[ad_1]

TELUS, Canada’s second-largest telecommunications company, is investigating a possible data breach after a malicious actor shared samples of what appears to be employee data online. The threat actor then posted screenshots apparently showing private source code repositories and payroll records held by the company.
TELUS has so far found no evidence of corporate or retail customer data theft and continues to monitor the potential incident.
Private source code and employee data put up for sale
On February 17, a hacker posted what he claims to be a list of TELUS employees (including names and email addresses) for sale on a data breach forum.
“TELUS employees [sic] from a very recent breach. We have over 76,000 unique emails and on top of that we have internal information associated with each employee pulled from the Telus API,” the forum post reads.
Although BleepingComputer has not yet been able to confirm the veracity of the threat actor’s claims, the small sample released by the seller contains valid names and email addresses matching current TELUS employees, specifically the developers of software and technical staff.
On Tuesday, February 21, the same hacker created another forum post, this time offering to sell TELUS’ private GitHub repositories, source code, and company payroll records.
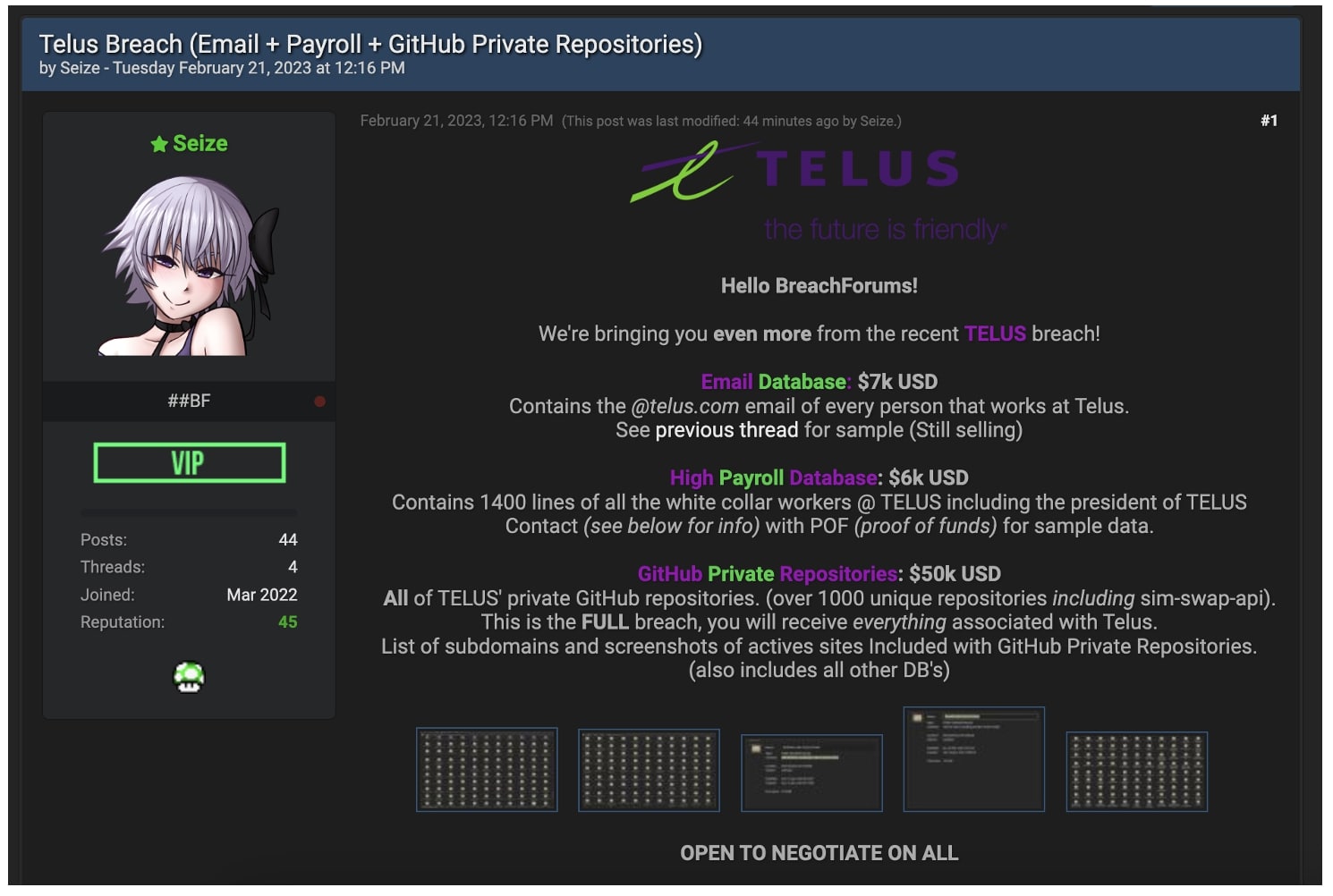
“In the repositories are the backend, the frontend, the middleware [information,] AWS Keys, Google Authentication Keys, Source Code, Test Apps, Staging/Prod/Test and more!”, reads the seller’s latest post.
The vendor further boasts that the stolen source code contains the company’s “sim-swap-api” which will allegedly allow adversaries to perform SIM card swapping attacks.
Although the threat actor called this a “COMPLETE breach” and promised to sell “everything associated with Telus”, it is too early to conclude that an incident actually took place at TELUS or to rule out infringement by a third-party provider.
“We are investigating allegations that a small amount of data related to internal TELUS source code and information from certain TELUS team members has appeared on the dark web,” a TELUS spokesperson told BleepingComputer.
“We can confirm that at this stage our investigation, which we launched as soon as we became aware of the incident, did not identify any corporate or retail customer data.”
BleepingComputer continues to monitor development and provide you with updates on the situation.
In the meantime, TELUS employees and customers should be alert to any phishing or scam messages that target them and refrain from receiving such emails, text messages or telephone communications.
[ad_2]
Source link
