[ad_1]

The new NoEscape ransomware operation is believed to be a re-image of Avaddon, a ransomware gang that shut down and released its decryption keys in 2021.
NoEscape launched in June 2023 when it began targeting the company in double extortion attacks. In these attacks, hackers steal data and encrypt files on Windows, Linux, and VMware ESXi servers.
Threat actors then threaten to publicly release the stolen data if a ransom is not paid. BleepingComputer is aware of NoEscape ransomware claims ranging from hundreds of thousands of dollars to over $10 million.
Like other ransomware gangs, NoEscape does not allow its members to target CIS (ex-Soviet Union) countries, with victims from these countries receiving free decryptors and information on how they were hacked.
As of now, the ransomware gang has listed ten companies from different countries and industries on their data leak site, illustrating that they are not targeting any particular vertical.
An Avaddon name change
The Avaddon ransomware operation launched in June 2020 using phishing campaigns to target victimized businesses.
However, in June 2021, a month after the FBI and Australia law enforcement issued notices of Avaddonthe ransomware gang suddenly stop its operation and shared victims’ decryption keys with BleepingComputer in an anonymous tip.
Since then, there has been no known ransomware or extortion activity associated with threat actors until last month with the launch of the NoEscape ransomware operation.
ID-Ransomware creator and ransomware expert Michael Gillespie told BleepingComputer that the ransomware encryptors from NoEscape and Avaddon are nearly identical, with only one notable change in the encryption algorithms.
Previously, the Avaddon encryptor used AES for file encryption, with NoEscape moving to the Salsa20 algorithm.
Otherwise, the encryptors are virtually identical, with nearly identical encryption logic and file formats, including a unique way to “split RSA encrypted blobs”.
Additionally, BleepingComputer has determined that the Avaddon and NoEscape encryptors use the same configuration file and directives as described in this Main article and described below.
"lck":
"lid": "",
"iv_key": "",
"mp_key": ""
,
"ext":
"ignore": [],
"full": []
,
"paths":
"skip": [],
"primary": []
,
"settings":
"build_type": "",
"add_to_autorun": ,
"interval": ,
"print_note": ,
"set_wallpaper": ,
"large_file_size_mb": ,
"spot_size_mb":
,
"kill_services": [],
"kill_processes": [],
"note_text": ""
Although it is possible that NoEscape threat actors purchased the source code for the Avaddon encryptor, BleepingComputer has been informed by numerous researchers that some of Avaddon’s core members are now believed to be part of the new ransomware operation.
The NoEscape Encryptor
A sample of NoEscape ransomware has been shared with BleepingComputer for us to analyze.
Once executed, NoEscape will run the following commands to delete Windows Volume Shadow Copies, local Windows Backup Catalogs, and to disable Windows Automatic Repair.
SHADOWCOPY DELETE /nointeractive
wmic SHADOWCOPY DELETE /nointeractive
wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest
wbadmin DELETE BACKUP -deleteOldest
wbadmin DELETE BACKUP -keepVersions:0
vssadmin Delete Shadows /All /Quiet
bcdedit /set default recoveryenabled No
The encryptor will then begin to terminate the following processes, including those associated with security software, backup applications, and web and database servers.
360doctor, 360se, Culture, Defwatch, GDscan, MsDtSrvr, QBCFMonitorService, QBDBMgr, QBIDPService, QBW32, RAgui, RTVscan, agntsvc, agntsvcencsvc, agntsvcisqlplussvc, anvir, anvir64, apache, axlbridge, backup, ccleaner, ccleaner64, dbeng50, dbsnmp, encsvc, excel, far, fdhost, fdlauncher, httpd, infopath, isqlplussvc, java, kingdee, msaccess, msftesql, mspub, mydesktopqos, mydesktopservice, mysqld-nt, mysqld-opt, mysqld, ncsvc, ocautoupds, ocomm, ocssd, onedrive, onenote, oracle, outlook, powerpnt, procexp, qbupdate, sqbcoreservice, sql, sqlagent, sqlbrowser, sqlmangr, sqlserver, sqlservr, sqlwriter, steam, supervise, synctime, taskkill, tasklist, tbirdconfig, thebat, thunderbird, tomcat, tomcat6, u8, ufida, visio, wdswfsafe, winword, wordpad, wuauclt, wxServer, wxServerView, and xfssvccon
It will also stop the following Windows services associated with databases, QuickBooks, security software, and virtual machine platforms.
Culserver, DefWatch, GxBlr, GxCIMgr, GxCVD, GxFWD, GxVss, QBCFMonitorService, QBIDPService, RTVscan, SavRoam, VMAuthdService, VMUSBArbService, VMnetDHCP, VMwareHostd, backup, ccEvtMgr, ccSetMgr, dbeng8, dbsrv12, memtas, mepocs, msexchange, msmdsrv, sophos, sql, sqladhlp, sqlagent, sqlbrowser, sqlservr, sqlwriter, svc$, tomcat6, veeam, vmware-converter, vmware-usbarbitator64, vss
The ransomware terminates these applications to unlock files that can be opened and prevented from being encrypted.
However, even if the files are locked, the encryptor uses the Windows Restart Manager API to close processes or stop Windows services that may keep a file open and prevent encryption.
When encrypting files, the encryptor will ignore all files that have the following file extensions:
exe, bat, bin, cmd, com, cpl, dat, dll, drv, hta, ini, lnk, lock, log, mod, msc, msi, msp, pif, prf, rdp, scr, shs, swp, sys, theme
It will also ignore files in folders whose names contain the following strings:
$recycle.bin, $windows.~bt, $windows.~ws, %PROGRAMFILES(x86)%, %PUBLIC%, %ProgramData%, %SYSTEMDRIVE%\\Program Files, %SYSTEMDRIVE%\\Users\\All Users, %SYSTEMDRIVE%\\Windows, %TMP%, %USERPROFILE%\\AppData, AppData, %AppData%, EFI, Intel, MSOCache, Mozilla, Program Files, ProgramData, Tor Browser, Windows, WINDOWS, boot, google, perflogs, system volume information, windows.old
When encrypting, Gillespie told BleepingComputer that it can be configured to use three modes:
- Complete – the whole file is encrypted
- Partiel – Only the first X megabytes are encrypted.
- Cut – Uses intermittent encryption to encrypt blocks of data.
However, NoEscape includes a configuration option that forces the encryptor to fully encrypt files with file extensions accdb, edb, mdb, mdf, mds, ndf, and sql.
Files are encrypted using Salsa20, with the encryption key being encrypted with a provided RSA private key. Encrypted files will have a 10 character extension appended to the filename, which is unique for each victim as shown below.
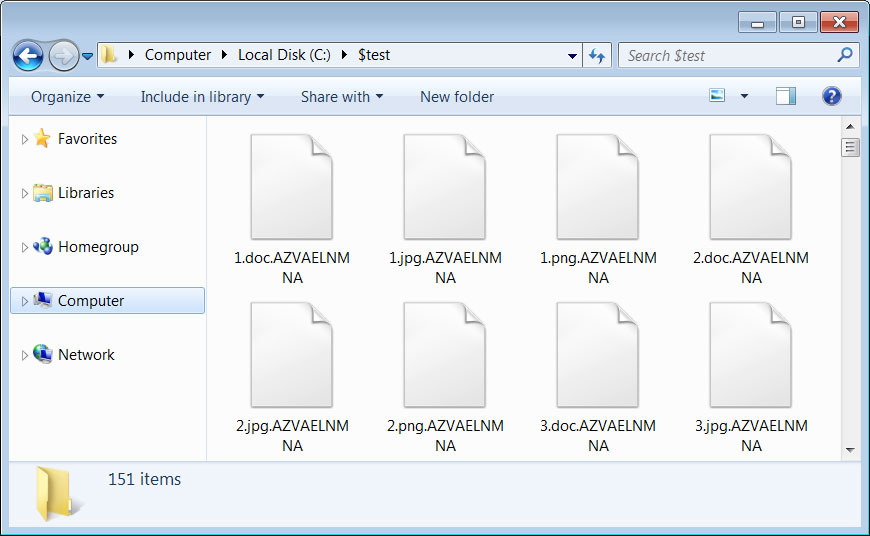
Source: BleepingComputer
The encryptor will also configure a scheduled task named “SystemUpdate” for persistence on the device and to launch the encryptor when logging into Windows.
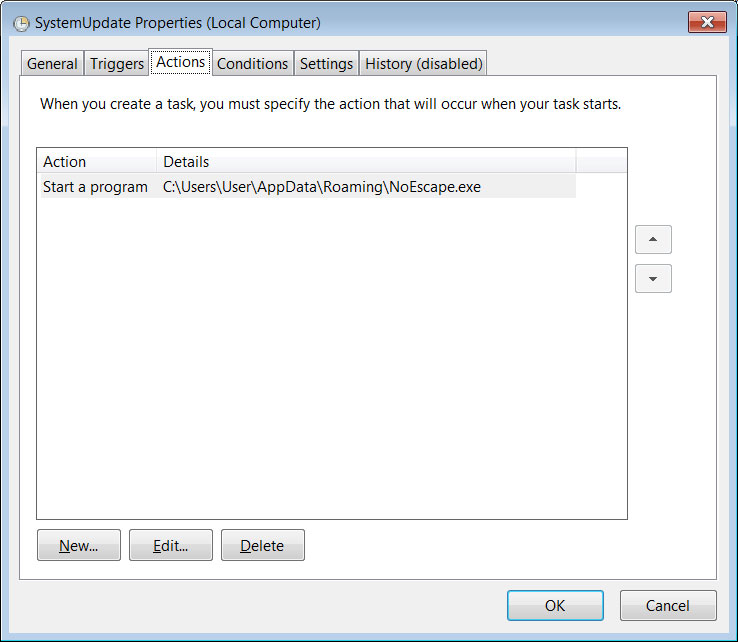
Source: BleepingComputer
The ransomware will also change the Windows desktop background to an image telling victims that they can find instructions in the ransom notes named HOW_TO_RECOVER_FILES.txt.
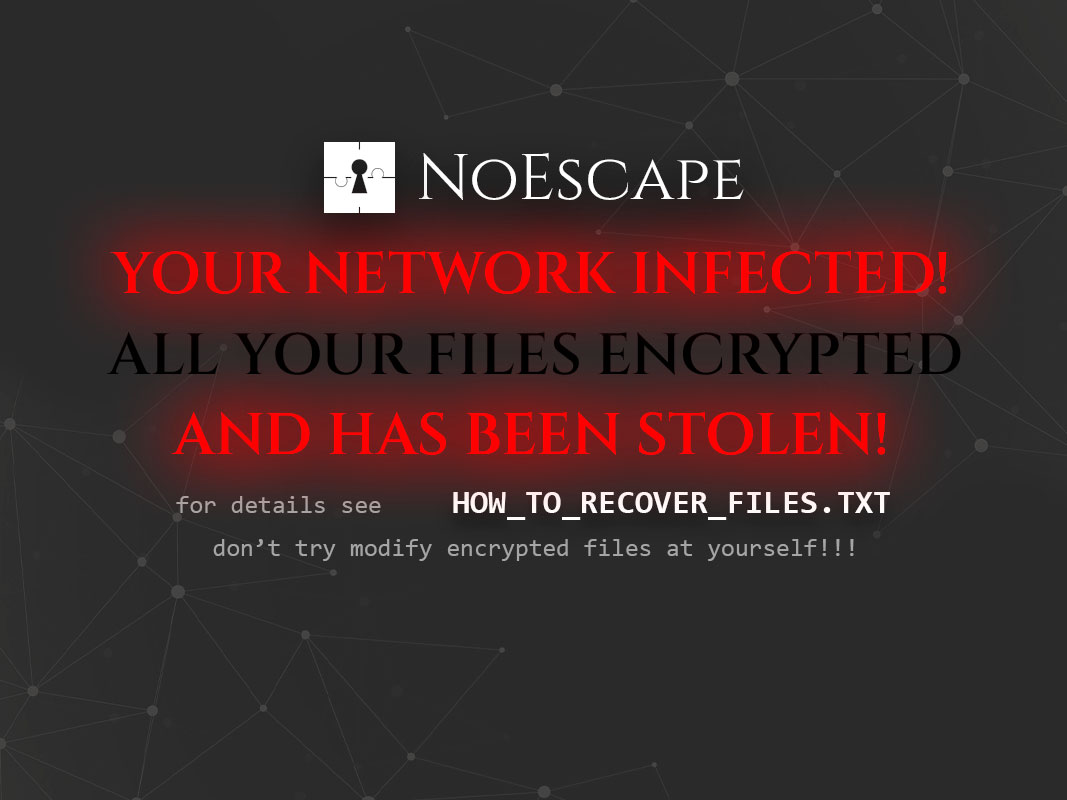
Source: BleepingComputer
HOW_TO_RECOVER_FILES.txt ransom notes are located in every device folder and include information about what happened to a victim’s files and links to the NoEscape Tor trading site.
“We are not a political company, and we are not interested in your private affairs. We are a commercial company, and we are only interested in money,” the NoEscape ransom note promises.
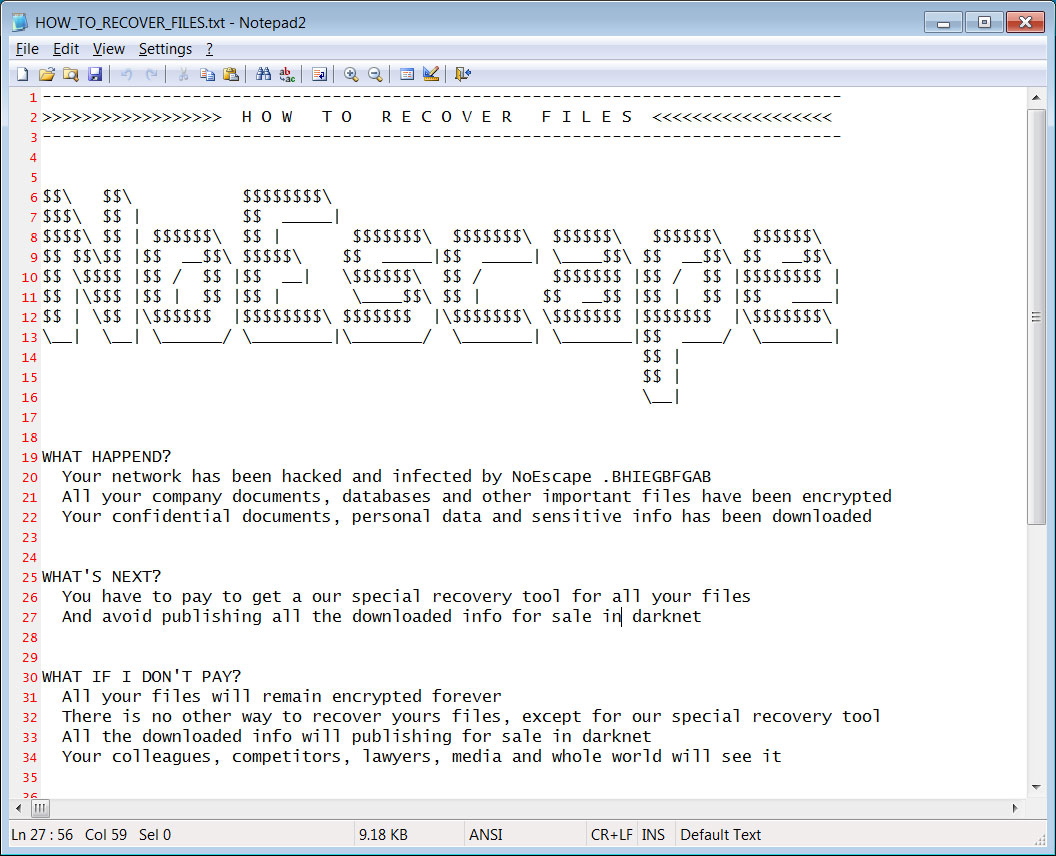
Source: BleepingComputer
On Linux, the /etc/motd is also replaced by the ransom note, which is displayed to victims when they log in.
The ransom notes contain a “personal ID” required to log in to the threat actor’s Tor payment site and access the victim’s unique trading page. This page includes bitcoin ransom amount, test decryption feature and chat panel to negotiate with threat actors.
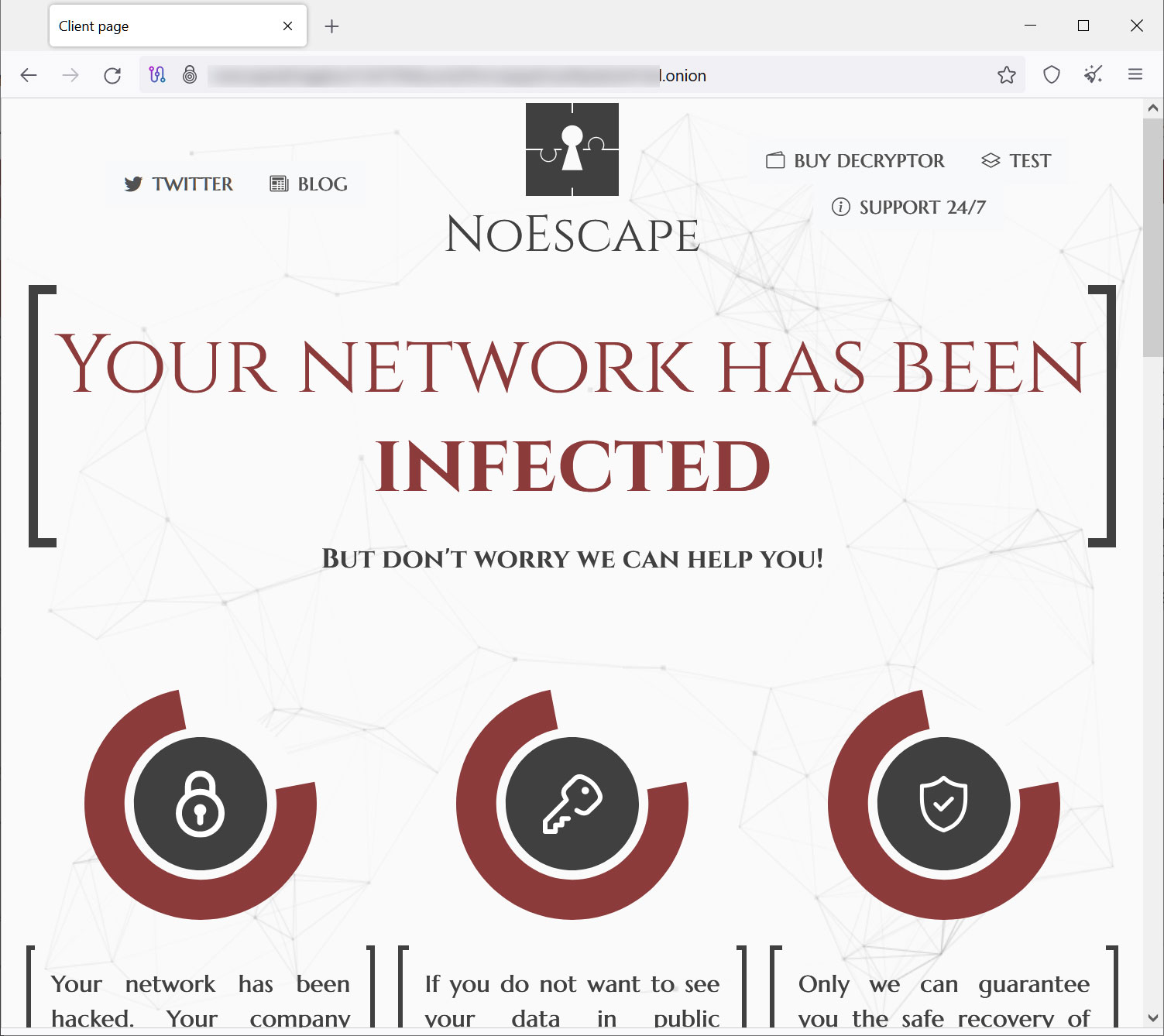
Source: BleepingComputer
As previously reported, BleepingComputer has seen NoEscape ransom demands ranging from a few hundred thousand dollars to over $10 million.
After paying, victims will see a list of available decryptors, which are those for Windows XP, modern versions of Windows and Linux.
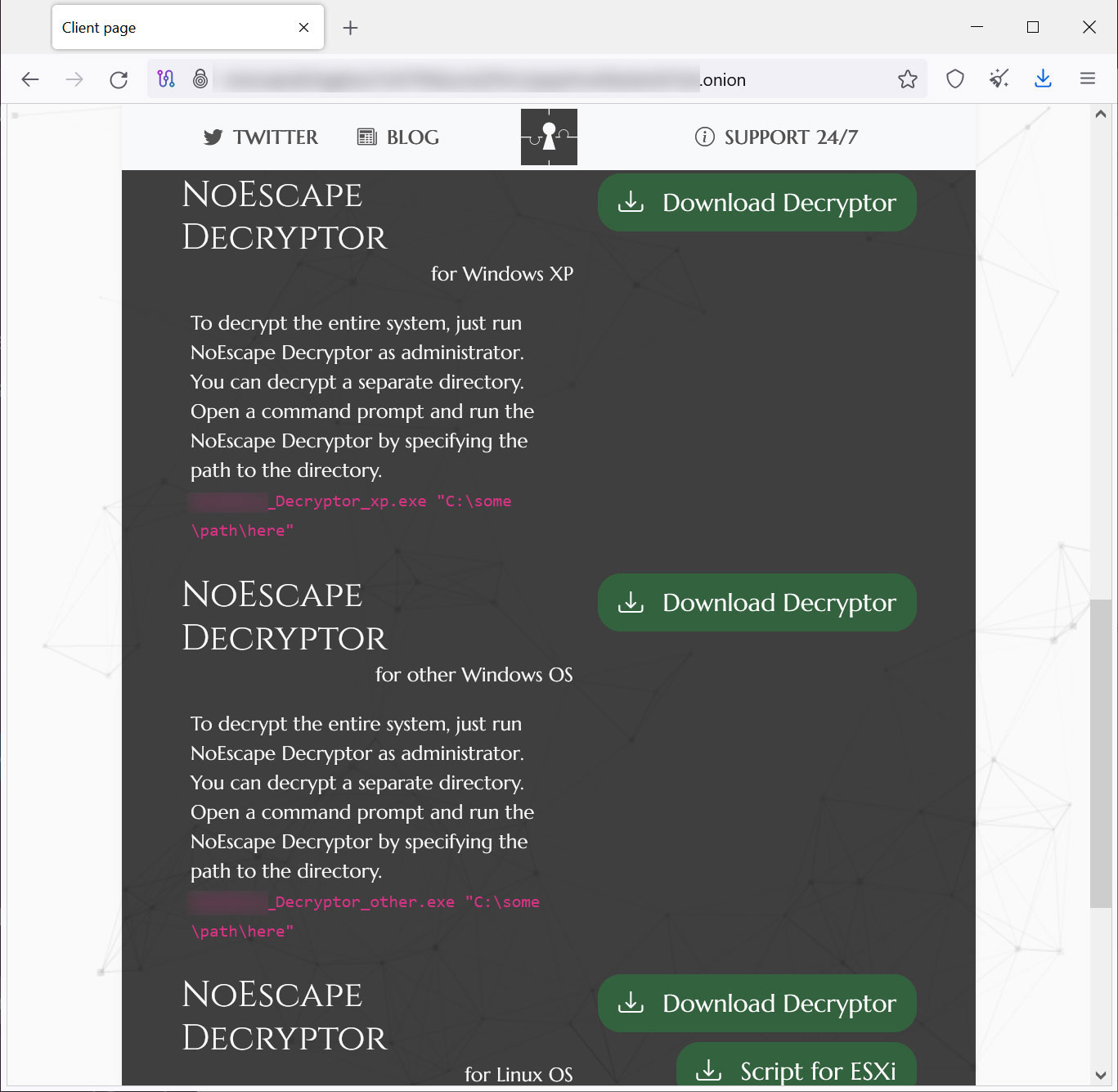
Source: BleepingComputer
For victim companies running VMware ESXi, NoEscape provides a shell script that can be used to restore /etc/motd files and decrypt the files using the Linux decryptor.
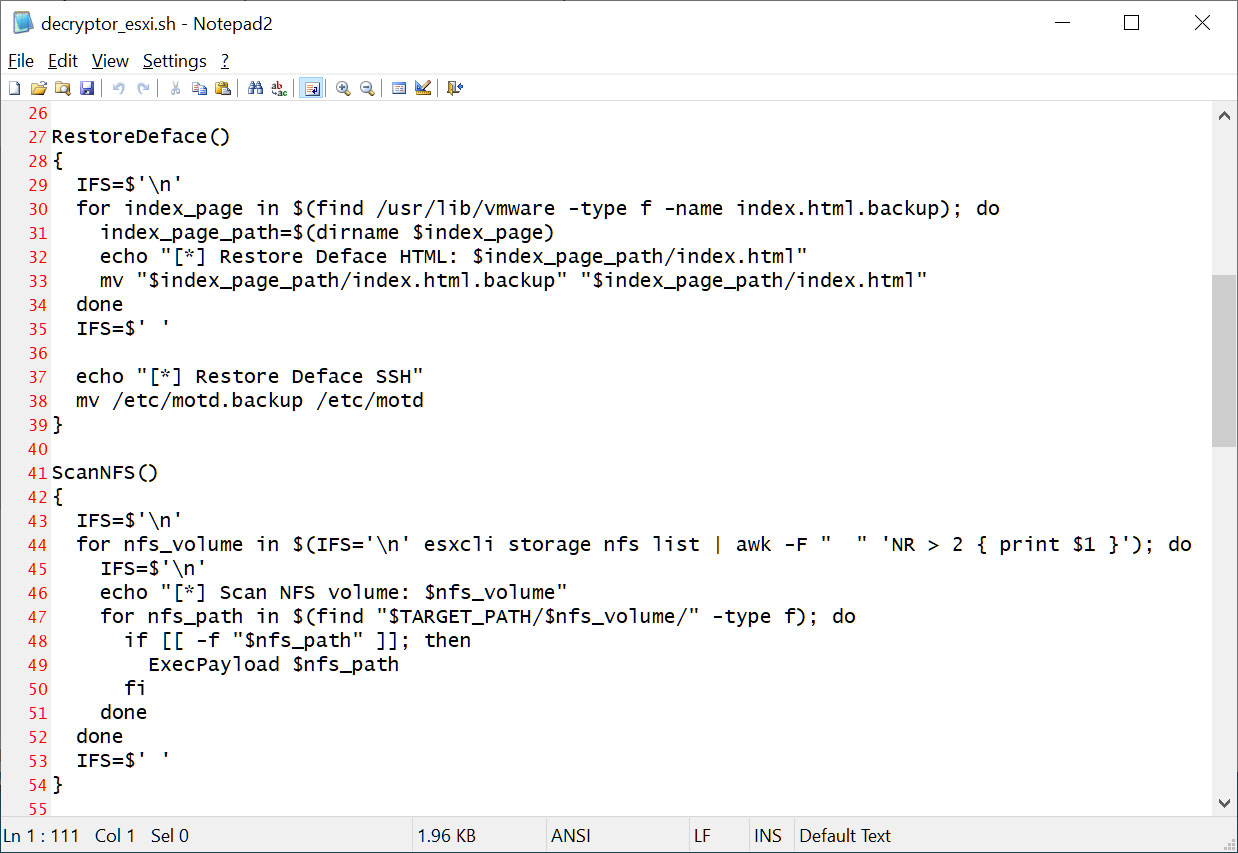
Source: BleepingComputer
Data leak site used to extort victims
Like other ransomware operations, NoEscape will breach a corporate network and laterally spread to other devices. Once threat actors obtain Windows domain administrator credentials, they will deploy the ransomware throughout the network.
However, before encrypting files, threat actors have already stolen corporate data to use as leverage in their extortion attempts. Threat actors then warn victims that their data will be made public or sold to other threat actors if a ransom is not paid.
At the time of this writing, NoEscape had leaked the data or started extorting ten victims on their data leak site, with the size of the leaked data ranging from 3.7GB for one company to 111GB for another.
Source: BleepingComputer
The ransomware is currently being analyzed for its weaknesses, and BleepingComputer does not advise paying a ransom until it is determined whether a free decryptor can recover files for free.
[ad_2]
Source link
