[ad_1]

Three popular WordPress plugins with tens of thousands of active installs are vulnerable to high-severity or critical SQL injection vulnerabilities, with proof-of-concept exploits now publicly available.
SQL injection is a website security flaw that allows attackers to enter data into form fields or through URLs that modify legitimate database queries to return different data or modify a database.
Depending on whether the website code is vulnerable to an SQL injection flaw, an attacker could modify or delete data on a site, inject malicious scripts, or gain full access to the website.
Proof-of-concept exploits released
The three vulnerable plugins were discovered by Tenable security researcher Joshua Martinelle, who responsibly reported them to WordPress on December 19, 2022, along with proofs of concept (PoC).
The plugin authors released security updates to fix the issues in the following days or weeks, so all issues have been resolved now, and those running the latest available version are no longer vulnerable.
Yesterday, the researcher disclosed technical details about each vulnerability along with proof-of-concept exploits using the SLEEP feature to demonstrate how the flaws work.
The first plugin that was found to be vulnerable to SQL injection is ‘Pro Paid Subscriptions‘, a membership and subscription management tool used in over 100,000 websites.
“The plugin does not escape the ‘code’ parameter in the REST route /pmpro/v1/order before using it in an SQL statement, which leads to an unauthenticated SQL injection vulnerability”, reveals Tenable Post.
The flaw is tracked as CVE-2023-23488, receiving a CVSSv3 severity rating of 9.8 (critical), and it affects all versions of the plugin prior to 2.9.8. Paid Memberships Pro fixed the vulnerability on December 27, 2022, with the release of version 2.9.8.
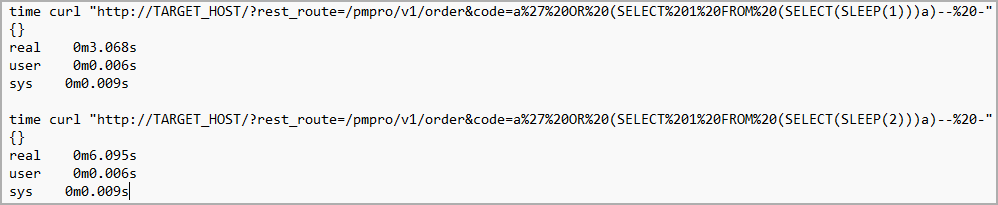
The second WordPress add-on vulnerable to SQL injection is ‘Easy digital downloads‘, an e-commerce solution for selling digital files with over 50,000 active installs.
“The plugin does not escape the ‘s’ parameter in the ‘edd_download_search’ action before using it in an SQL statement, leading to an unauthenticated SQL injection vulnerability,” Tenable explains.
“The vulnerable part of the code corresponds to the function ‘edd_ajax_download_search()’ of the file ‘./includes/ajax-functions.php’.”
The vulnerability is tracked as CVE-2023-23489 and received a CVSSv3 severity rating of 9.8, categorizing it as critical. The flaw affects all versions below 3.1.0.4, released on January 5, 2023.
Finally, Tenable discovered CVE-2023-23490, a “high-severity” SQL injection flaw in ‘Survey Marker‘, a WordPress plugin used by 3,000 websites for surveys and market research.
The flaw was given a severity rating of 8.8, according to CVSS v3, because the attacker must be authenticated as at least a subscriber to exploit it.
However, this prerequisite is usually easy to fulfill, as many websites allow visitors to register as members.
Survey Marker was the fastest vendor to respond to Tenable’s SQL injection discovery, releasing a remediation update on December 21, 2022, with version 3.1.2.
While all of these plugins were vulnerable to SQL injection and proof-of-concept exploits were published, Tenable did not share the impact they could have if exploited in attacks.
However, since bugs are classified as critical, it is recommended that all sites using these plugins upgrade to the latest version.
[ad_2]
Source link
