[ad_1]

A Brazilian hacking group has been targeting thirty Portuguese public and private financial institutions since 2021 in a malicious campaign called “Operation Magalenha”.
Examples of targeted entities include ActivoBank, Caixa Geral de Depósitos, CaixaBank, Citibanamex, Santander, Millennium BCP, ING, Banco BPI and Novobanco.
This campaign was revealed by a Sentinel Labs report highlighting the tools used by the threat actor, the different infection vectors and their malware distribution methods.
Analysts uncovered details about the threat actor’s origin and tactics through a server misconfiguration that exposed files, directories, internal correspondence, and more.
The initial infection
Attackers use many methods to distribute their malware to targets, including phishing emails claiming to be from Energias de Portugal (EDP) and the Portuguese Tax and Customs Authority (AT), social engineering and malicious websites that imitate these organizations.
Either way, the infection begins by executing an obfuscated VB script that fetches and executes a malware loader, which in turn loads two variants of the “PeepingTitle” backdoor onto the victim’s system after a five-second delay.
“VB scripts are obfuscated in such a way that malicious code is dispersed among large amounts of code comments, which are typically content pasted from publicly available code repositories,” Sentinel Labs explains in the report.
“This is a simple but effective technique for evading static detection mechanisms – the scripts available on VirusTotal have relatively low detection rates.”
Analysts explain that the purpose of these scripts is to distract users while downloading malware and to steal their EDP and AT credentials by directing them to the corresponding fake portals.
‘PeepingTitle’ backdoor
PeepingTitle is malware written in Delphi with a build date of April 2023, which Sentinel Labs claims was developed by a single person or team.
The reason attackers drop two variants is to use one to capture the victim’s screen and the second to monitor windows and the user’s interactions with them.
Additionally, the second variant can fetch additional payloads after registering the victim machine and sending reconnaissance details to the attackers.
The malware searches for windows that match a hard-coded list of financial institutions and, when it finds one, logs all user input (including credentials) and sends it to the C2 server of the author of the threat.
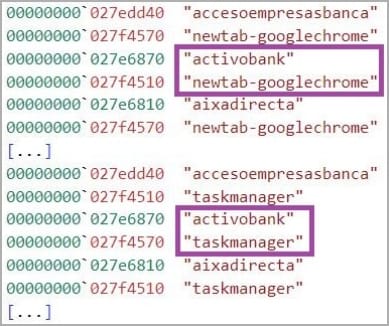
PeepingTitle can also capture screenshots, terminate processes on the host, change its monitor interval configuration on the fly, and organize payloads from executables or DLL files, using Windows rundll32.
Sentinel Labs has noticed several instances where threat actors have demonstrated their ability to overcome operational obstacles since the start of Operation Magalenha.
In mid-2022, the group stopped abusing DigitalOcean Spaces for hosting and distributing C2 malware and started using more obscure cloud service providers like Russia-based Timeweb.
Analysts believe the move was due to DigitalOcean’s due diligence causing too much campaign disruption and operational difficulties.
[ad_2]
Source link
