[ad_1]

A signed Windows driver has been used in attacks against banks in French-speaking countries, likely by a malicious actor who stole over $11 million from various banks.
The activity and targets match the profile of OPERA1ER hackers who have been credited with at least 35 successful attacks between 2018 and 2020.
The gang is believed to have French-speaking members and operates from Africa, targeting organizations in the region, although it also hits businesses in Argentina, Paraguay and Bangladesh.
Bluebottle TTPs point to OPERA1ER
In a report released today, researchers from Symantec, a division of Broadcom Software, reveal details about the activity of a cybercriminal group they track under the name Bluebottle that shares significant similarities with the tactics, techniques and procedures (TTP) of the OPERA1ER gang.
OPERA1ER’s campaigns were documented by cybersecurity firm Group-IB in a lengthy report published in early November 2022, where researchers note the lack of custom malware and heavy use of readily available tools (open source, commodity, frameworks) .
Symantec’s report adds some technical details, such as the use of the GuLoader tool to load the malware and a signed driver (kernel mode) that helps the attacker kill security product processes running on the victim network .
Researchers say the malware had two components, “a control DLL that reads a list of processes from a third file, and a signed ‘helper’ driver controlled by the first driver and used to terminate processes. from the list”.
It seems that the signed malicious driver has been used by several cybercriminal groups to disable the defense. Mandiant and Sophos reported in mid-December in a list that included verified kernel-mode drivers with Authenticode signatures from Microsoft’s Windows Hardware Development Program.
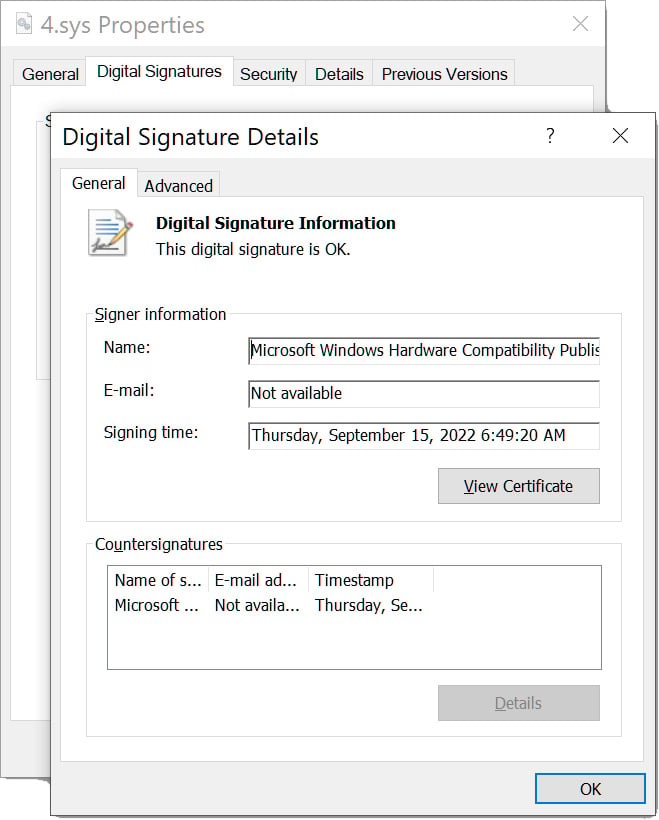
Source: BleepingComputer
Mandiant follows the driver like POVERTYclaiming that the first sign of it dates back to June 2022 and that it was used with a mixture of certificates, some of them stolen and popular among cybercriminals.
The version found by Symantec researchers, although the same driver, was signed with a digital certificate from the Chinese company Zhuhai Liancheng Technology Co., Ltd.
This shows that cybercriminals have vendors who can provide legitimate trusted entity signatures so that their malicious tools can pass verification mechanisms and avoid detection.
The researchers note that the same driver was used in activity suspected of leading to a ransomware attack against a non-profit entity in Canada.
Symantec says the Bluebottle activity they saw was as recent as July 2022 and extended through September. However, it is possible that some of them probably started a few months earlier, in May.
Recent attacks also show new TTPs, which include the use of GuLoader in the early stages of the attack. Additionally, researchers have seen indications that the threat actor was using ISO disk images as an initial infection vector in job-themed spear-phishing.
“However, the July Jobs-themed malware was observed in paths suggesting that it had been mounted as a CD-ROM. This could indicate that a genuine disc was inserted, but it may also be that a malicious ISO file was delivered to victims and mounted” – Symantec
Symantec researchers analyzed Bluebottle attacks against three different financial institutions in African countries. In one of them, the threat actor relied on several dual-purpose tools and utilities already available on the system:
- Quser for user discovery
- Ping to check internet connectivity
- Ngrok for network tunneling
- Net localgroup /add to add users
- Fortinet VPN client – probably for secondary access channel
- Xcopy to copy RDP wrapper files
- Netsh to open port 3389 in firewall
- Autoupdatebat ‘Automatic RDP Wrapper installer and updater’ tool to enable multiple concurrent RDP sessions on a system
- SC privs to change SSH agent permissions – this could have been tampering for key theft or installing another channel
Although the last activity on the victim’s network was observed in September, researchers claim that the Ngrok tunneling tool was present until November, confirming Group-IB’s findings of the OPERA1ER hackers sitting on the compromised networks for long periods (between three and twelve months).
Bluebottle also used malicious tools such as GuLoader, Mimikatz to extract passwords from memory, Reveal Keylogger to log keystrokes, and the Netwire remote access Trojan.
The threat actor began manual lateral movement activity approximately three weeks after the initial compromise, using a command prompt and PsExec.
While analysis of the attacks and tools used suggest that OPERA1ER and Bluebottle are the same group, Symantec cannot confirm that the activity they saw had the same monetization success as reported by Group-IB. .
[ad_2]
Source link
