cracker easier. Once the base word, yoda, is guessed through a dictionary attack, trying a few different symbols and numbers can quickly crack the password.
In the image below, you can see the top 5 basic Star Wars themed terms that are used in compromised passwords.

Source: Special forces
A more advanced form of dictionary attack is the Markov chain attack. It involves a statistical analysis of a list of words stored in a table and used to calculate the probability of character placement in a brute force attack.
Credential stuffing
Users typically use the same root password across multiple services. If a password is broken on one service, an attacker can quickly try that same password or variations on other services the user may have access to.
Known as credential stuffing, attackers will try the cracked password on multiple services to try different passwords on the same service. This can lead to the compromise of all user services.
Weak (insecure) password hashes
Of course, not all password hashing schemes are created equal. As technology advances, what was once considered safe may no longer be. This is true for hashing algorithms like MD5 or SHA-1, which can be hacked quickly.
A system that stores user password hashes with one of these algorithms could have its entire database cracked quickly.
Modern systems recommend more secure algorithms, such as bcrypt, which uses salted password hashes.
Password cracking tools
While the techniques themselves are essential to know, many password crackers rely on readily available tools.
Although three standard tools are listed below, many more are available. All of the below are open-source and community-developed, which means they’re constantly evolving.
- John the Ripper – Supports hundreds of hash types in many applications and is available on multiple platforms.
- mince cat – Works with CPU and GPU to provide a high-speed command-line password cracking tool supporting many hash types.
- Ophcrack – A tool based on rainbow tables focused on LM and NTLM passwords used in Windows environments.
While these tools make it much easier to crack retrieved hashes, there are many custom tools that can be tailored to individual organizations. A strong and up-to-date password policy is essential to protect an organization.
How users should protect themselves
With all the talk about cracking passwords, what should a user do to protect themselves? Modern security organizations such as NIST, although their Guidelines 800-63Bnow recommend the following:
- Ditch the usual password change requirements. Change passwords only at the explicit request of a user or if a password has been breached.
- Reduce the need for arbitrary password complexity and focus on overall password length, such as a minimum of 12 characters.
- All new passwords should be checked against commonly used or previously compromised passwords.
- Do not reuse passwords across different services to avoid attacks such as credential stuffing.
- Increased hash security means even shorter passwords take significantly longer to crack, such as MD5 versus PBKDF2.
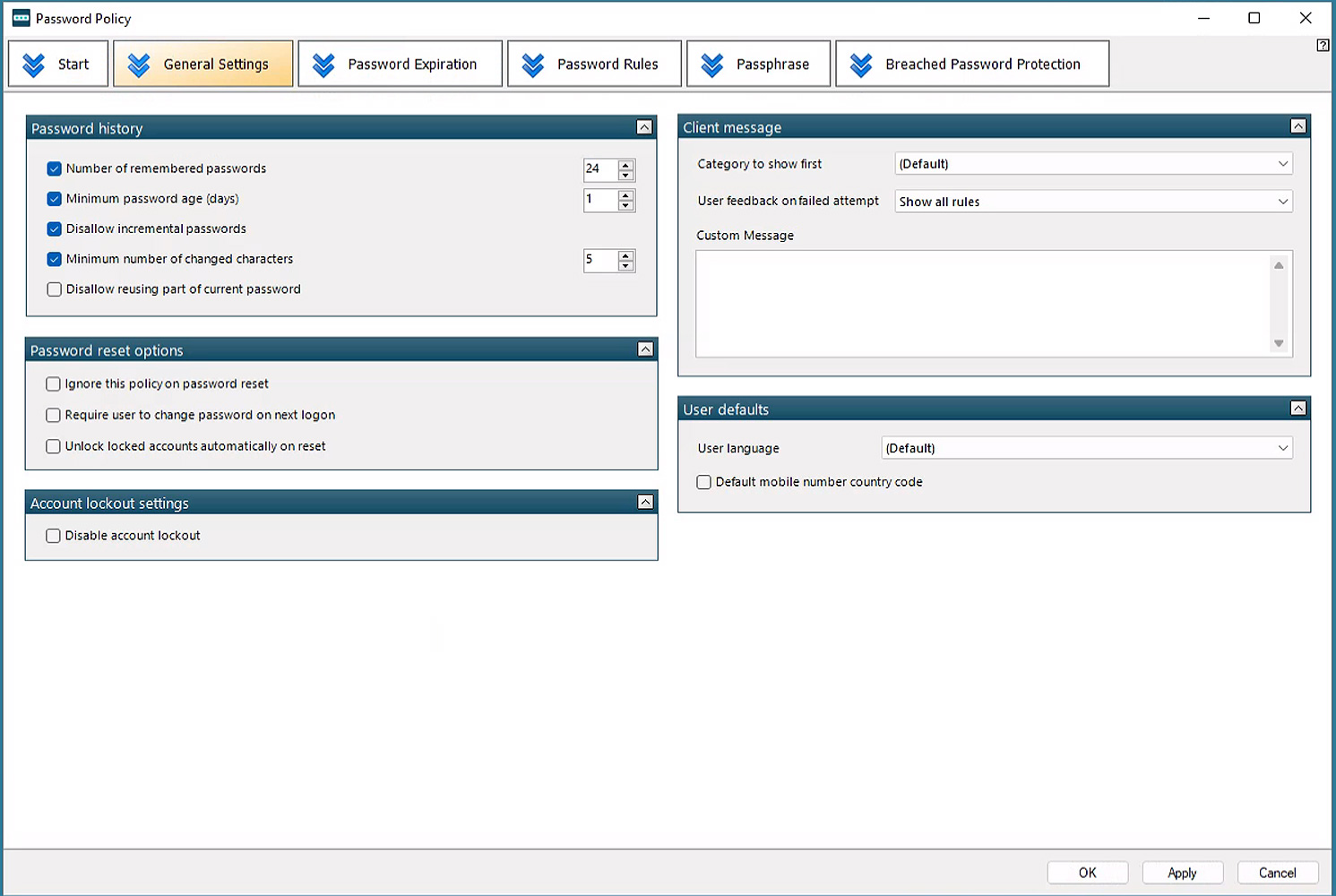
Specops password policy: ensuring the security of organizations
Cracking tools and techniques continue to get more sophisticated and faster. To stay one step ahead, tools like Specops password policy work hand-in-hand with Active Directory to ensure you’re using the latest recommendations and meeting compliance requirements.
With features like custom dictionaries, unique and customizable password policies, and powerful password breach prevention with the Breached Password Protection add-on, Specops Password Policy goes a long way toward keeping your organization secure. .
Protect organizations against password hacking
With the many tools and techniques available to password crackers, it’s no wonder password breaches happen on a regular basis.
Improve your security with tools like Specops password policy and ensure that your organization and your users are not victimized by the many threat actors.
Stay ahead of the bad guys with securely designed password policies and root out previously hacked passwords with hacked password detection!
Sponsored and written by Specops software
[ad_2]
Source link
