[ad_1]
Several malicious botnets actively target Cacti and Realtek vulnerabilities in campaigns detected between January and March 2023, spreading ShellBot and Moobot malware.
The targeted flaws are CVE-2021-35394, a critical remote code execution vulnerability in the Realtek Jungle SDK, and CVE-2022-46169, a critical command injection flaw in the management monitoring tool. Cacti breakdowns.
Both flaws have been exploited by other botnet malware in the past, including Fodcha, RedGoBot, MiraiGafgyt and Mozi.
Fortinet reports that the volume of malicious activity in 2023 is significant, targeting exposed network devices to enlist them in DDoS (distributed denial of service) swarms.
Although Fortinet’s report does not explicitly state whether the same threat actors are spreading Moobot and ShellBot, payloads have been observed exploiting the same flaws in overlapping bursts of attacks.
Moobot infections
Moobot, a variant of Mirai, was first discovered in December 2021, targeting Hikvision cameras. In September 2022, it was update to target multiple D-Link RCE flaws.
Currently, it targets CVE-2021-35394 and CVE-2022-46169 to infect vulnerable hosts, then downloads a script containing its configuration and establishes a connection to the C2 server.
Moobot continues to exchange heartbeat messages until it recognizes an incoming command, which is when it launches its attack.
A notable feature of newer versions of Moobot is their ability to seek out and kill the processes of other known bots so that they can harvest the infected host’s maximum hardware power to launch DDoS attacks.
ShellBot Attacks
ShellBot was first spotted in January 2023 and continues to be active today, primarily targeting the Cacti flaw. Fortinet has captured three variants of malware, indicating that it is being actively developed.
The first variant establishes communication with the C2 and waits for the reception of one of the following commands:
- ps – perform a port scan on the specified target and port
- nmap – perform an Nmap port scan on a specified port range
- rm – delete files and folders
- version – send version information
- down – download a file
- UDP – launch a UDP DDoS attack
- back – inject an inverted shell
The second variant of ShellBot, which first appeared in March 2023 and already has hundreds of victims, offers a much more extensive set of commands, as shown below:
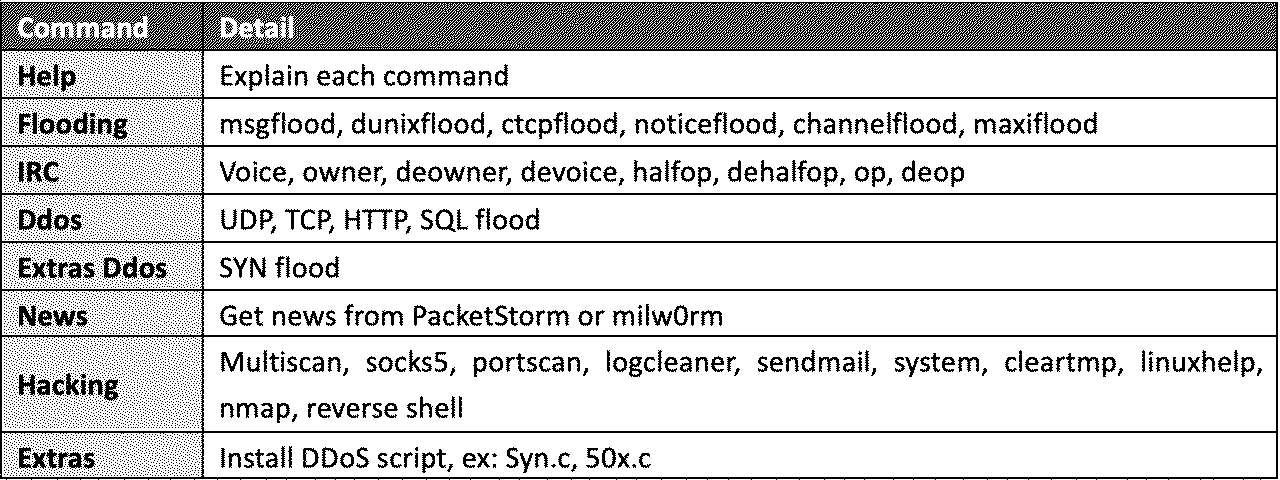
Interestingly, the malware has an exploit enhancement module that aggregates news and public notices from PacketStorm and milw0rm.
The recommended action to defend against Mootbot and ShellBot is to use strong administrator passwords and apply security updates that address the mentioned vulnerabilities.
If your device is no longer supported by its vendor, it must be replaced with a newer model to receive security updates.
[ad_2]
Source link
