[ad_1]

The operators of the StrRAT and Ratty remote access Trojans are launching a new campaign using polyglot MSI/JAR and CAB/JAR files to evade detection by security tools.
The campaign was spotted by deep instinct, which reports that threat actors have moderate success in evading detection by antivirus engines. This is remarkable given the age and documentation of the two RATs in particular.
Polyglot files combine two or more file formats in a way that allows them to be interpreted and launched by several different applications without error.
Threat actors have been using polyglot files to hide malicious code, confuse security solutions, and circumvent protections for several years now.
More recently, we reported that this technique was employed by the StrelaStealer Malware which targets Outlook and Thunderbird accounts.
Despite Microsoft’s efforts to address the issue by implementing a signature-based detection system, there are ways around this protection, so polyglot files continue to be used for malicious purposes.
RAT Polyglot Campaign
A notable case that was employed since 2018which is also what Deep Instinct observed in the last RAT distribution campaign, is the combination of JAR and MSI formats in a single file.
JAR files are archives identified as such by a record at their end, while in MSI the file type identifier is a “magic header” at the beginning of the file, so hackers can easily combine the two formats in one file.
This dual format allows them to be run as MSI in Windows and also run as a JAR file by the Java runtime.
JAR files are not executables, so they are not checked as vigorously by anti-virus tools. Unfortunately, this allows them to hide the malicious code and trick the AV into analyzing the MSI part of the file, which should come out clean.
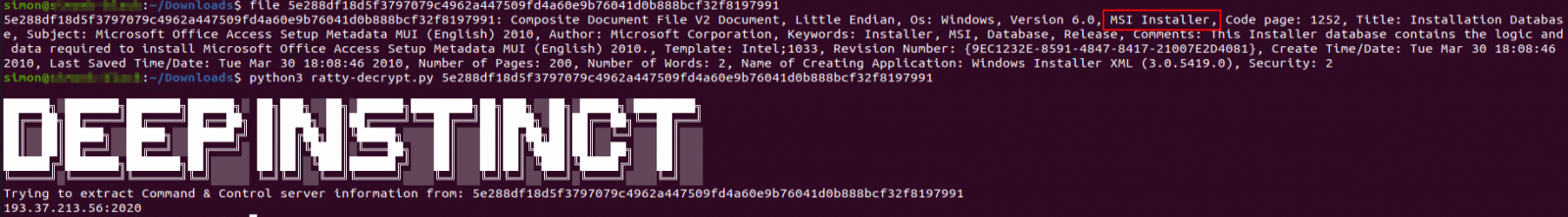
Deep Instinct has noticed CAB/JAR combinations instead of MSI in other cases involving the same two RAT families. CABs are also good candidates for polyglot combinations with JARs because they also feature a magic header for file type interpretation.
The polyglots used in this campaign are served by Sendgrid and URL shortening services like Cutt.ly and Rebrand.ly, while the retrieved StrRAT and Ratty payloads are stored in Discord.
In terms of detection, CAB/JAR polyglots return six positives out of 59 AV engines on Virus Total, while 30 security vendors identify MSI/JAR polyglots. Thus, the detection rate varies between 10% and 50%.
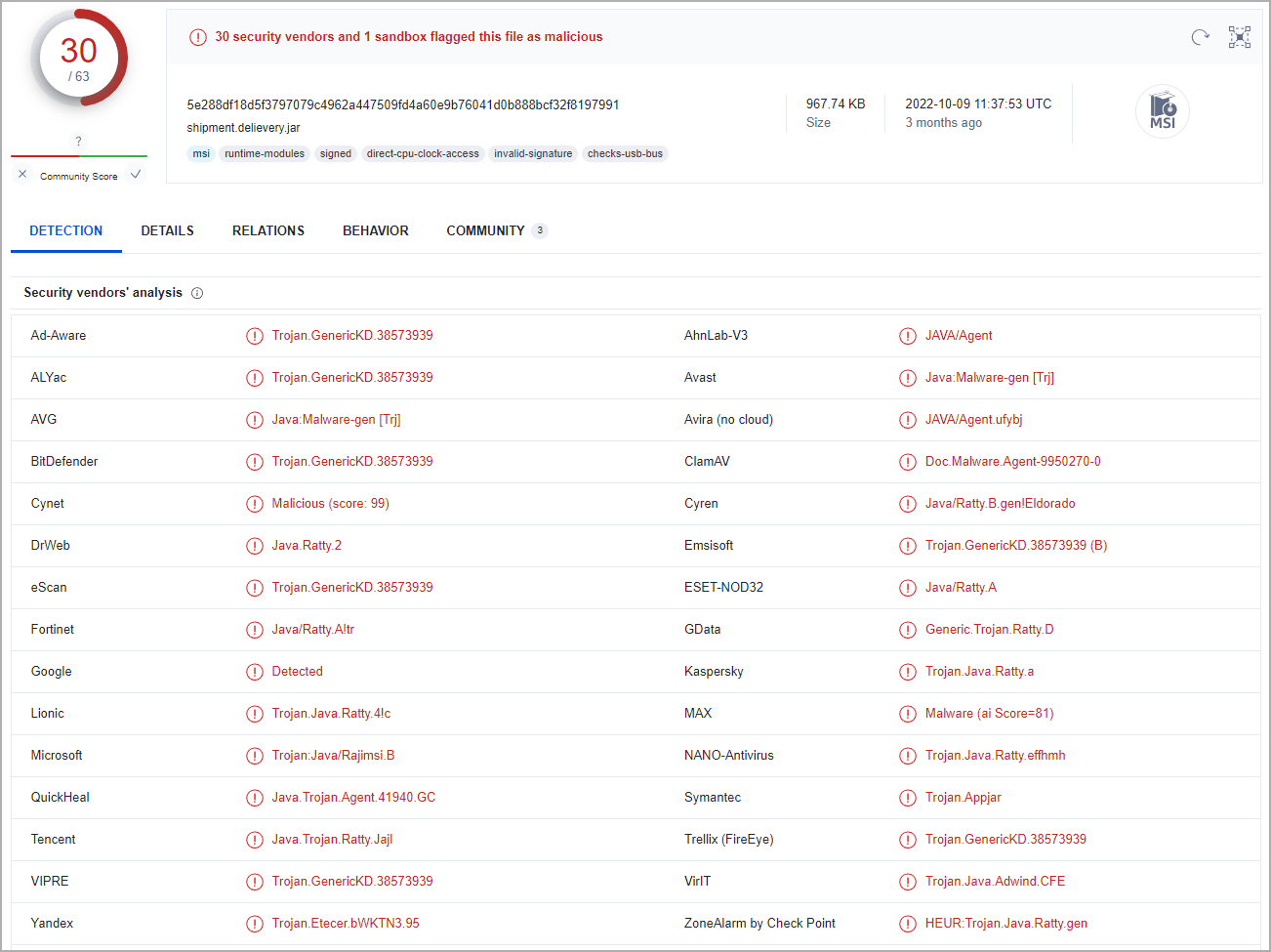
Deep Instinct reports that many polyglots reviewed for StrRAT and Ratty use the same C2 address and are hosted by the same Bulgarian hosting company.
It is therefore possible that the two strains are used in the same campaign carried out by the same operator.
[ad_2]
Source link
