[ad_1]

Russian cybersecurity firm Kaspersky claims that some iPhones in its network were hacked using an iOS vulnerability that installed malware via iMessage no-click exploits.
The delivery of the message exploits a vulnerability that leads to code execution without requiring any user interaction, causing additional malware to be downloaded from the attackers’ server.
Thereafter, the message and the attachment are erased from the device. At the same time, the payload stays behind, running with root privileges to collect system and user information and execute commands sent by attackers.
Kaspersky says the campaign started in 2019 and reports the attacks are still ongoing. The cybersecurity firm has dubbed the campaign “Operation Triangulation” and invites anyone who knows more to share information.
Malware analysis
Since it is impossible to scan iOS from the device, Kaspersky used the Mobile Verification Toolkit to create file system backups of infected iPhones to retrieve information about the attack process and function of the malware.
While the malware attempts to remove traces of the attack from devices, it still leaves signs of infection, such as system file changes that prevent iOS updates from being installed, abnormal data usage, and memory loss. injection of obsolete libraries.
The analysis revealed that the first signs of infection occurred in 2019 and the most recent iOS version infected with the malicious toolset is 15.7.
Note that the latest major version of iOS is 16.5, which may have already patched the vulnerability used in these malware attacks.
The exploit sent via iMessage triggers an unknown vulnerability in iOS to perform code execution, retrieving next steps from the attacker’s server, including elevation of privilege exploits.
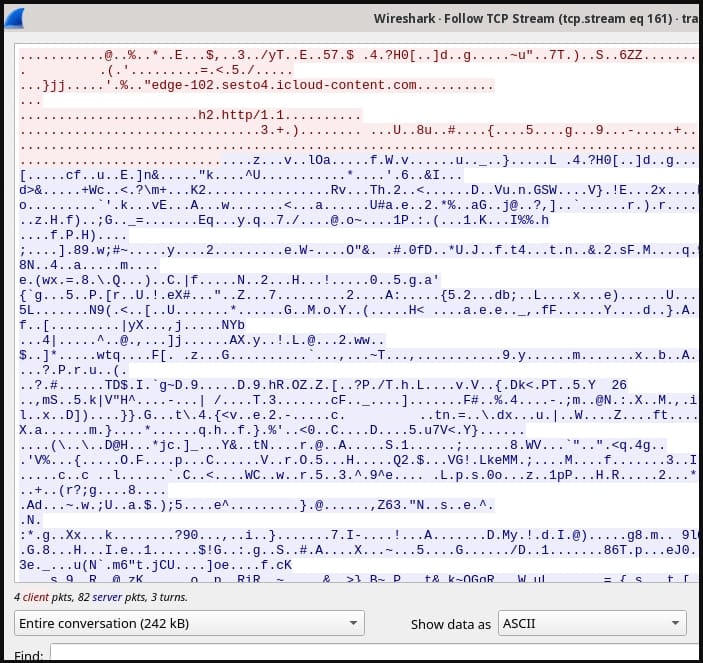
The security firm has provided a list of 15 domains associated with this malicious activity, which security administrators can use to check historical DNS logs for possible signs of exploitation on their devices.
After elevation of root privileges, the malware downloads an extensive toolset that executes commands to collect system and user information and download additional modules from the C2.
Kaspersky notes that the APT toolset dropped on the device has no persistence mechanism, so a reboot would effectively stop it.
At present, only a few details about the malware’s functions have been made public, as analysis of the final payload is still ongoing.
Russia accuses NSA of attacks
In a statement coinciding with Kaspersky’s report, Russia’s FSB intelligence and security agency says Apple deliberately provided the NSA with a backdoor it can use to infect the country’s iPhones with spyware.
THE The FSB alleges that he found malware infections on thousands of Apple iPhones belonging to Russian government officials and staff at the embassies of Israel, China and several NATO member countries in Russia.
Despite the seriousness of the allegations, the FSB has provided no evidence for its claims.
The Russian state has previously recommended that all employees and members of the Presidential Administration abandon the use of Apple iPhones and, if possible, abandon US-made technology entirely.
Kaspersky confirmed to BleepingComputer that the attack affected its headquarters in Moscow and employees in other countries. Still, the company said it was unable to verify a link between its findings and the FSB report because it does not have the technical details of the government investigation.
However, the Russian CERT has published an alert linking the FSB statement to the Kaspersky report.
BleepingComputer has contacted Apple to request comment on Kaspersky’s findings and FSB allegations, but we are still awaiting a response.
[ad_2]
Source link
