[ad_1]

Open source project Moq (pronounced “Mock”) has drawn sharp criticism for quietly including a controversial dependency in its latest release.
Distributed on the NuGet software registry, Moq sees over 100,000 downloads on any given day, and has been downloaded over 476 million times over the course of its lifetime.
Moq’s 4.20.0 release from this week quietly included another project, SponsorLink, which caused an uproar among open source software consumers, who likened the move to a breach of trust.
Seemingly an open-source project, SponsorLink is actually shipped on NuGet as closed source and contains obfuscated DLLs that collect hashes of user email addresses and send these to SponsorLink’s CDN, raising privacy concerns.
Moq breaks user trust
Last week, one of Moq’s owners, Daniel Cazzulino (kzu), who also maintains the SponsorLink project, added SponsorLink to Moq versions 4.20.0 and above.
This move sent shock waves across the open source ecosystem largely for two reasons—while Cazzulino has every right to change his project Moq, he did not notify the user base prior to bundling the dependency, and SponsorLink DLLs contain obfuscated code, making it is hard to reverse engineer, and not quite “open source.”
“It seems that starting from version 4.20, SponsorLink is included,” Germany-based software developer Georg Dangl reported referring to Moq’s 4.20.0 release.
“This is a closed-source project, provided as a DLL with obfuscated code, which seems to at least scan local data (git config?) and sends the hashed email of the current developer to a cloud service.”
The scanning capability is part of the .NET analyzer tool that runs during the build process, and is hard to disable, warns Dangl.
“I can understand the reasoning behind it, but this is honestly pretty scary from a privacy standpoint.”
SponsorLink describes itself as a means to integrate GitHub Sponsors into your libraries so that “users can be properly linked to their sponsorship to unlock features or simply get the recognition they deserve for supporting your project.”
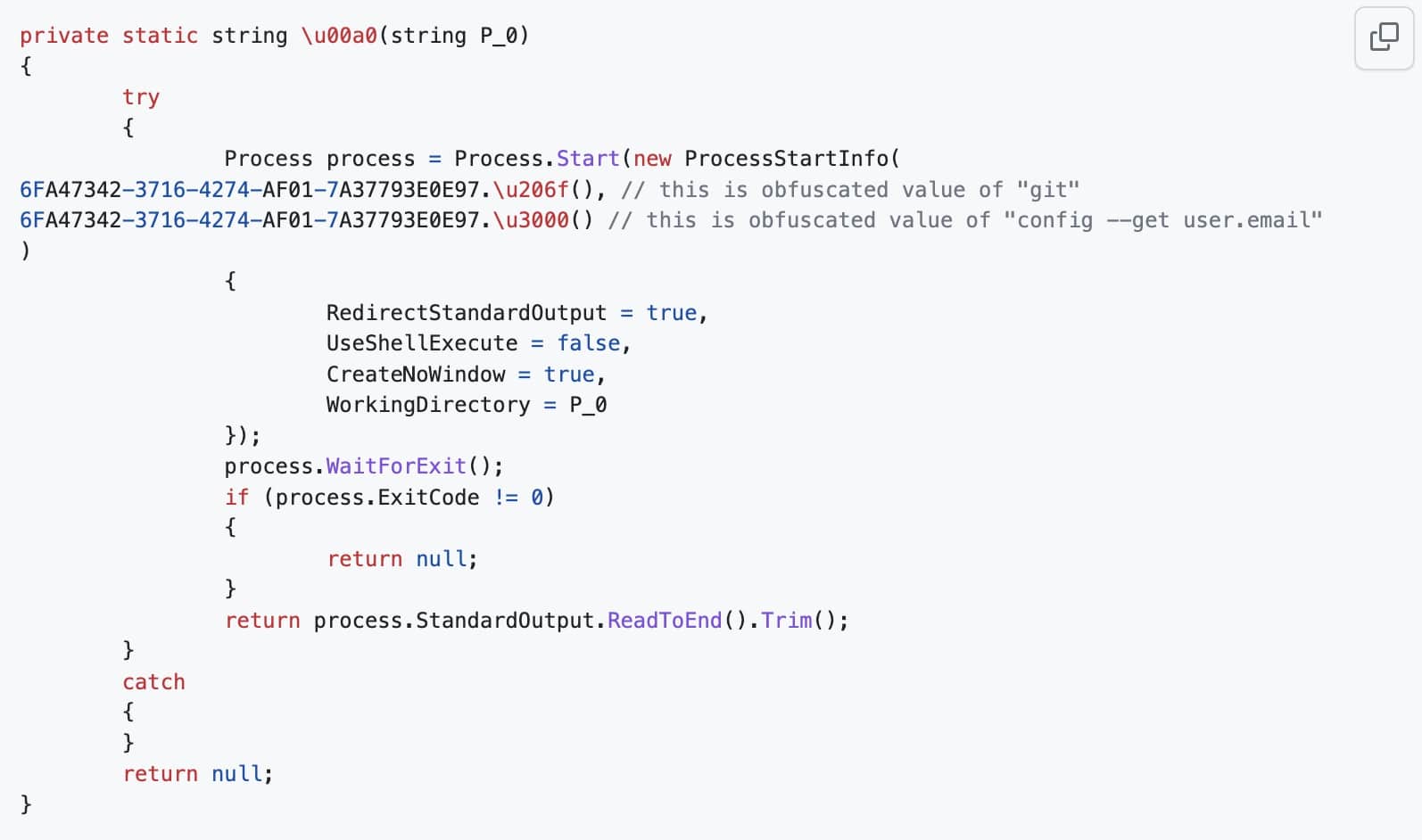
GitHub user Mike (d0pare) decompiled the DLLs, and shared a rough reconstruction of the source code. The library, according to the analyst, “spawns external git process to get your email.”
It then calculates a SHA-256 hash of the email addresses and sends it to SponsorLink’s CDN: hxxps://cdn.devlooped[.]com/sponsorlink.
“Honestly Microsoft should blacklist this package working with the NuGet providers,” writes Austin-based developer Travis Taylor.
“The author can’t be trusted. This was an incredibly stupid move that’s just created a ton of work for lots of people.”
Developer defends change
In a comment, Cazzulino explained his reasons, admitting that the “4.20” version was “a jab so that people wouldn’t take it so seriously.”
“I’ve been testing the waters with SponsorLink for a while now (~6 mo since the announcement),” says Cazzulino.
“It has been hard getting actual feedback, so even if the comments are a “bit” harsh, I really appreciate it!”
Cazzulino further updated the SponsorLink project’s README with a lengthy “Privacy Considerations” section shown below that clarifies that no actual email addresses, just their hashes, are being collected. The update came as of a few hours ago—after the backlash emerged.
There was some concern that SponsorLink might be collecting your email without your explicit consent. This is incorrect, and can easily be verified by running Fiddler to see what kind of traffic is happening.
Specifically, the actual email is never sent when performing the sponsoring check. The email on your local machine is hashed with SHA256, then Base62-encoded. The resulting opaque string (which can never reveal the originating email) is the only thing used.
The only moment SponsorLink actually gets your email address (to perform the backend- side association of that opaque string with your actual email and GH user to link your sponsorship), is after you install the SponsorLink GitHub app and give it explicit permission to do so.
Also, the moment you suspend or uninstall the app, we delete all records associated with your account and your email(s).
“The notice seems to be a reactive response to the online backlash rather than the project being upfront about what data was being harvested,” Ankita Lamba, senior security researcher at Sonatype told BleepingComputer after spotting the update.
In the past, Cazzulino has also defended his decision to keep SponsorLink closed source and obfuscated so as to prevent some of its checks being bypassed. In his words, the opaque features of the library are “by design.”
A potential privacy concern
The quiet inclusion of SponsorLink in projects, such as moq, is a matter of privacy from an ethical and legal standpoint.
First comes the question of an obscure, closed source dependency (SponsorLink) being distributed via open source channels, and being included in popular OSS projects, such as GitInfo—which is also created by Cazzulino and downloaded millions of times.
Collection of email address hashes may not altogether be anonymous either.
In theory at least, SponsorLink’s developer could compare the harvested hashes against a database of email addresses leaked somewhere and identify users.
“I consider your hashing more as a security by obscurity. Even hashed mail should be sent only after consent,” states Michał Rosenbaum.
“I’d say serious concerns have now been raised. The vast majority of users don’t even know this change has been made and would have a problem,” states another software engineer, Kevin Walter.
“Trust with moq is now broken as has GDPR. This is underhanded to say the least. Be one of the good guys,” Walter urged Cazzulino to be more transparent with regards to the obscure SponsorLink package.
In reaction, several developers either threatened to discontinue use of Moq [1, 2] in the favor of alternatives, and building tools that would detect and block any projects that run SponsorLink.
Some went a step further, suggesting they would boycott projects that use SponsorLink or even report “SponsorLink” as malware to the NuGet registry [1, 2].
BleepingComputer has contacted SponsorLink’s creator, Cazzulino, for comment prior to publishing.
[ad_2]
Source link
