[ad_1]

An alleged Chinese hacking campaign has targeted unpatched SonicWall Secure Mobile Access (SMA) appliances to install custom malware that establishes long-term persistence for cyber espionage campaigns.
The deployed malware is customized for SonicWall devices and is used to steal user credentials, provide shell access to attackers, and even persist through firmware upgrades.
The campaign was discovered by Beggar and SonicWall’s PSIRT team, which tracks the actor behind it as UNC4540, likely of Chinese descent.
New malware targets SonicWall devices
The malware used on SonicWall devices consists of an ELF binary, the TinyShell backdoor, and several bash scripts that show deep understanding of the targeted network devices.
“The overall behavior of the malicious bash script suite shows a detailed understanding of the appliance and is well-suited to the system for stability and persistence,” Mandiant explains.
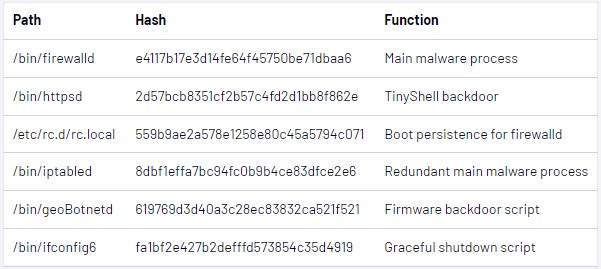
The main module, named “firewalld”, executes SQL commands against the appliance database to steal the hashed credentials of all logged in users.
The stolen credentials are copied to a text file created by the attacker at ‘tmp/syslog.db’ and then recovered to be hacked offline.
Additionally, firewalld launches other malicious components, like TinyShell, to establish a reverse shell on the appliance for easy remote access.
Finally, the main malware module also adds a small patch to the legitimate “fire-based” SonicWall binary, but Mandiant researchers could not determine its exact purpose.
Analysts speculate that this modification helps the stability of the malware when the shutdown command is entered on the device.
While it’s unclear which vulnerability was used to compromise the devices, Mandiant says the targeted devices weren’t patched, likely making them vulnerable to older flaws.
Recent flaws revealed by SonicWall [1, 2, 3] that impacted SMA devices allowed unauthenticated access to devices, which could then be used in campaigns like this.
Persistence and resilience
Mandiant says there are signs that the malware has been installed on systems examined since 2021 and has persisted through several subsequent firmware updates on the appliance.
Threat actors have achieved this by using scripts that provide redundancy and ensure long-term access to hacked devices.
For example, there is a script called “iptabled” which is essentially the same module as firewalld but will only be called by the startup script (“rc.local”) if the main malware process terminates, hangs, or cannot be launched.
Additionally, the attackers implemented a process where a bash script (“geoBotnetd”) checks for new firmware updates in “/cf/FIRMWARE/NEW/INITRD.GZ” every 10 seconds. If found, the malware injects itself into the upgrade package to survive even after firmware upgrades.
The script also adds a backdoor user named “acme” on the upgrade file so that they can retain access after applying the firmware update to the hacked appliance.
System administrators are advised to apply the latest security updates provided by SonicWall for SMA100 appliances.
The recommended target version at the moment is 10.2.1.7 or higher, which includes File Integrity Monitoring (FIM) and Abnormal Process Identification, which should detect and stop this threat.
This campaign shares many similarities with recent attacks that targeted a zero-day vulnerability in Fortinet SSL-VPN devices used by government organizations and government-related targets.
Similar to the SonicWall campaign, the threat actors behind the Fortinet attacks showed intimate knowledge of the devices and how they functioned to inject custom malware for persistence and data theft.
“In recent years, Chinese attackers have deployed several zero-day exploits and malware for a variety of Internet-connected network devices as a route for full enterprise intrusion, and the instance reported here does part of a recent pattern that Mandiant expects to continue in the near term,” Mandiant warns in the report.
[ad_2]
Source link
