[ad_1]

The family of Android malware tracked as SpyNote (or SpyMax) experienced a sudden spike in detections in the last quarter of 2022, which is attributed to a source code leak of one of its latest, known under the name “CypherRat”.
“CypherRat” combined SpyNote’s spying capabilities, such as remote access, GPS tracking, and device status and activity updates, with banking Trojan functionality who impersonate banking institutions to steal account credentials.
CypherRat was sold via private Telegram channels from August 2021 to October 2022, when its author decided to publish its source code on GitHub, following a series of scam incidents on hacking forums that posed as for the project.
Threat actors quickly seized the source code of the malware and launched their own campaigns. Almost immediately, custom variants emerged targeting reputable banks like HSBC and Deutsche Bank.
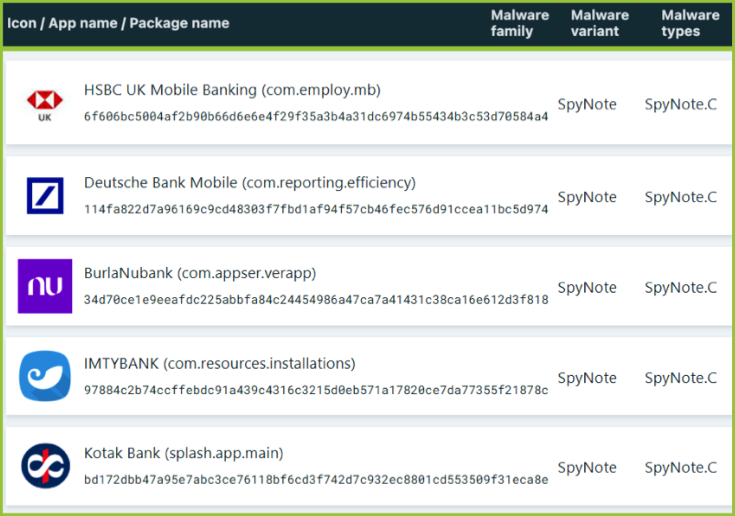
In parallel, other players have chosen to hide their versions of CypherRat in Google Play, WhatsApp and Facebook, targeting a wider audience.
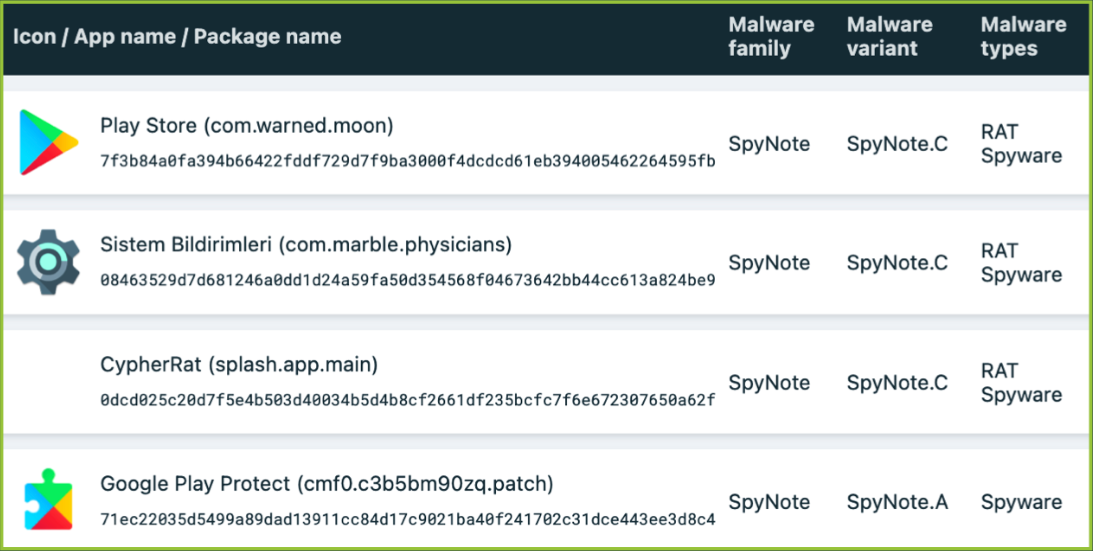
This activity was observed by ThreatFabric Analystswhich warn of the possibility of CypherRat becoming an even more widespread threat.
SpyNote Malware Features
All variants of SpyNote in circulation rely on requesting access to Android’s Accessibility Service for permission to install new apps, intercept SMS messages (for 2FA bypass), spy on calls, and record video and audio on the device.
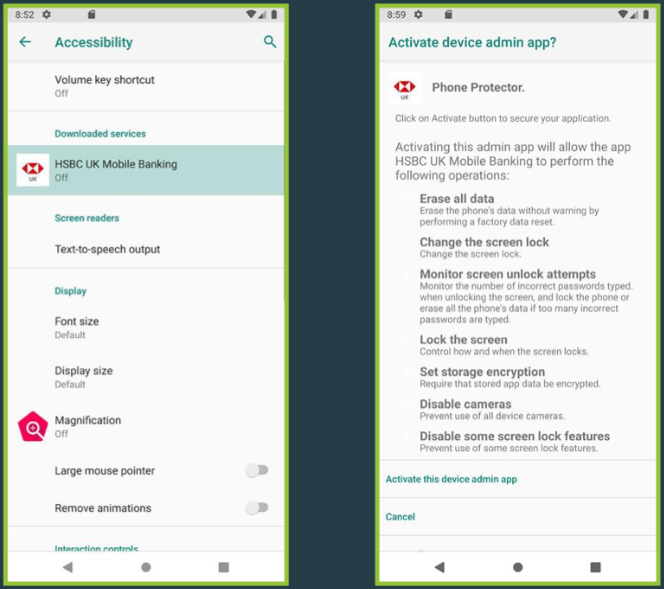
ThreatFabric lists the following features as “standout”:
- Use camera API to record and send camera videos to C2 server
- GPS and network location information
- Steal credentials from Facebook and Google accounts.
- Use Accessibility (A11y) to extract codes from Google Authenticator.
- Use Accessibility Services powered keylogging to steal banking credentials.
To hide its malicious code from scrutiny, the latest versions of SpyNote employ string obfuscation and use commercial packers to wrap APKs.
Additionally, all information exfiltrated from SpyNote to its C2 server is masked using base64 to mask the host.
Threat actors currently use CypherRat as a banking Trojan, but the malware could also be used as spyware in targeted low-volume spying operations.
ThreatFabric believes SpyNote will continue to pose a risk to Android users and believes that various forks of the malware will appear as we move forward into 2023.
Although ThreatFabric has not shared how these malicious apps are distributed, they are likely spread via phishing sites, third-party Android app sites, and social media.
For this reason, users are advised to exercise extreme caution when installing new apps, especially from outside Google Play, and to reject requests for permission to access the accessibility service.
Unfortunately, despite Google continuous efforts To stop abuse of Accessibility Service APIs by Android malware, there is still ways around restrictions imposed.
[ad_2]
Source link
