[ad_1]

Researchers at North Carolina State University Raleigh have discovered a privacy risk in the Strava app’s heatmap feature that could lead to the identification of users’ home addresses.
Strava is a popular running companion and fitness tracker app with over 100 million users worldwide, helping people track their heart rate, activity details, GPS location, and more.
In 2018, Strava introduced a feature called “heatmap” which anonymously aggregates user activity (runners, cyclists, hikers) to help users find trails or exercise hotspots, meet like-minded people and to conduct their sessions in busier and safer places.
However, as researchers findthis feature opens up the ability to track and de-anonymize users using publicly available heatmap data combined with specific user metadata.
Location of athletes’ homes
The first step the researchers took was to collect publicly available data via the Strava heatmap over a month for the states of Arkansas, Ohio and North Carolina.
Next, they used image analysis to detect start/stop zones next to streets, indicating that a specific house is linked to a tracked source of activity.
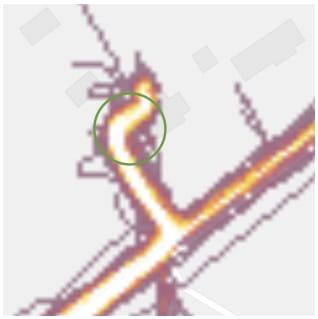
After selecting heatmap screenshots that matched the criteria, the team overlaid OpenStreetMaps images at zoom levels that helped identify individual residential addresses.
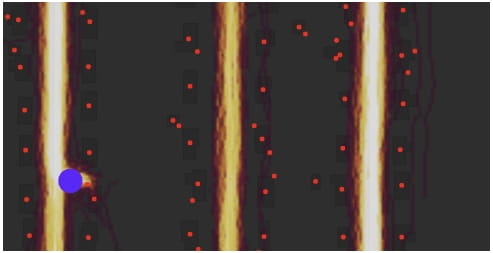
The next step was to perform user exploration by leveraging a poorly documented search feature on Strava to locate users who recorded a specific city as their location.
By comparing heatmap endpoints and a user’s personal data from the search function, researchers were able to correlate high activity points on the heatmap and users’ home addresses.
Public Strava profiles contain activity data with timestamps and distances, making it easier to identify potential routes that match patterns in the heatmap data, limiting people and area matches.
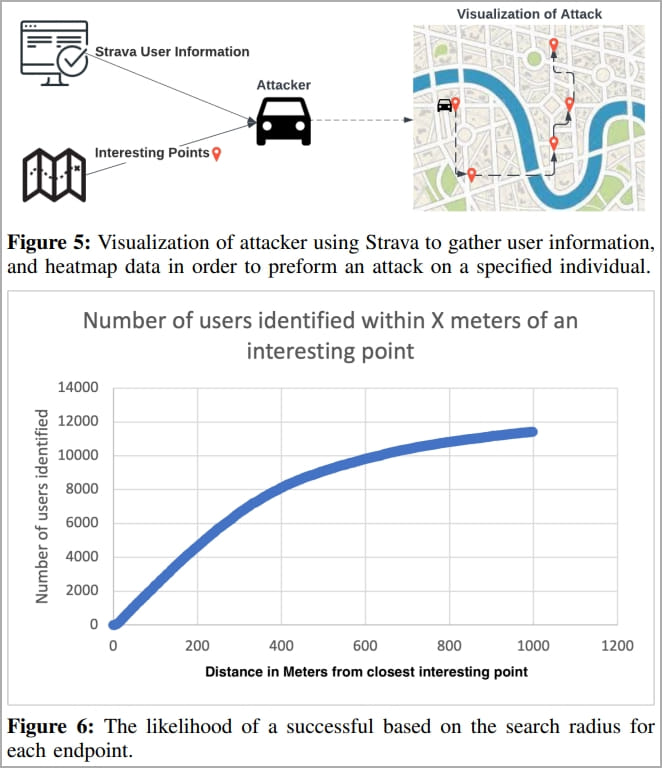
As many Strava users register with their real names and even upload profile pictures of themselves, it is possible to correlate identities with places of origin.
For their research, the scientists correlated their findings with voter registration data and found that their predictions were about 37.5% accurate.
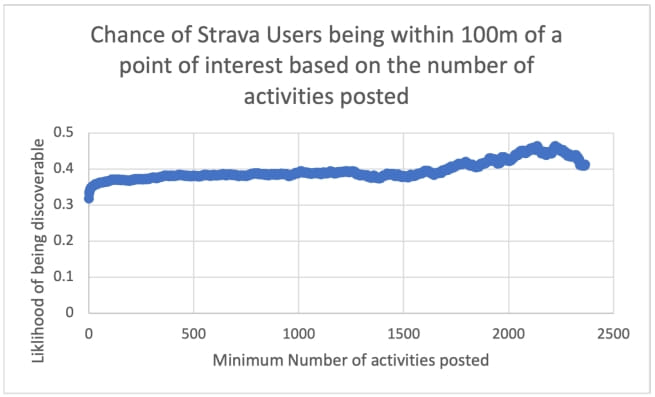
“A more active user produces more heat on the Strava heatmap and is therefore more easily identified. Figure 7 shows the likelihood of a match based on the number of activities posted,” the researchers explain.
“For the rest of the analysis, we will assume that the attack target publishes an average number of activities, which for our dataset is 308 activities.”
“With the 100 meter threshold, and the victim displaying 308 activities, the probability of being discovered is 37.5%.”
Improving Strava Privacy
The first passive mitigation is living in a densely populated area that receives massive amounts of Strava heatmap data, making person-specific tracking nearly impossible.
Another way to mitigate this privacy concern would be to start tracking after leaving your home or for Strava to create an exclusion for the heatmap for a few meters around home locations as shown in OpenStreetMaps.
The researchers also propose that the heatmap supports an option for users to set privacy zones around their homes or elsewhere as well.
The heatmap feature is enabled by default on all Strava apps, but users can disable it through settings.
As for profile settings, those concerned about privacy should keep their user profiles private on the Strava app, which would not expose names and activity data.
BleepingComputer has reached out to Strava to ask for a comment on the article’s findings and whether the software vendor has any repair plans, but we haven’t received a response as of press time.
[ad_2]
Source link
