[ad_1]

Organizations are rapidly adopting the cloud as they rely heavily on data and technology to drive their business. These organizations use highly scalable cloud services that manage compute, storage, and networking operations.
A cloud workload is a computing asset that runs in a cloud environment and consumes resources. Examples of cloud workloads include virtual machines, databases, microservices, storage, networks, and applications.
Cloud workload security is a practice that ensures that all cloud workloads are properly monitored and protected. We may use cloud security solutions to achieve this practice. Cloud security solutions help protect against threats targeting cloud infrastructure, thereby reducing risk, improving application reliability and ensuring regulatory compliance. Additionally, a cloud workload security solution can give an organization visibility into its cloud infrastructure.
Cloud Workload Security Challenges
- Large attack surface: The more IT resources are spread across multiple offsite locations, the larger the risk and attack surface. Having a presence in the cloud comes with the added obligation of protecting virtual servers, remote applications, containers, and network interactions between environments.
- Multi-cloud security: Most organizations use more than one cloud service provider (CSP) to increase reliability and efficiency. However, this presents a challenge because these CSPs have unique requirements when integrating cloud workload security solutions. This challenge may require organizations with multiple CSPs to monitor their workloads with different cloud security solutions. Additionally, it can be difficult to have a central overview of the organization’s overall security posture.
- Regulatory compliance: Compliance is key when it comes to sensitive information such as health and financial data. As many regulations change, businesses need to ensure their cloud service providers and infrastructure are certified to handle sensitive data.
- Misconfigurations: As cloud environments continually evolve, this increases the risk of misconfigurations that can expose organizations to attacks resulting in data breaches. For example, weak data transmission protocols and poorly configured access management systems can expose a cloud workload to intrusions. Configuration errors can occur due to cloud migration difficulties or configuration fatigue.
Importance of Cloud Workload Security Solution
A cloud security solution can protect various workload environments. When analyzing cloud workload protection, consider the following benefits:
- Vulnerability management: Cloud security solutions automate certain risk assessment and prioritization processes that will help security teams eliminate critical risks with minimal effort. When it comes to assessing workload vulnerabilities, it’s best to prioritize and patch the most serious vulnerabilities out of the thousands that emerge each year.
- Regulatory Compliance: Data privacy and security are crucial elements of an organization’s Information Security Management System (ISMS). Cloud security solutions provide robust security for the organization’s workloads to meet compliance requirements such as customer personal and financial data.
- Protection: Cloud workload security solutions protect cloud workloads against various threats, such as viruses, worms, Trojans, and sophisticated attacks. With less time between initial intrusion and lateral movement, rapid detection time is critical to an organization’s security.
- Simplified, centralized management: Cloud security solutions provide automated detection and response across an organization’s cloud environment while providing the lowest possible overhead. This allows an organization to have a single view that provides visibility into the status of workloads and overall security posture.
Wazuh for cloud security
Wazuh is a free and open source security platform that offers Unified XDR and SIEM functionality. It helps keep workloads secure across cloud and on-premises environments. It provides a centralized view to monitor, detect and alert on security events and incidents on monitored endpoints and cloud workloads.
Wazuh offers several features that organizations can implement to detect and defend against security threats. This section introduces several Wazuh features that protect workloads on cloud platforms like AWS, Azure, GCP, and Office 365. This can be achieved by installing the Wazuh agent on virtual instances or by collecting logs from cloud services through different CSP modules.
The Wazuh agent supports multiple operating systems including Windows, Linux, Solaris, BSD, and macOS. The agent collects security event data from the virtual instances and forwards these events to central Wazuh components, where log analysis, correlation, and alerting are performed.
It should be noted that Wazuh offers an out-of-the-box set of rules to detect suspicious events in all cloud solutions discussed in this section.
Monitoring AWS with Wazuh
Wazuh helps increase the security of an AWS infrastructure in two different ways that complement each other, as described below:
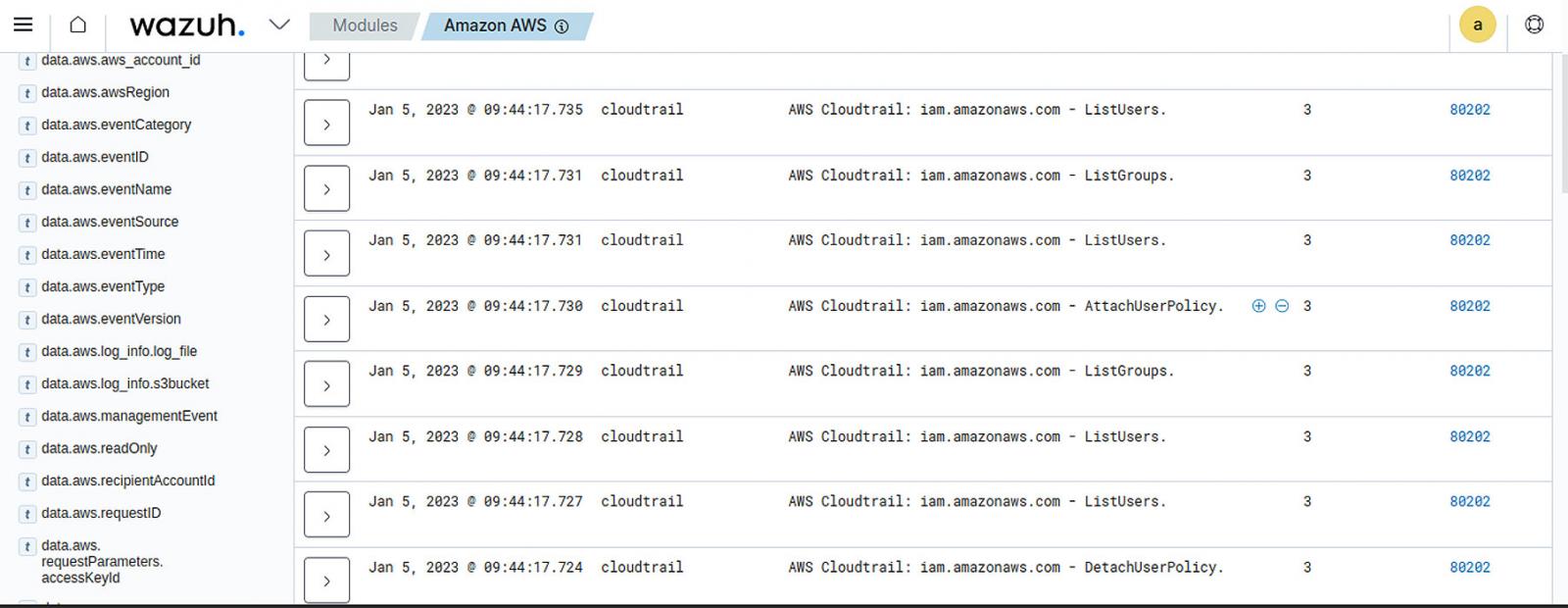
- Using the Wazuh AWS module: Wazuh can monitor AWS services to collect and analyze infrastructure log data and generate alerts based on collected events. Thanks to the AWS module, these logs provide comprehensive and detailed information about the infrastructure, such as instance configuration, unusual activities, data recorded on S3 buckets, etc. Some supported services include CloudTrail, VPC, Config, WAF, Macie, GuardDuty, CloudWatch Logs, Amazon ECR Image Scanning, Cisco Umbrella, and Trusted Advisor. Wazuh can monitor account activity in an organization’s AWS infrastructure, configuration of AWS resources, unusual API calls, and more.
To find more information about supported services and configuration options, visit the Wazuh Documentation.
Azure monitoring with Wazuh
Workloads on Microsoft Azure can be adequately protected against attacks using Wazuh in the following ways:
- Using the Wazuh Azure module: The Wazuh module for Azure enables organizations to monitor their cloud infrastructure’s activities, services, and Azure Active Directory (Azure AD). Azure Monitor Logs collects and organizes these logs and performance data. Wazuh receives these logs through the Azure Log Analytics API or by directly accessing logs stored in an Azure storage account. Please refer to the Wazuh Documentation for more information on configuration options and the different use cases you can define for effective monitoring.
Wazuh can monitor Azure AD activities to discover how Azure AD services are accessed and used. Azure AD is an identity and management service that combines essential directory services, application access management, and identity protection in a single solution. Wazuh uses Microsoft Graph REST API activity reports to monitor Azure AD. For more information, you can visit Wazuh Documentation.
Monitor GCP with Wazuh
Wazuh provides workload security monitoring on GCP by collecting and analyzing log data. You can achieve this in three ways:
- Using the Wazuh Pub/Sub integration module for GCP: The Google Cloud Pub/Sub messaging and ingestion service is commonly used for event-based systems and flow analysis. It allows applications to send and receive messages. The Wazuh module for GCP uses it to get several events from GCP services supported by Wazuh. GCP services supported by Wazuh include audited resources, DNS queries, VPC flow logs, firewall rule logging, and HTTPS load balancing logging. To Wazuh Documentation, you can find more information about these services and how Wazuh handles their logs for proper monitoring. Wazuh can monitor events such as admin activity, data access, system events, etc.
- Using the Wazuh Storage integration module for GCP: Wazuh can process storage and usage logs using the GCP-buckets module and monitor access control settings, request latency information, and more. Further information on the integration of the storage module can be found in this Documentation.
- Installing the Wazuh agent on virtual instances: The Wazuh agent helps monitor and protect virtual instances with multiple Wazuh capabilities like vulnerability detection, file integrity monitoringAnd malware detection.
Monitoring Office 365 with Wazuh
Microsoft Office 365 is a suite of collaboration and productivity cloud services offered by Microsoft. Therefore, tracking user behavior in Microsoft Office 365 can be beneficial. Microsoft Office 365 audit logs record information about system configuration changes and access events, including user, time, and location of activity.
The Wazuh module for Office 365 allows you to collect all audit logs using its API. The Office 365 Management Activity API groups events into tenant-specific content blobs based on their content type and source. The audit log allows Wazuh to monitor user activity in Exchange Online, admin activity in SharePoint Online, user and admin activity in Dynamics 365, and more. Visit Wazuh Documentation to learn more about monitoring Office 365 with Wazuh.
Conclusion
Opportunistic threat actors targeting cloud workloads take advantage of large and complicated cloud environments, requiring extensive configuration and administration. Companies should select the best cloud security technology to complement their security strategy.
Wazuh is a free and open-source SIEM and XDR solution that provides comprehensive security for organizations. As discussed in this article, Wazuh offers excellent integration flexibility with multiple cloud solution providers and offers all of its capabilities to provide robust visibility and security.
Wazuh has over 10 million annual downloads and provides extensive support to its users through ever-growing open source community.
Sponsored and written by Wazuh
[ad_2]
Source link
