[ad_1]
Raspberry Robin malware is now trying its hand at trickery by dropping a fake payload to confuse researchers and evade detection when it detects that it is running in sandboxes and debugging tools.
This new tactic was discovered by Trend Micro researchers who observed Raspberry Robin in recent attacks against telecommunications service providers and government systems.
Raspberry Robin is a worm-like malware dropper that sells initial access to compromised networks to ransomware gangs and malware operators. He was previously associated with END11 and the Clop gangas well as Bumblebee, IcedID and TrueBot payload distribution.
The malware reaches the targeted systems through malicious USB drives which infect the device with malware when inserted and included. The .LNK file is double-clicked.
When the shortcut is executed, it abuses the legitimate Windows executable “MSIExec.exe” to download a malicious MSI installer that installs Raspberry Robin payloads.
.png)
Double trouble
The malware is heavily obfuscated to hide its code from anti-virus programs and security researchers, with multiple layers containing hard-coded values to decrypt the next one.
However, to make it even more difficult for security researchers to analyze the malware, Raspberry Robin has started dropping two different payloads depending on how it is executed on a device.
If the malware detects that it is running in a sandbox, indicating that it is likely being scanned, the loader drops a fake payload. Otherwise, it will launch genuine Raspberry Robin malware.
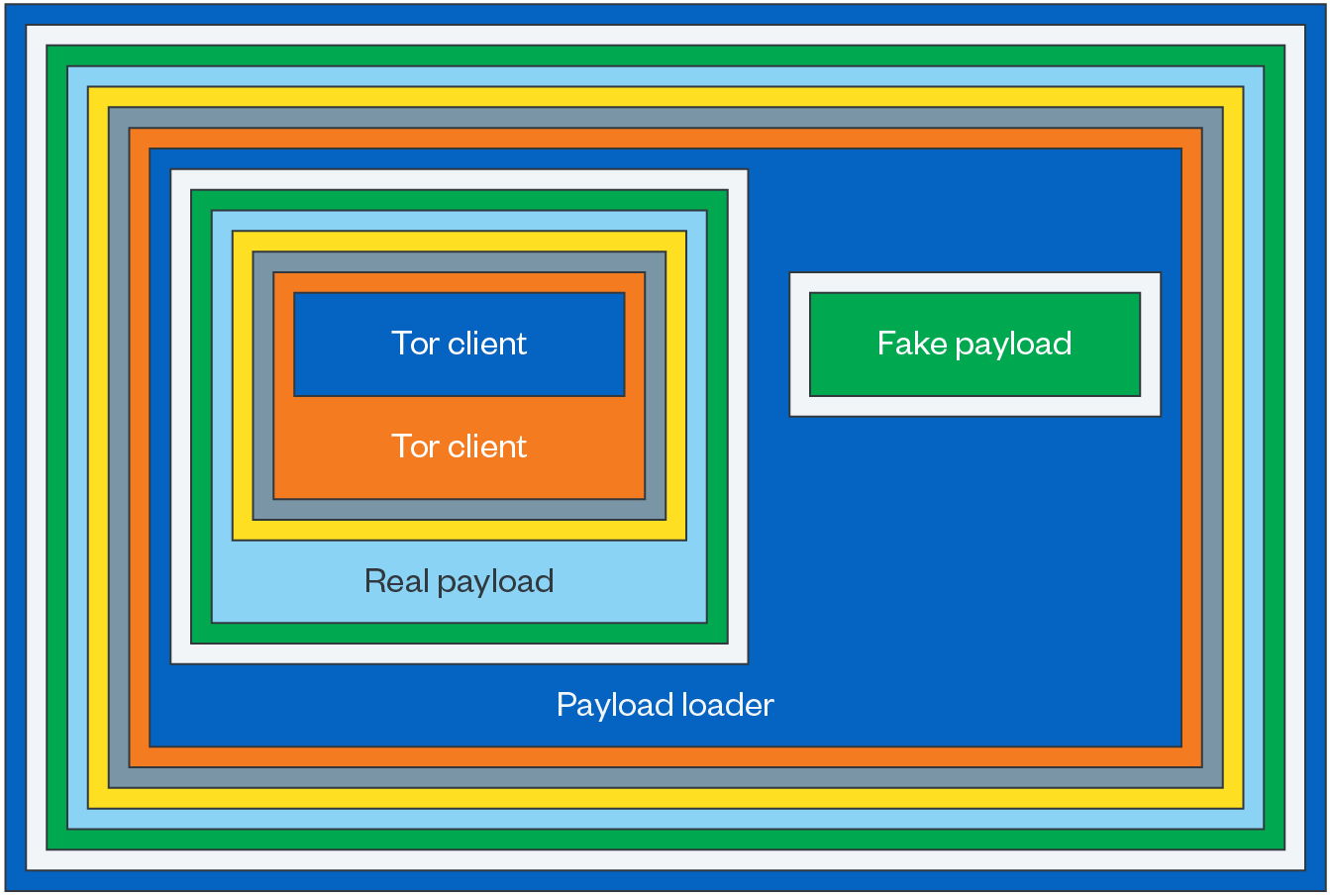
This fake payload has two additional layers, a shellcode with an embedded PE file and a PE file with the MZ header and PE signature removed.
While running, it attempts to read the Windows registry for infection markers and then proceeds to collect basic system information.
Next, the fake payload tries to download and run an adware named “BrowserAssistant”, to trick the analyst into believing that it was the final payload.
On valid systems, however, the actual Raspberry Robin malware payload is loaded, which includes a built-in custom Tor client for internal communication.
Even with the payload trick, the actual payload is filled with ten layers of obfuscation, making it much harder to analyze.
On launch, it checks if the user is admin, and if not, it uses the ‘ucmDccwCOM method in UACMe‘ Privilege escalation technique to gain administrative privileges.
The malware also modifies the registry for persistence between reboots, using two different methods for each case (administrator or not).
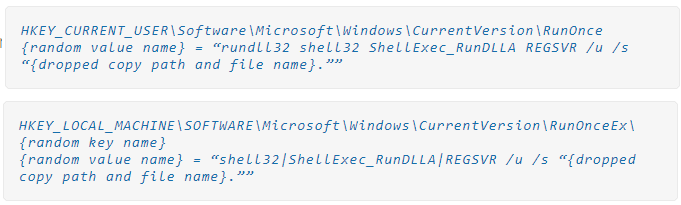
“After dropping a copy of himself, he runs the dropped copy as an administrator using a UAC (User Account Control) bypass technique”, Trend Micro explains about the privilege escalation process.
“It implements a variant of the ucmDccwCOMMethod technique in UACMe, thereby abusing the built-in Windows AutoElevate backdoor.”
Once ready, the malware attempts to connect to hardcoded Tor addresses and establishes an information exchange channel with its operators.
The Tor client process uses names that mimic standard Windows system files such as “dllhost.exe”, “regsvr32.exe”, and “rundll32.exe”.
Notably, the main routine runs in session 0, a specialized Windows session reserved exclusively for services and applications that don’t need or shouldn’t have user interaction.
As part of its infection process, Raspberry Robin will also copy itself to any attached USB drives to infect other systems.
LockBit ransomware shares similarities
Trend Micro analysts comment that recent additions in Raspberry Robin’s TTPs (tactics, techniques, and procedures) have similarities to LockBit, so the two projects might be related.
The two main similarities are using the ICM calibration technique for privilege escalation and the ‘TreadHideFromDebugger’ tool for anti-debugging.
Although these findings are notable, they do not constitute proof of a link between the two, but they could serve as a reference in future research.
In conclusion, Trend Micro asserts that the current Raspberry Robin campaign is more of a reconnaissance effort to assess the effectiveness of new mechanisms rather than the first stage of actual attacks.
[ad_2]
Source link
