[ad_1]

An international law enforcement operation involving the FBI and law enforcement around the world led to the arrest of the alleged administrator of the NetWire remote access Trojan and the seizure of the web domain and service hosting server.
NetWire was a remote access Trojan presented as a legitimate remote administration tool to manage a Windows computer remotely.
The service was sold through the www.worldwiredlabs.com website, where users could purchase subscriptions for as little as $10 per month, which included support.
However, since at least 2014, NetWire has been a tool of choice in various malicious activities, including phishing attacks, BEC Campaignsand to breach corporate networks.
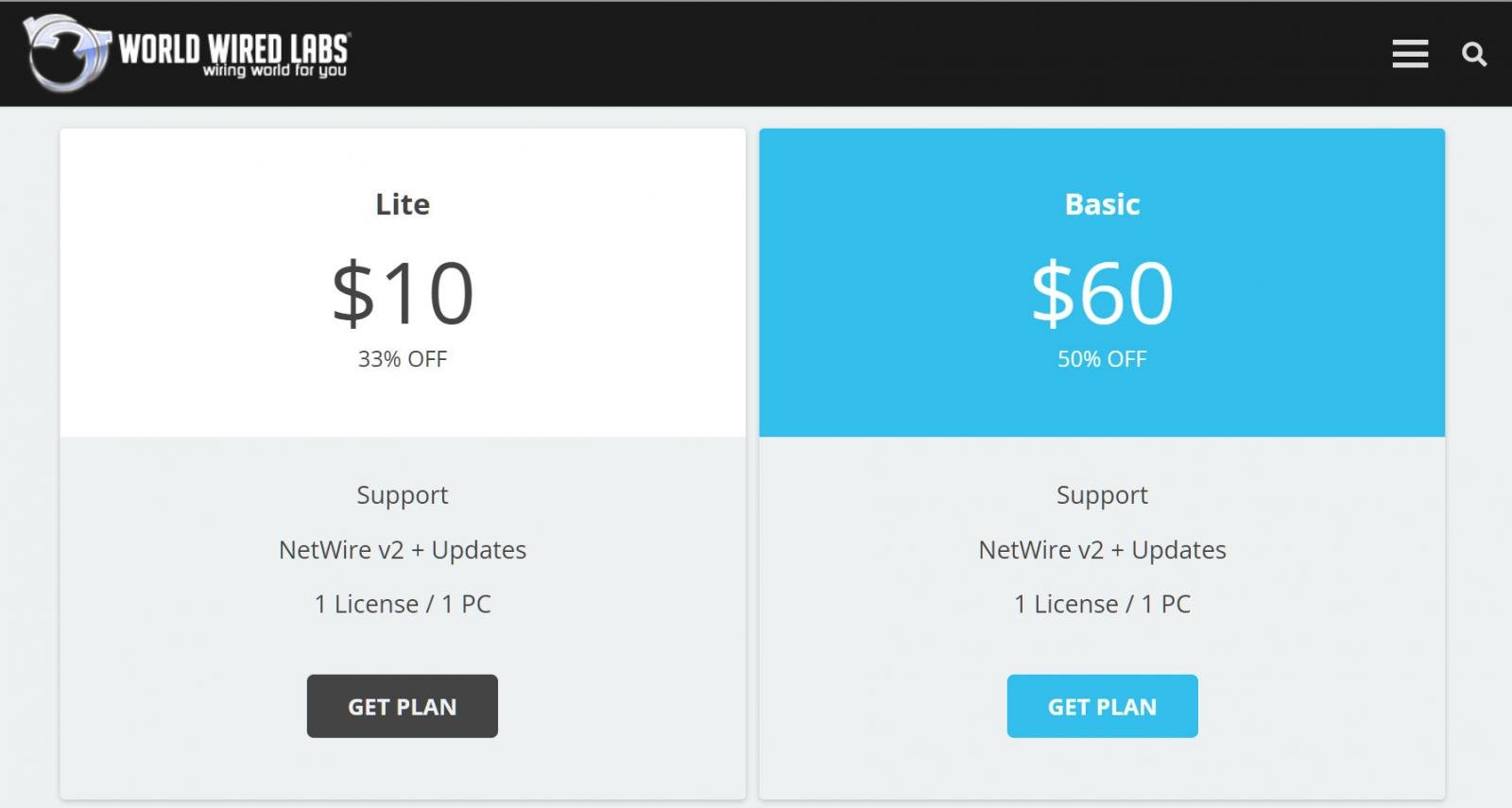
Threat actors could use the Netwire RAT to remotely take screenshots, upload and download files, run commands, or download other programs to run on infected Windows computers.
NetWire infrastructure seized by police
Today, the U.S. Attorney’s Office for the Central District of California announced that a warrant of seizure was approved on March 3 and executed on Tuesday as part of a coordinated international law enforcement operation to disrupt NetWire service.
This operation involved the FBI Police, the United States Attorney’s Office for the Central District of California, the Criminal Police Directorate of the Croatian Ministry of the Interior, the Zurich Cantonal Police, Europol and the Australian Federal Police. .
As part of the operation, the FBI seized the worldwiredlabs.com domain used to promote the service, and Swiss police seized the server hosting the website.
The website now displays a seizure message stating: “This website was seized in a coordinated law enforcement action against the NetWire Remote Access Trojan”.
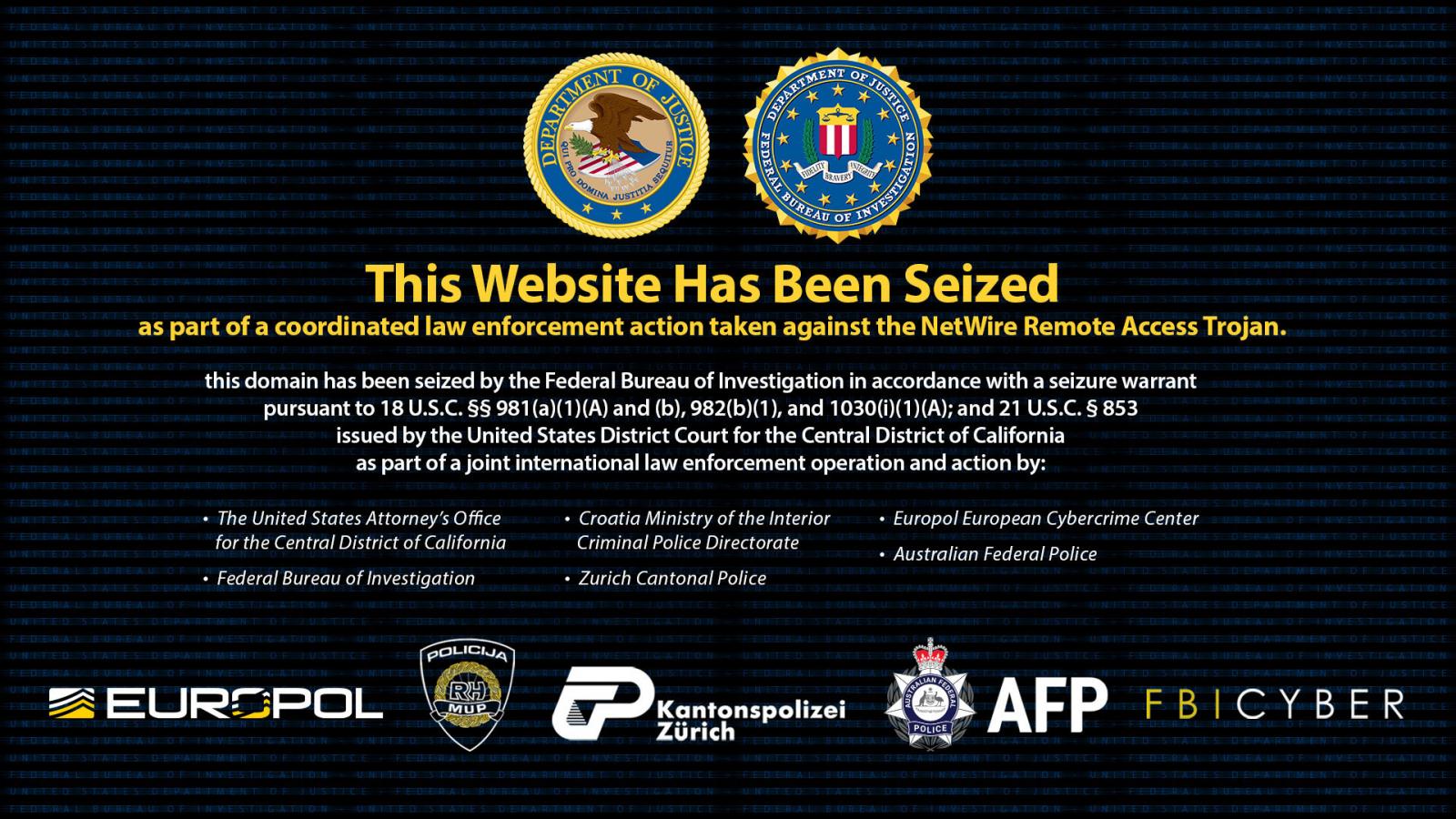
Source: BleepingComputer
A Croatian national suspected of being the administrator of the NetWire site was also arrested in Croatia on Tuesday and will be prosecuted by local authorities.
“By removing the Netwire RAT, the FBI has impacted the criminal cyber ecosystem,” said Donald Alway, deputy director in charge of the FBI’s Los Angeles field office.
“The global partnership that led to the arrest in Croatia also removed a popular tool used to hijack computers to perpetuate global fraud, data breaches and network intrusions by threat groups and cybercriminals. “
[ad_2]
Source link
