[ad_1]

A new, stealthier variant of the “BPFDoor” Linux malware has been discovered, with stronger encryption and reverse communications.
BPFDoor is a stealth backdoor malware that has been active since at least 2017 but was only discovered by security researchers around 12 months ago.
The malware gets its name from using the “Berkley Packet Filter” (BPF) to receive instructions while bypassing firewall restrictions of incoming traffic.
BPFDoor is designed to allow threat actors to maintain long persistence on hacked Linux systems and remain undetected for long periods of time.
New version BPFDoor
Until 2022, the malware used RC4 encryption, bind shell and iptables for communication, while commands and filenames were hardcoded.
The new variant analyzed by Deep Instinct has static library encryption, reverse shell communication, and all commands are sent by the C2 server.
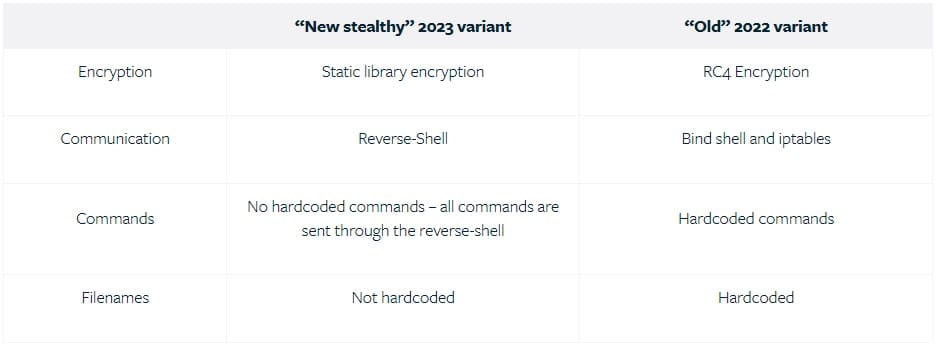
By embedding the encryption in a static library, malware developers achieve better stealth and concealment, as reliance on external libraries like the one featuring the RC4 encryption algorithm is removed.
The main advantage of the reverse shell over the bind shell is that the former establishes a connection between the infected host and the threat actor’s command and control servers, allowing communication with the attackers’ servers even when a firewall -fire protects the network.
Finally, removing hard-coded commands reduces the likelihood that antivirus software will detect malware using static analysis such as signature-based detection. It also theoretically gives it more flexibility, supporting a more diverse set of commands.
Deep Instinct reports that the latest version of BPFDoor is not flagged as malicious by any of the AV engines available on VirusTotal, despite its first submission to the platform dating back to February 2023.
Operating logic
On first run, BPFDoor creates and locks a runtime file at “/var/run/initd.lock”, then launches to run as a child process, and finally configures itself to ignore various system signals operations that could interrupt it.
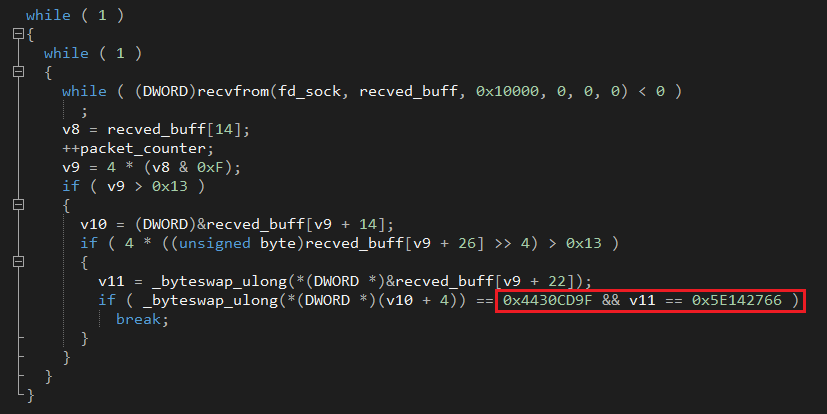
Next, the malware allocates a buffer and creates a packet sniffing socket which it will use to monitor incoming traffic for a “magic” byte sequence (“\x44\x30\xCD\x9F\x5E\x14\ x27\x66”) .
At this point, BPFDoor attaches a Berkley packet filter to the socket to only read UDP, TCP, and SCTP traffic through ports 22 (ssh), 80 (HTTP), and 443 (HTTPS).
Any firewall restrictions present on the hacked machine will not impact this sniffing activity because BPFDoor runs at such a low level that they are not enforceable.
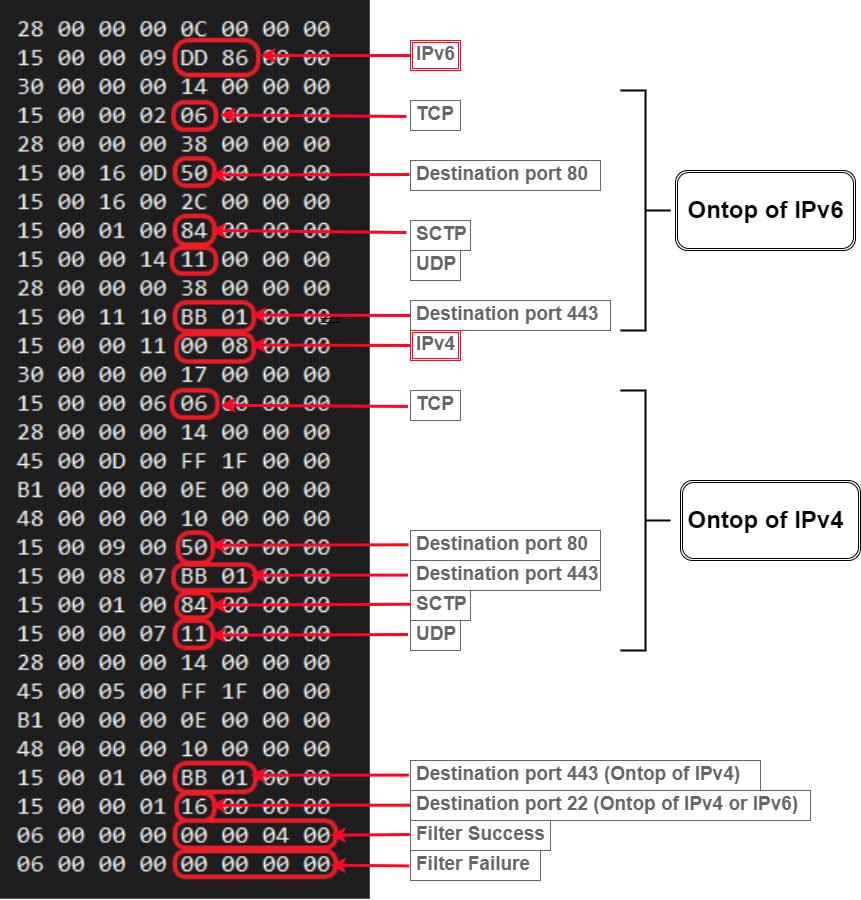
“When BPFdoor finds a packet containing its ‘magic’ bytes in filtered traffic, it treats it as a message from its carrier and parses two fields and forks again,” says Deep Instinct.
“The parent process will continue and monitor the filtered traffic passing through the socket while the child will treat the previously scanned fields as a Command & Control IP-Port combination and attempt to contact it.”
After establishing a connection with the C2, the malware sets up a reverse shell and waits for a command from the server.
.png)
(deep instinct)
GMP Gate remains undetected by security software, so system administrators can only rely on vigorous monitoring of network traffic and logs, using state-of-the-art endpoint protection products, and monitor the integrity of files on “/var/run/initd.lock”.
Additionally, a May 2022 report from CrowdStrike pointed out that BPFDoor used a vulnerability from 2019 to ensure persistence on targeted systems, therefore applying available security updates is always a crucial strategy against all types of malware.
[ad_2]
Source link
