[ad_1]

The APT37 threat group uses new evasive malware “M2RAT” and steganography to target individuals for intelligence gathering.
APT37, also known as “RedEyes” or “ScarCruft”, is a North Korean cyber espionage and hacking group believed to be state-backed.
In 2022, the hacking group was seen exploiting Internet Explorer Zero Days and the distribution of a wide assortment of malware against targeted entities and individuals.
For example, threat actors have targeted EU-based organizations with a new version of their mobile backdoor named “Dolphin,’ deployed a custom RAT (Remote Access Trojan) called ‘Konni,’ and targeted US journalists with highly customizable malware named ‘golden backdoor.’
In a new report released today by AhnLab Security Emergency Response Center (ASEC), researchers explain how APT37 now uses a new strain of malware called “M2RAT” which uses a shared memory section for commands and data exfiltration and leaves very little operational traces on the infected machine.
Start with phishing
The recent attacks observed by ASEC began in January 2023, when the hacking group sent phishing emails containing a malicious attachment to their targets.
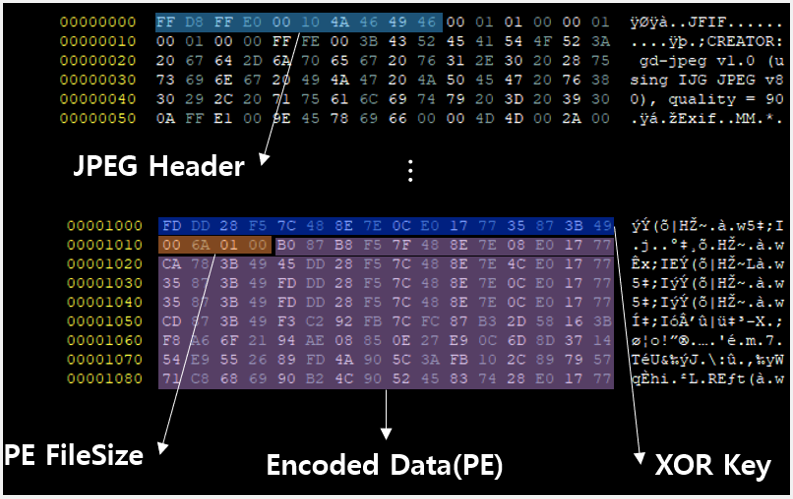
Opening the attachment triggers the exploitation of an old EPS vulnerability (CVE-2017-8291) in the Hangul word processor commonly used in South Korea. The exploit will cause shellcode to execute on a victim’s computer that downloads and executes a malicious execution stored in a JPEG image.
This JPG image file uses steganography, a technique for hiding code inside files, to sneak the M2RAT executable (“lskdjfei.exe”) onto the system and inject it into “explorer.exe” .
For persistence on the system, the malware adds a new value (“RyPO”) in the “Run” registry key, with commands to run a PowerShell script via “cmd.exe”. This same command was also seen in a Kaspersky Report 2021 about APT37.
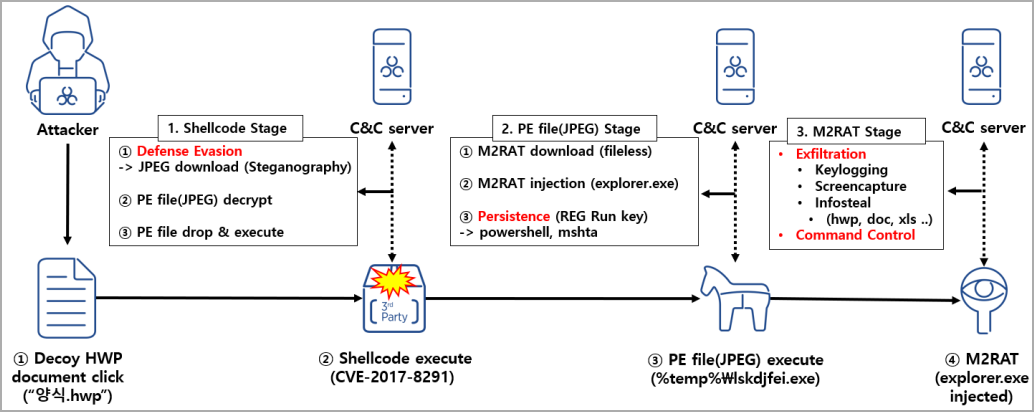
M2RAT steals Windows and phones
The M2RAT backdoor acts as a basic remote access Trojan that performs keylogging, data theft, command execution and screenshot taking from the desktop.
The screen capture function is activated periodically and works autonomously without requiring a specific command from the operator.
The malware supports the following commands, which collect information from the infected device and then send it back to the C2 server for attackers to examine.
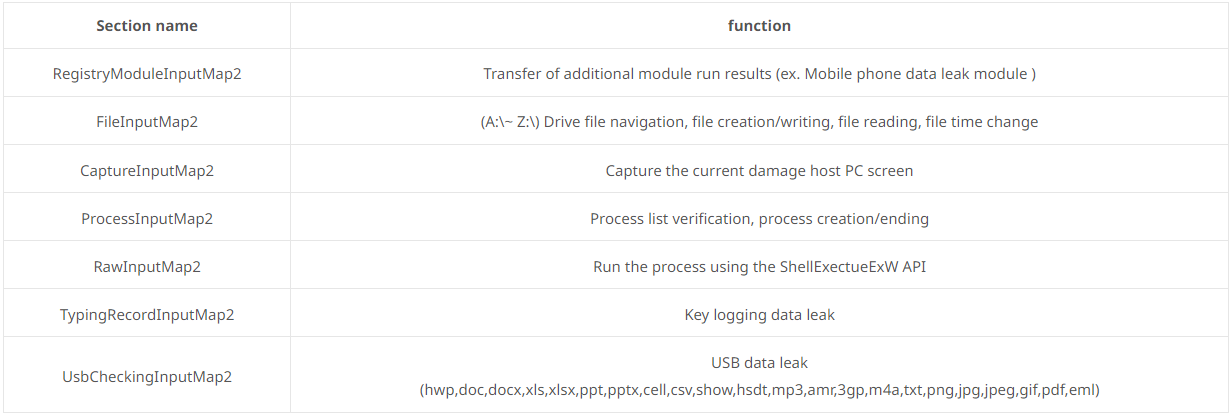
Of particular interest is the ability of the malware to search for portable devices connected to the Windows computer, such as smartphones or tablets.
If a portable device is detected, it scans the contents of the device for documents and voice recording files and, if found, copies them to the PC for exfiltration to the attacker’s server .
Prior to exfiltration, the stolen data is compressed into a password-protected RAR archive, and the local copy is erased from memory to eliminate all traces.
Another interesting feature of M2RAT is that it uses a shared memory section for command and control (C2) communication, data exfiltration and direct transfer of stolen data to the C2 without storing it in the compromised system .
Using a memory section on the host for the above functions minimizes swapping with the C2 and makes analysis more difficult, as security researchers have to scan the memory of infected devices to retrieve commands and data used by the malware.
In conclusion, APT37 continues to refresh its custom toolset with evasive malware that is difficult to detect and analyze.
This is especially true when the targets are individuals, as in the recent campaign spotted by ASEC, who lack the sophisticated threat detection tools of large organizations.
[ad_2]
Source link
