[ad_1]

Play ransomware hackers use a new exploit chain that bypasses ProxyNotShell URL Rewrite Mitigation to achieve Remote Code Execution (RCE) on vulnerable servers through Outlook Web Access (OWA).
Cybersecurity firm CrowdStrike spotted the exploit (dubbed OWASSRF) while investigating Play ransomware attacks where compromised Microsoft Exchange servers were used to infiltrate victims’ networks.
To execute arbitrary commands on compromised servers, ransomware operators used Remote PowerShell to abuse the CVE-2022-41082the same bug exploited by ProxyNotShell.
“In each case, CrowdStrike reviewed the relevant logs and determined that there was no evidence of exploitation of CVE-2022-41040 for initial access,” the researchers said. said.
“Instead, it appeared that the corresponding requests were made directly through the Outlook Web Application (OWA) endpoint, indicating a previously undisclosed method of exploitation for Exchange.”
While ProxyNotShell exploits the target CVE-2022-41040CrowdStrike found that the flaw abused by the newly discovered exploit is likely CVE-2022-41080a security flaw qualified by Microsoft as critical and not exploited in the wild that allows remote elevation of privileges on Exchange servers.
CVE-2022-41080 was discovered and reported by zcgonvh with 360 noah lab and rskvp93, Q5Ca and nxhoang99 with Viettel Cyber Security’s VcsLab.
One of the researchers who found the bug said that it can be leveraged as part of a “chain to RCE Exchange on-premises, Exchange Online, Skype for Business Server (maybe also SFB Online+Teams but can’t find its remote powershell endpoint).”
At this time, it is unclear whether threat actors were abusing this Microsoft Exchange attack chain as a zero-day exploit prior to the release of patches.
OWASSRF PoC exploit leaked online
While security researchers at CrowdStrike worked on developing their own proof-of-concept (PoC) code to match log information found while investigating these recent Play ransomware attacks, threat researcher at Huntress Labs, Dray Agha found and disclosed the tooling of an online threat actor, Dec. 14.
The leaked tool contained a PoC exploit for Play’s Exchange, which allowed CrowdStrike to replicate malicious activity recorded in Play ransomware attacks.
CrowdStrike believes the proof-of-concept exploit was used to drop remote access tools such as Plink and AnyDesk onto compromised servers.
BleepingComputer also discovered that Agha’s leaked tools contained ConnectWise remote administration software, which was also likely deployed in attacks.
Organizations with on-premises Microsoft Exchange servers on their network are advised to apply the latest Exchange security updates (November 2022 being the minimum patch level) or disable OWA until the CVE-2022 patch is released. -41080 can be applied.
Operation Play ransomware launched in June 2022, when the first victims began to ask for help to deal with the fallout from the attacks in the IT Forums.
Since its launch in June, dozens of Play ransomware victims have uploaded samples or ransom notes to the ID Ransomware platform to identify which ransomware was used to encrypt their data.
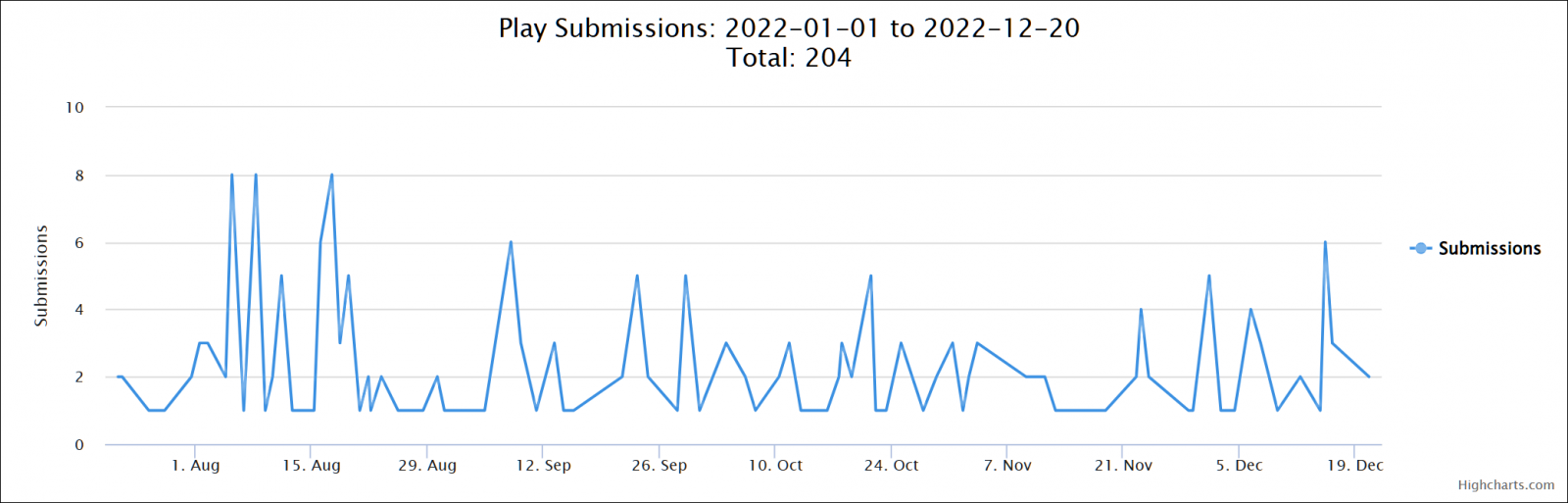
Unlike most ransomware operations, Play affiliates drop simple ransom notes with the word PLAY and a contact email address.
Currently, there are no data leaks related to this ransomware or any indication that data was stolen in any attacks.
Recent victims affected by Play ransomware affiliates include the German hotel chain H-Hotelsthe Belgium city of Antwerpand Argentinian Judiciary of Córdoba.
[ad_2]
Source link
