[ad_1]

Slack suffered a security incident over the holidays affecting some of its private GitHub code repositories.
The immensely popular Salesforce-owned IM app is used by approximately 18 million users in workplaces and digital communities around the world.
Customer data is not affected
BleepingComputer encountered a security incident notice issued by Slack on December 31, 2022.
The incident involves threat actors accessing Slack’s externally hosted GitHub repositories through a “limited” number of stolen Slack employee tokens.
Although some of Slack’s private code repositories have been hacked, Slack’s core codebase and customer data remains unchanged, according to the company.
The wording of the notice [1, 2] released on New Year’s Eve is as follows:
“On December 29, 2022, we were notified of suspicious activity on our GitHub account. Upon investigation, we discovered that a limited number of Slack employee tokens had been stolen and misused to gain access to our repository. Externally hosted GitHub Our investigation also revealed that the threat actor uploaded private code repositories on December 27. None of the uploaded repositories contained customer data, means to access customer data, or the database. Slack main code.
Slack has since invalidated the stolen tokens and says it is investigating the “potential impact” on customers.
At this time, there is no indication that sensitive areas of the Slack environment, including production, have been accessed. As a precaution, however, the company has been spinning relevant secrets.
“Based on information currently available, the unauthorized access did not result from an inherent vulnerability in Slack. We will continue to investigate and monitor for any additional exposures,” Slack’s security team says.
Hidden Search Engine Security Update
Ironically, the security update talks about Slack taking your “security, privacy, and transparency very seriously”, and nevertheless comes with some caveats.
To begin with, this “news” article does not appear on the society international news blog aside from other articles, at the time of writing.
Also, unlike previous Slack blog posts, this update (when available in certain regions, e.g. UK) is marked with ‘no index‘—an HTML feature used to deliberately exclude a web page from search engine results, making it more difficult, if not impossible, to discover the page.
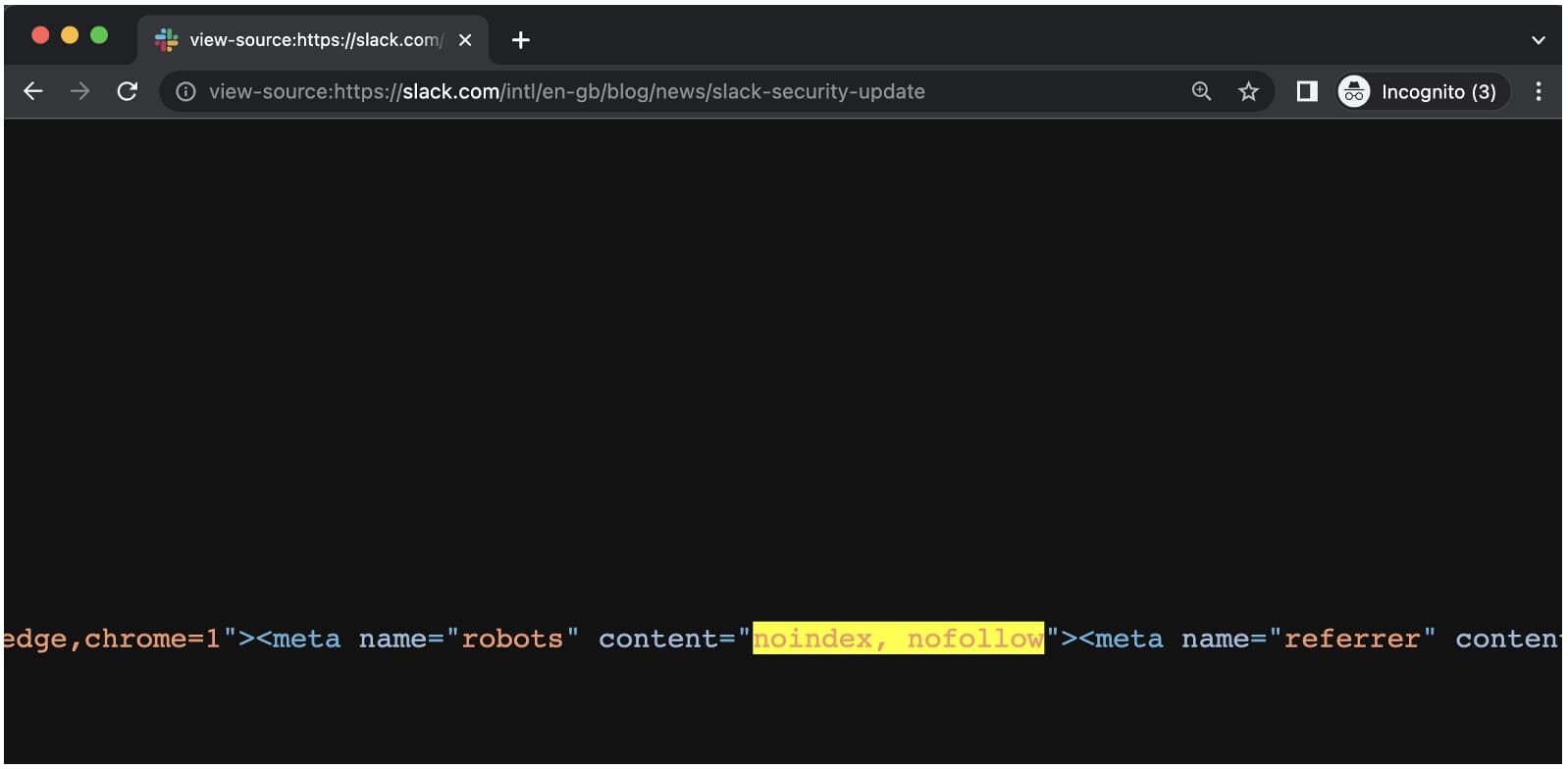
BleepingComputer further observed that the “meta” tag containing the “noindex” attribute was itself placed downward in the page’s HTML, in an elongated line that overflows without breaking. This means that source code viewers (like us) wouldn’t easily see the buried tag unless they actively search (Ctrl+F) the source code for it. By convention, HTML head and meta tags are usually placed at the top of a page.
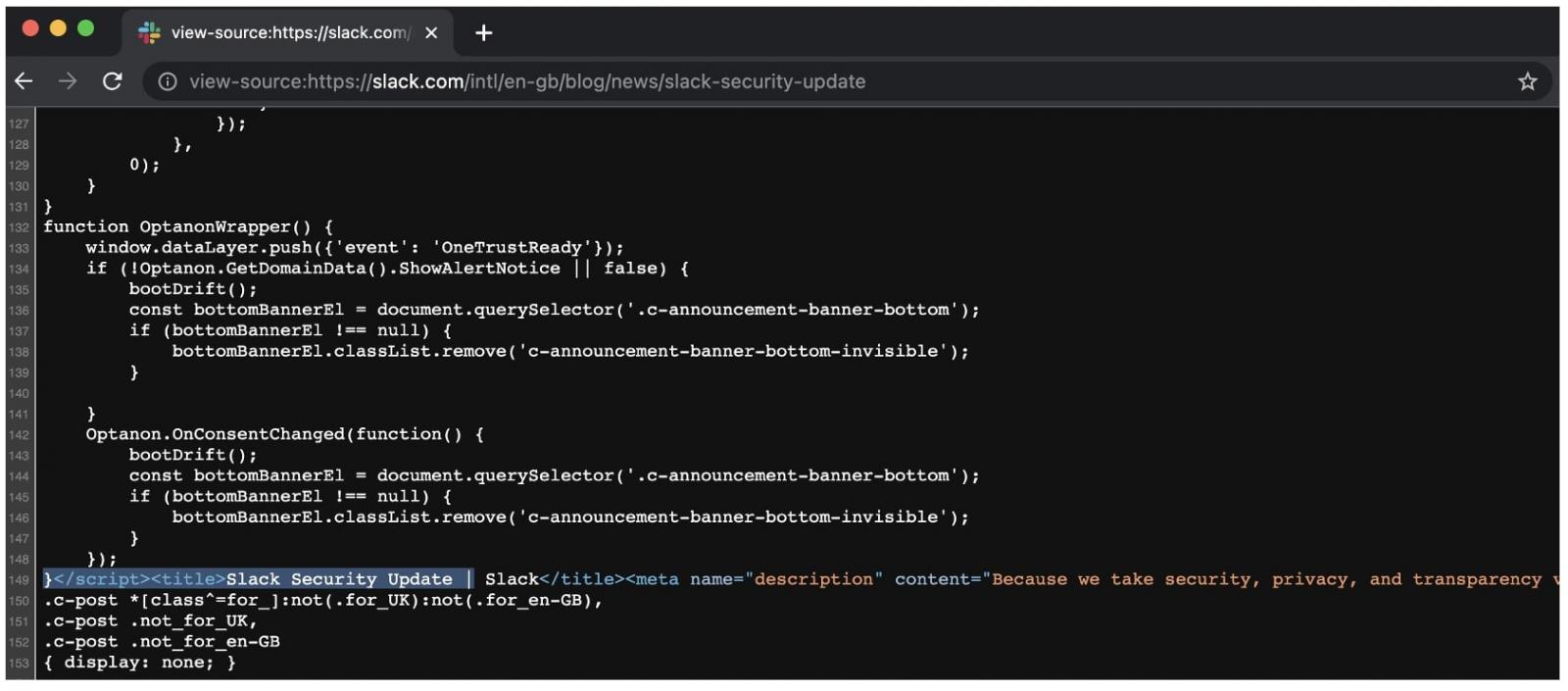
However, we noticed that Google has already indexed the American notice published without the label.
Other techniques employed by companies seeking to limit the visibility of strange news may include the use of geo-fence and adapting the robots.txt case. Such techniques, including the use of “noindex” in prominent announcements, are generally frowned upon.
Last year, journalist and infosec editor Zack Whittaker called LastPass and GoTo for using similar tactics with LastPass’ Disclosure of security vulnerabilities 2022.
In August 2022, Slack resets user passwords after accidentally exposing their password hashes in a separate incident. Unsurprisingly, this particular notice is also marked with a “noindex” (the American version as well).
In 2019, Slack announced that it had reset passwords for approximately 1% of users affected by the 2015 data breach who additionally met a defined criterion.
The good news for the most recent security update is that there is no action for customers to take at this time.
[ad_2]
Source link
