[ad_1]

Geacon, a Go-based implementation of the tag from the widely abused Cobalt Strike penetration testing suite, is increasingly being used to target macOS devices.
Both Geacon and Cobalt Strike are utilities that legitimate organizations use to simulate attacks against their networks and improve defenses, but threat actors have also relied on them for attacks.
In the case of Cobalt Strike, threat actors have been abusing it to compromise Windows systems for years, with the infosec industry making a continuous effort For fight it.
Security Researchers at SentinelOne Geacon activity monitoring in the wild recently noticed an increase in the number of payloads on VirusTotal. Although some of them showed signs of participating in a red team operation, others showed the traits of malicious attacks.
Development and availability of forks
When Geacon first appeared on GitHub as a promising port for Cobalt Strike that could work on macOS, hackers seemed to pay little attention to it.
However, SentinelOne reports that this changed in April, after anonymous Chinese developers released two Geacon forks on GitHub: Geacon Plus – free and accessible to the public, and the paid private version, Geacon Pro.
Historical data from Virus Total indicates that the Mach-O payloads for the free variant of the fork have been in development since November 2022.
Today the Geacon fork has been added to the ‘404 Project Starlink‘, a public GitHub repository dedicated to Red Team Penetration Testing Tools maintained by the Zhizhi Chuangyu Lab since 2020.
This inclusion helped increase the popularity of the Geacon fork and seems to have caught the attention of malicious users.
Deployment in the wild
SentinelOne found two instances of Geacon’s malicious deployment across two VirusTotal submissions that occurred on April 5 and April 11.
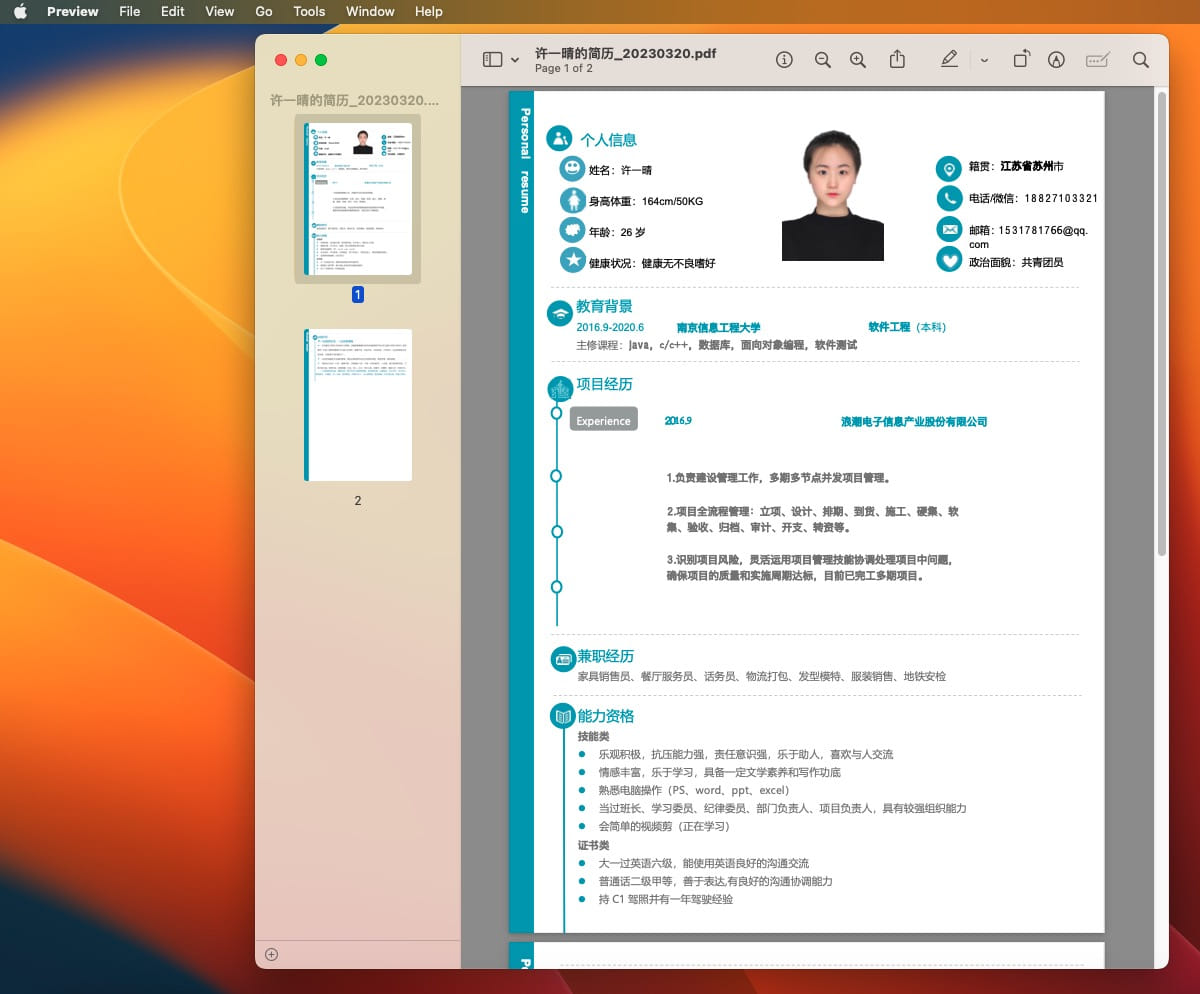
The first is an AppleScript applet file named “Xu Yiqing’s Resume_20230320.app”, which is designed to confirm that it is running on a macOS system before fetching an unsigned “Geacon Plus” payload from a command and control server (C2) with a Chinese IP Address.
The researchers note that the particular C2 address (47.92.123.17) has previously been associated with Cobalt Strike attacks on Windows machines.
Before initiating its “markup activity”, the payload displays a decoy PDF file to the victim – a CV for an individual named Xy Yiqing.
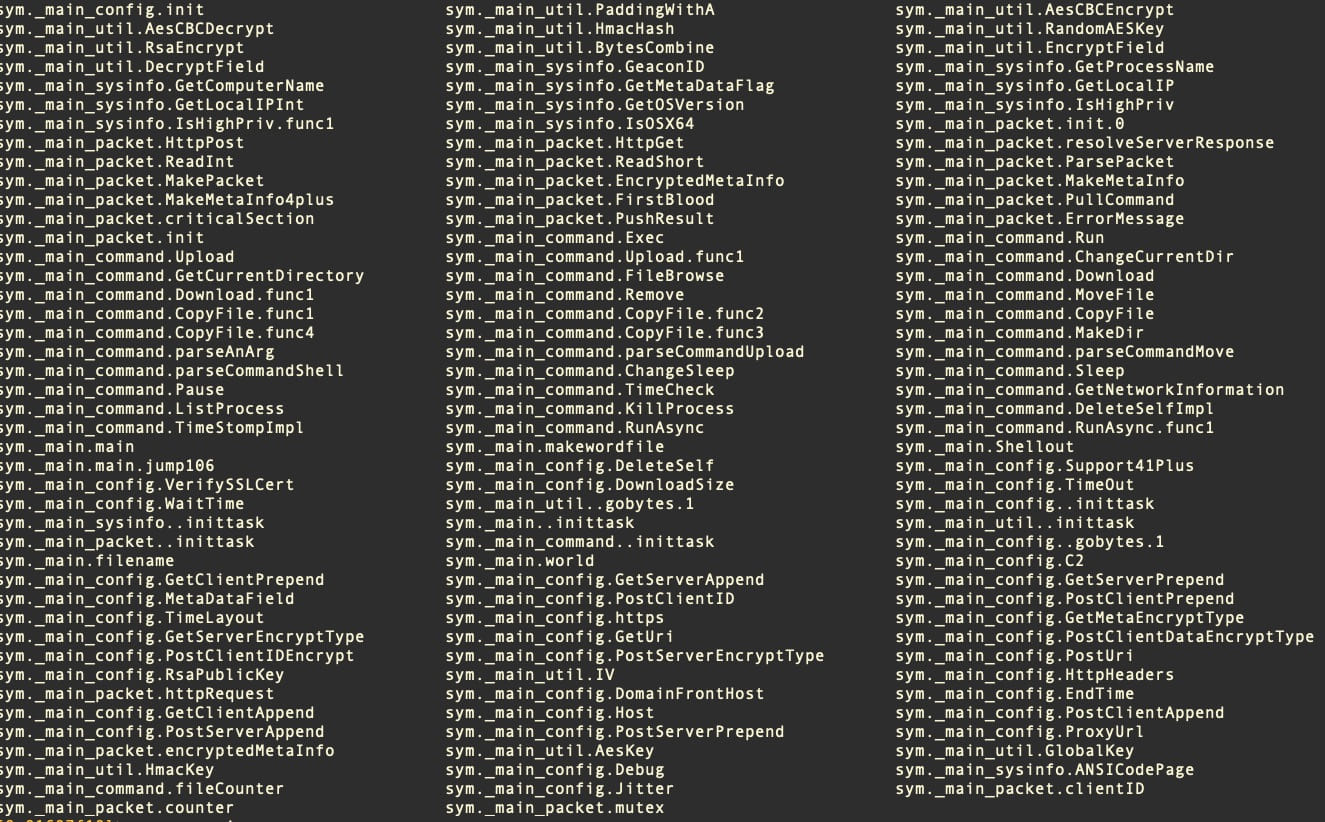
The Geacon payload supports network communications, data encryption and decryption, it can download additional payloads and exfiltrate data from the compromised system.
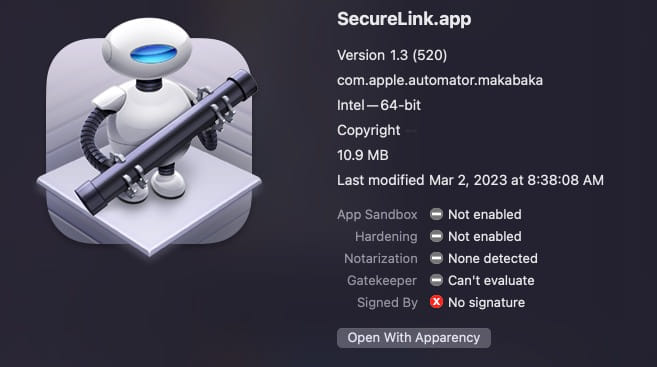
The second payload is SecureLink.app and SecureLink_Client, a trojanized version of the SecureLink application used for secure remote support, which contains a copy of “Geacon Pro”.
In this case, the binary only targets Intel-based Mac systems, OS X versions 10.9 (Mavericks) and later.
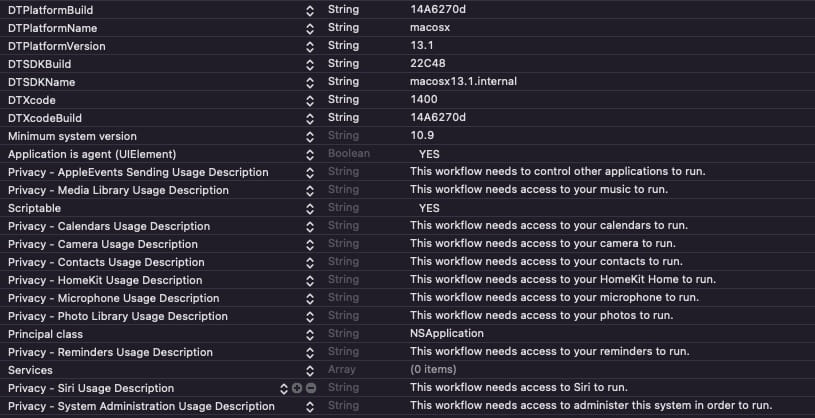
On launch, the app requests access to the camera, microphone, contacts, photos, reminders, and even computer admin privileges, which are normally protected by the Transparency privacy framework, Apple Consent and Control (TCC).
Although these are extremely risky permissions, the type of hidden app is such that the user’s suspicions can be allayed, thus tricking them into acceding to the app’s request.
In this case, the C2 server IP address (13.230.229.15) that Geacon is communicating with is based in Japan and VirusTotal has connected it to past Cobalt Strike operations.
While SentinelOne agrees that some of the Geacon activity observed is likely related to legitimate Red Team operations, there is a good chance that real adversaries “are using public and possibly even private Geacon forks. “.
This conclusion is supported by the increase in the number of Geacon samples observed over the past few months, which security teams should respond to by implementing adequate defenses.
SentinelOne has provided a list of Indicators of Compromise (IoCs) that organizations can use to create appropriate protections against the Geacon threat.
[ad_2]
Source link
