[ad_1]

PyTorch has identified a malicious dependency with the same name as the framework’s “torchtriton” library. This led to a successful compromise via the Dependency Confusion attack vector.
PyTorch admins are warning users who installed PyTorch-nightly over the holidays to uninstall the framework and the counterfeit ‘torchtriton’ dependency.
From computer vision to natural language processing, the open-source machine learning framework PyTorch has risen to prominence in commercial and academic fields.
Malicious Library Targets Nightly PyTorch Users
Between December 25 and 30, 2022, users who have PyTorch-nightly installed should ensure that their systems have not been compromised, the PyTorch team warned.
The warning follows a “torchtriton” dependency that surfaced over the holidays on the Python Package Index (PyPI) registry, the official third-party software repository for Python.
“Please uninstall it and torchtriton immediately and use the latest nightly binaries (newer than December 30, 2022),” the PyTorch team advises.
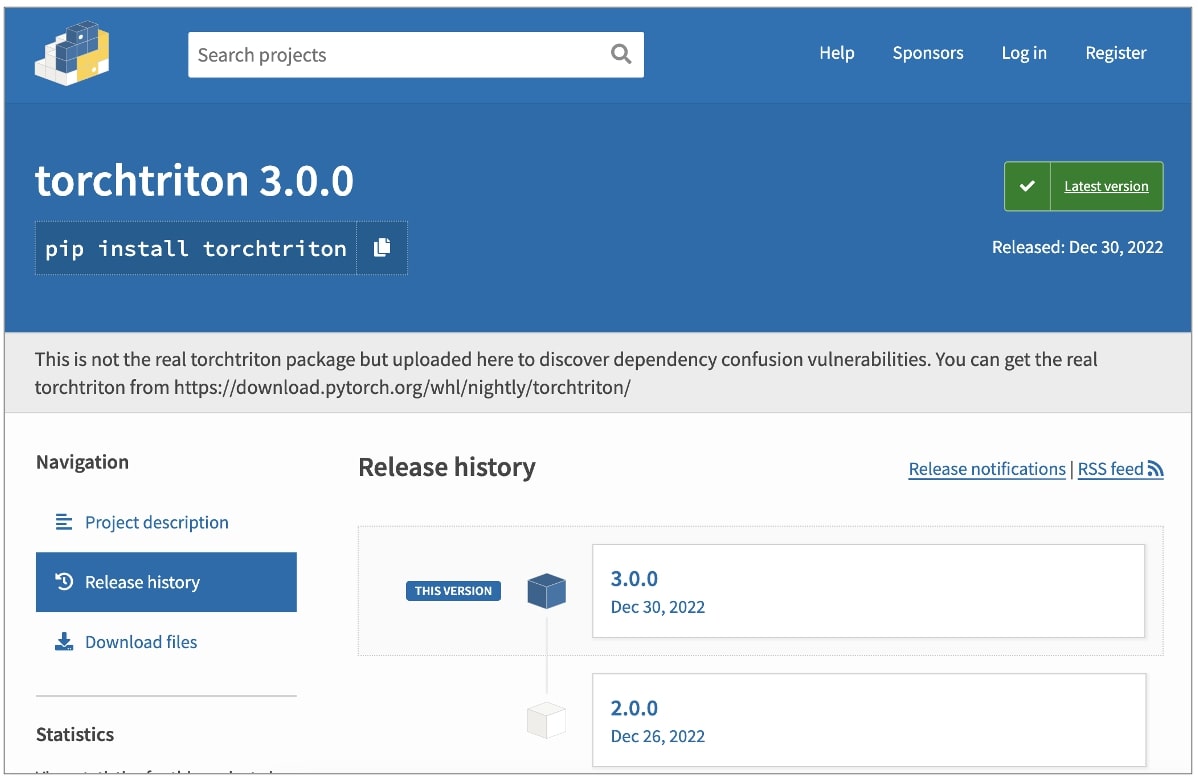
Malicious ‘torchtriton’ dependency on PyPI shares name with official library published on the PyTorch-nightly repo. But, when fetching dependencies in the Python ecosystem, PyPI normally takes precedence, causing the malicious package to be extracted to your machine instead of the legitimate PyTorch one.
” Since The PyPI index takes precedence, this malicious package was installed instead of the version from our official repository. This design allows someone to register a package under the same name that exists in a third-party index, and seed will install their default version,” writes the PyTorch team in a disclosure published yesterday.
At the time of writing, BleepingComputer has observed that the “torchtriton” malicious dependency has outmoded 2,300 downloads last week.
This type of supply chain attack is known as “dependency confusion”, as reported for the first time by BleepingComputer in 2021, just as the attack vector was popularized by an ethical hacker Alex Birsan.
PyTorch states, PyTorch users stable packages are not affected by this issue.
Hacker steals sensitive files and claims ethical research
The malicious “torchtriton” not only monitors your system for basic fingerprinting information (such as IP address, username and current working directory), but it also steals data sensitive:
- Get system information
- name servers of
/etc/resolv.conf - hostname of
gethostname() - current username of
getlogin() - current working directory name
getcwd() - Environment variables
- name servers of
- Plays the following files
- /etc/hosts
- /etc/passwd
- The first 1000 files in $HOME/*
- $HOME/.gitconfig
- $HOME/.ssh/*
It then uploads all of this data, including file contents, to the h4ck.cfd domain via encrypted DNS queries using the wheezy.io DNS server.
PyTorch explains that the malicious “triton” binary contained in the counterfeit “torchtriton” is only executed when the user imports the “triton” package into their build. This would require explicit code and is not the default behavior of PyTorch.
The opinion on the domain h4ck.cfd involved the whole operation is ethical research, but the analysis strongly indicates otherwise.
“Hi, if you came across this in your logs, it’s probably because your Python was misconfigured and vulnerable to a dependency confusion attack. To identify vulnerable companies, the script sends metadata to the host ( such as its current hostname and working directory) Once I have identified vulnerable people and [reported] discovery of all metadata on your server will be removed.”
Contrary to the wording of the review, the binary not only collects “metadata”, but steals the aforementioned secrets, including your SSH keys, ,gitconfig, hosts and password files and the contents of the first 1,000 files in your HOME directory.
BleepingComputer obtained a copy of the malicious binary which, according to VirusTotal, shows a clean reputation at the time of writing. But, don’t be fooled.
We observed that unlike several research packages and PoC exploits that differ in intent and behavior, “torchtriton” uses known anti-VM techniques to evade detection. More importantly, the malicious payload is hidden and entirely contained in the binary format, i.e. Linux ELF files, which makes the library an outlier when juxtaposed with confusing exploits of ethical dependence. the past sent in the clear.
We also noticed that the example reads .bash_history or a list of commands and inputs the user has typed into the terminal, which is yet another trait exhibited by malware.
It also won’t be the first time a hacker has claimed his actions constitute ethical research, just as he’s been caught exfiltrating secrets.
In mid-2022, the extremely popular Python and PHP libraries, ‘ctx’ and ‘PHPass’ respectively, were hacked and modified to steal AWS keys. The researcher behind the attack later claims that it was ethical research.
For the avoidance of doubt, we have approached the owner of h4ck.cfd for comment. Public records show that the domain was registered with Namecheap on December 21, just days before this incident.
Attenuations
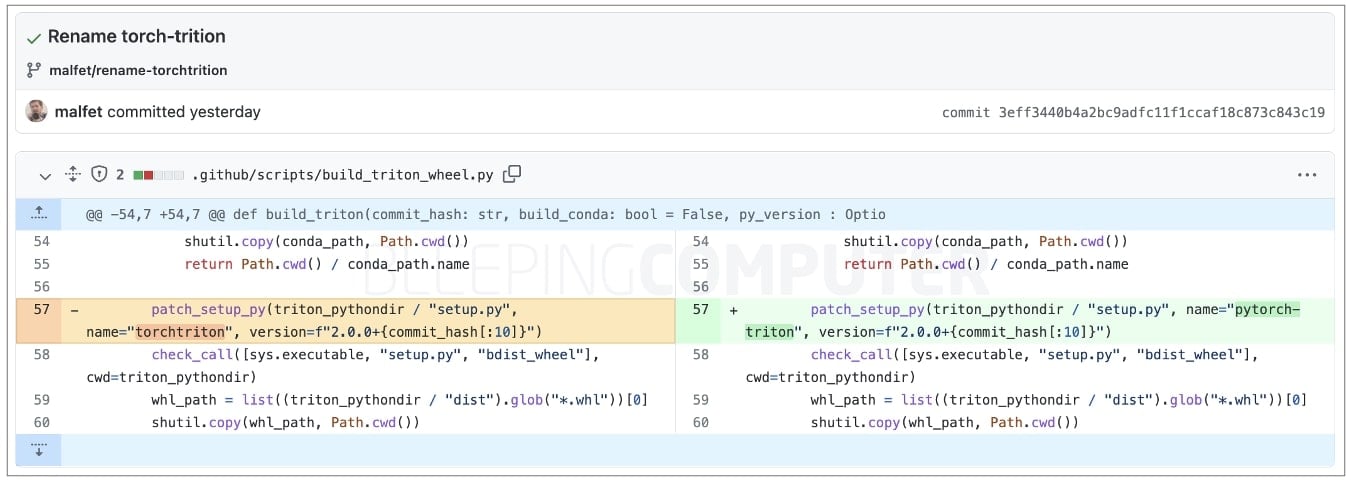
The PyTorch team has renamed the ‘torchtriton’ dependency on ‘pytorch-triton’ and reserved a dummy package on PyPI to prevent similar attacks. The group seeks to claim ownership of the existing “torchtriton” on PyPI to spread the current attack.
To uninstall the malicious dependency chain, users need to run the following command:
$ pip3 uninstall -y torch torchvision torchaudio torchtriton
$ pip3 cache purgeRunning the following command will scan for the presence of malicious binaries and reveal if you are affected:
python3 -c "import pathlib;import importlib.util;s=importlib.util.find_spec('triton');
affected=any(x.name == 'triton' for x in (pathlib.Path(s.submodule_search_locations[0]
if s is not None else '/' ) / 'runtime').glob('*'));
print('You are affected'.format('' if affected else 'not '))"
The SHA256 hash of the ELF binary ‘triton’ is: 2385b29489cd9e35f92c072780f903ae2e517ed422eae67246ae50a5cc738a0e.
[ad_2]
Source link
