[ad_1]
Data from the first half of the year indicates that ransomware activity is on track to break previous records, with an increase in the number of payments large and small.
According to a report by a blockchain analytics company On-chain analysisransomware is the only category of cryptocurrency crime to see an increase this year, all others including hacks, scams, malware, abuse hardware sales, fraud shops and revenue from the darknet market, registering a sharp decline.
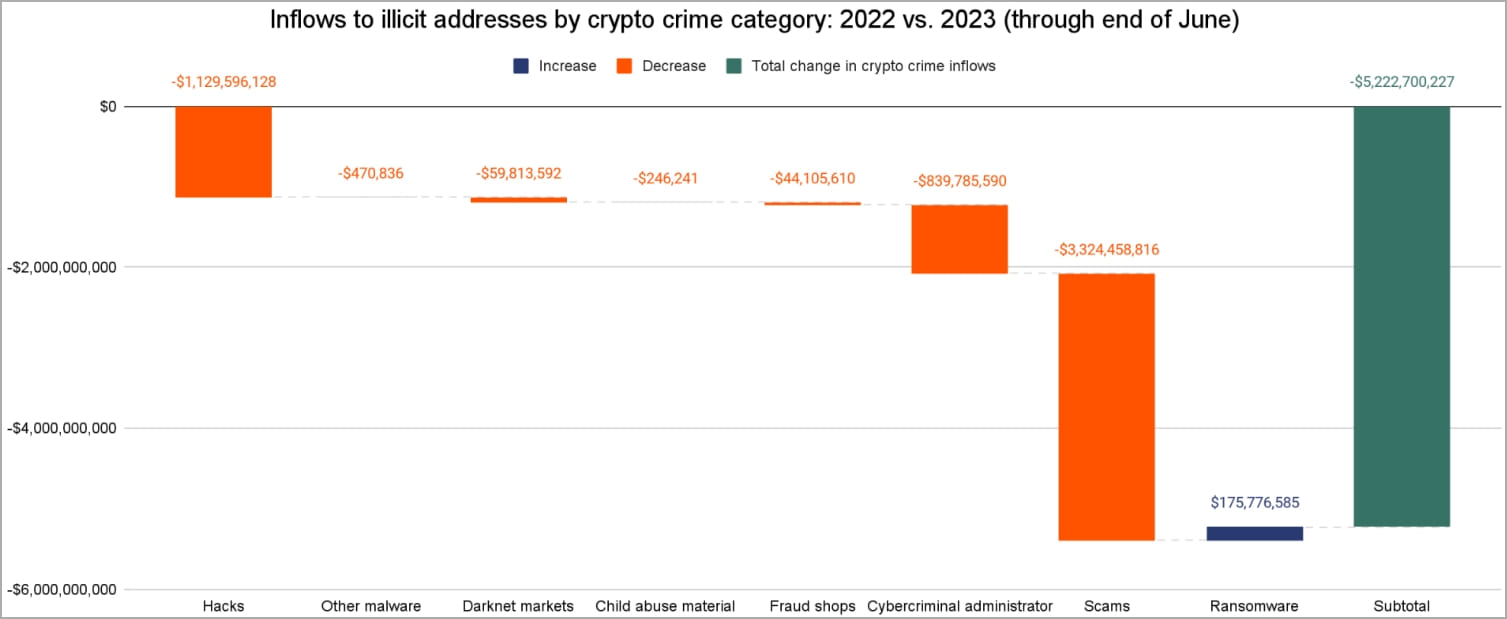
“Ransomware is the only form of cryptocurrency-based crime on the rise so far in 2023,” reads the Chainalysis report.
“In fact, ransomware attackers are about to have their second biggest year ever, having extorted at least $449.1 million through June.”
As shown in the graph below by Chainalysis, the cumulative annual ransomware revenue for 2023 reached 90% of the total 2022 figure in the first half of the year.
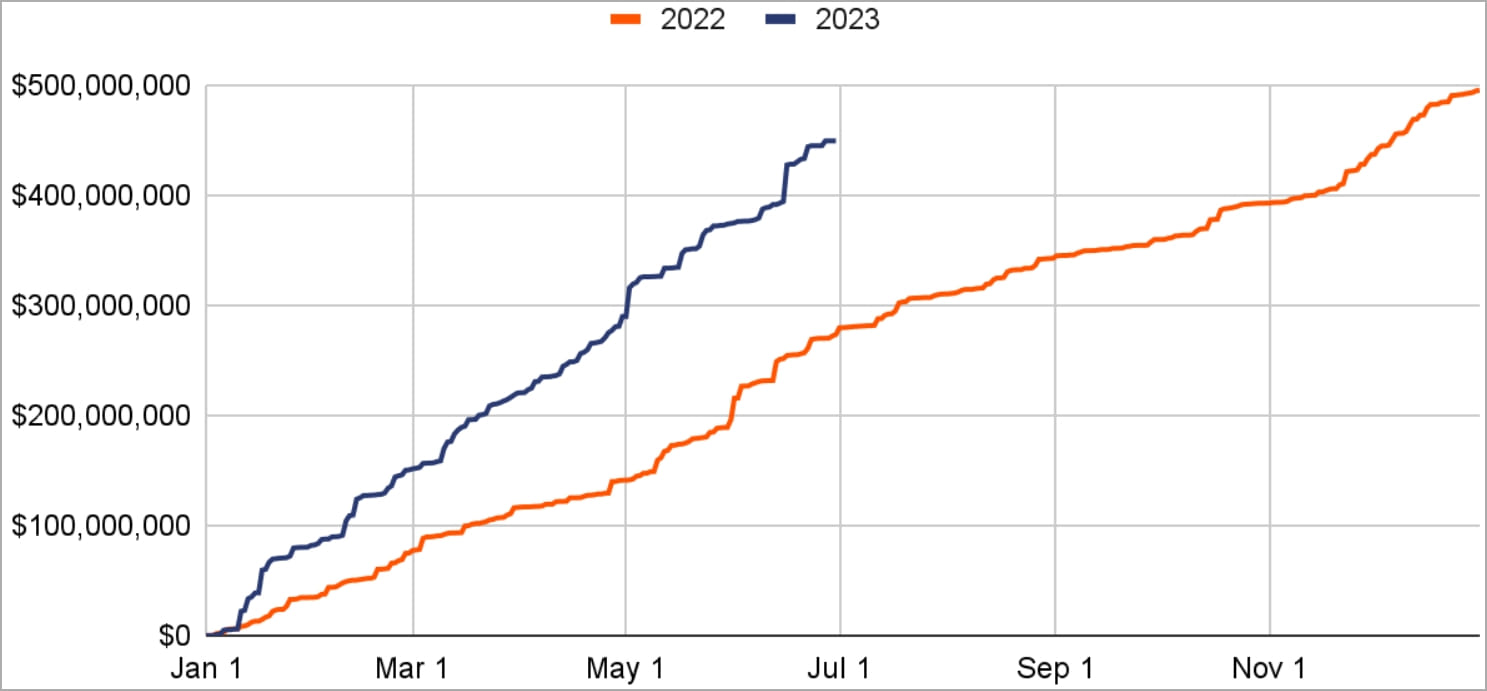
If the pace of revenue growth continues at this level, ransomware actors will earn just under $900 million from victims in 2023, just below 2021’s all-time high of $940 million.
Analysts believe that so-called “big game hunting” is driving this surge in revenue, as cybercriminals have resumed targeting large organizations that can be extorted for large sums of money.
This is reflected in the ransom payment distribution graph, which for the first half of 2023 shows an unprecedented increase on the right side, corresponding to large payments.
.jpg)
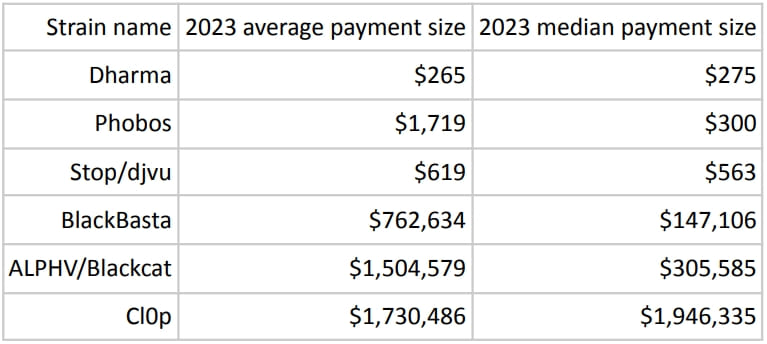
BlackBasta, LockBit, ALPHV/Blackcat, and Clop lead the pack as top high-end payout recipients, with Clop having an average payout amount of $1.7 million and a median payout amount of $1.9 million .
Clop is responsible for two waves of massive attacks exploiting two zero-day vulnerabilities in file transfer tools: Fortra GoAnywhere in the first quarter of the year and MOVEit transfer from Progress in the second.
In fact, Clop’s GoAnywhere campaign, which involved 129 attacks, made March 2023 a banner month because reported by the NCC group at the time.
The MOVEit attack wave is already larger, counting 267 victims to datewith more information on Clop’s extortion site every week.
The growth trend for the first half of 2023 is also seen at the other end of the spectrum, with small ransomware payments being made to opportunistic “spray and pray” ransomware-as-a-service (RaaS) operations such as Dharma, Phobos and STOP/DJVU. , which blackmail victims for a few hundred dollars.
Experts in the field hypothesize that with the annual decrease in the number of organizations willing to pay a ransom, threat actors could strategically increase their ransom demands, with the aim of compensating their losses with substantial payments. from the few people who give in to the demands.
[ad_2]
Source link
