[ad_1]

Online vendors are targeted in a new campaign to push Vidar information-stealing malware, allowing threat actors to steal credentials for more damaging attacks.
The new campaign launched this week, with threat actors sending complaints to online store administrators via email and website contact forms.
These emails claim to be from an online store customer who had $550 deducted from his bank account after an alleged order was not properly placed.
BleepingComputer received one such email this week and after investigating the attack found it widespread with numerous submissions to VirusTotal over the past week.
Target online sellers
Online sellers are a juicy target for threat actors because obtaining credentials on the backend of e-commerce sites enables various types of attacks.
For example, once a hacker gains access to an online store’s admin backend, they can inject malicious JavaScript scripts to run MageCart Attacksthat is, when the code steals credit cards and personal information from customers during checkout.
Backend access can also be used to steal a site’s customer information by generating backups for the store’s database, which can be used to extort victimsthreatening to pay a ransom, otherwise the data would be publicly disclosed or sold to other threat actors.
Earlier this week, BleepingComputer received an email claiming to be from a customer who was charged $550 even though an order was incorrectly placed, which is displayed below.
“I am writing to express my deep concern and disappointment regarding a recent transaction I made on your website.
On May 14, 2023, I purchased items over $550 from your store.
However, a substantial problem has arisen that requires your immediate attention.
Right after I completed the purchase, I encountered an error signal on your webpage that it was unable to complete the payment and no money was taken from my card banking.
To my surprise, upon examining my bank account, I discovered that the payment had been executed and the same amount had been withdrawn.
I urge you to address this issue with the utmost urgency and resolve the issue promptly.
It is essential that you analyze the cause of this discrepancy and take immediate action to return the amount of money withdrawn.
For your review and as proof of purchase, I have provided a copy of my bank statement below, which obviously shows the withdrawal of funds.
This should serve as definitive proof of payment and emphasize the urgency of full reimbursement.
I will sincerely appreciate your immediate actions.
Here is the hyperlink to my statement https://bit.ly/xxxx”
Attached in the email above is a bit.ly link to the alleged bank statement, shortened to hide the original link.
The email is written to convey a sense of urgency, demanding that the retailer issue a refund and investigate the root cause of the issue.
Clicking on the URL will bring up a website that claims to be Google Drive. In BleepingComputer’s tests, this fake Google Drive will show a bank statement or prompt the user to download the bank statement.
The domains believed to be associated with this campaign are:
http://bank.verified-docs.org[.]za/
http://chase.sign-docs.org[.]za/
http://documents.cert-docs.net[.]za/
http://documents.verified-docs[.]com/
https://bank.cert-docs.net[.]za
https://bank.my-sign-docs[.]com
https://bank.sign-documents[.]net.za
https://bank.sign-documents[.]org.za
https://bank.verified-docs[.]net.za
https://bank.verified-docs[.]org.za
https://bank.verified-docs[.]site
https://chase.cert-docs.co[.]za
https://chase.my-sign-docs[.]org
https://chase.sign-docs.net[.]za
https://chase.sign-docs.org[.]za
https://chase.sign-documents.co[.]za
https://chase.sign-documents.org[.]za
https://documents.cert-docs.co[.]za
https://documents.my-sign-docs[.]org
https://documents.sign-docs.co[.]za
https://documents.verified-docs.org[.]za
https://sign-documents.net[.]za/
https://statements.my-sign-docs.net[.]za/
https://statements.sign-docs.co[.]za/
https://statements.sign-documents.co[.]za/
https://statements.sign-documents.net[.]za/
https://statements.sign-documents.org[.]za/
https://statements.verified-docs.org[.]za/
https://verified-docs[.]com/If the site displays the bank statement, it displays a Commerce Bank bank statement example which uses sample data, such as the customer name “Jane Customer” at “Anywhere Dr.”
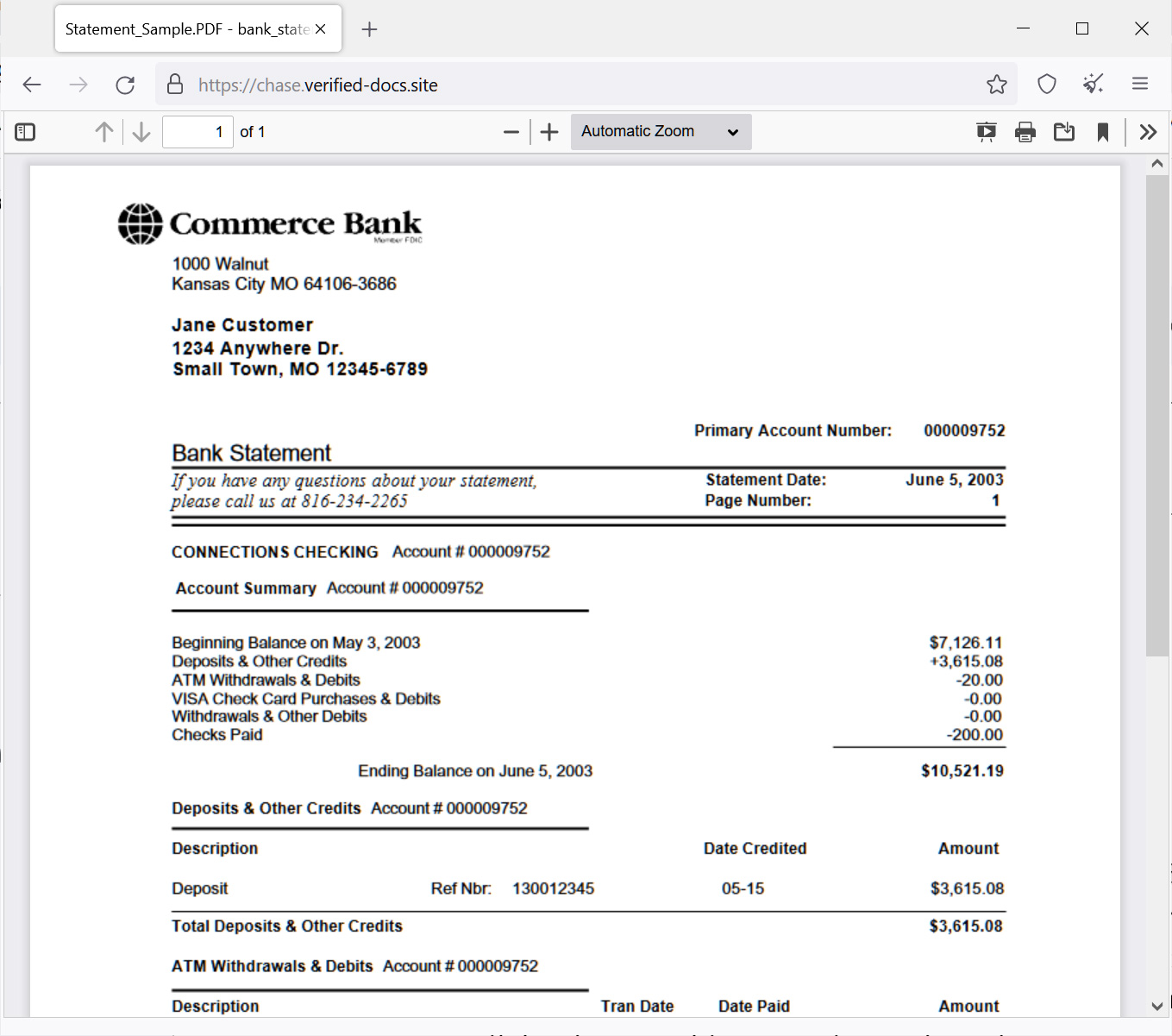
Source: BleepingComputer
However, other tests would show a fake Google Drive page stating that a preview is not available and prompting the user to download the “Bank_statement.pdf”. However, this will actually download an executable named ‘bank_statement.scr’.
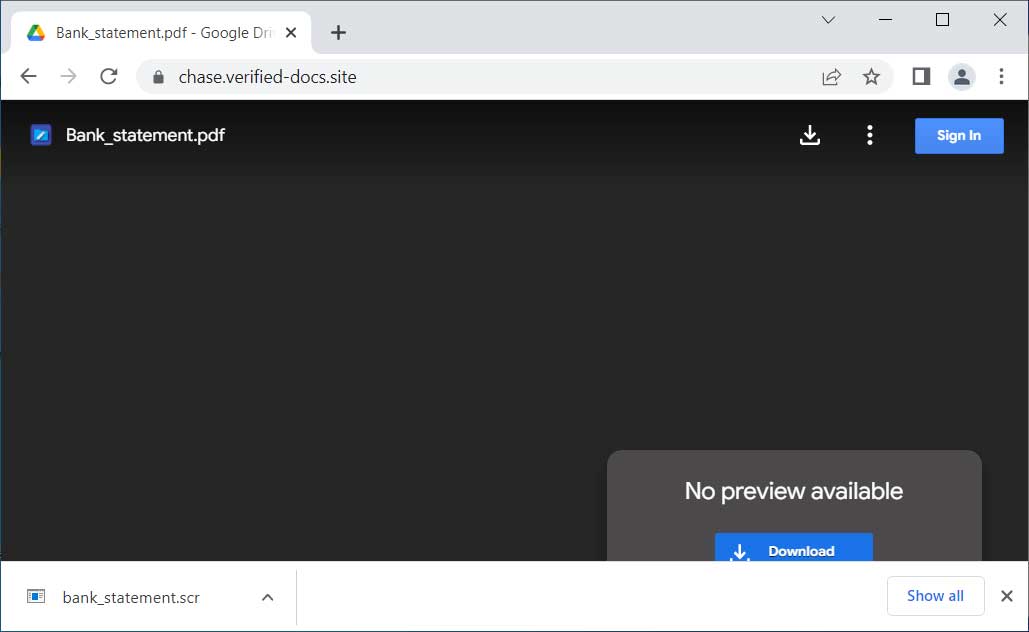
Source: BleepingComputer
While antivirus vendors on VirusTotal only detect it as a generic information thief, Triage of the recorded future detected it as the Vidar information-stealing malware.
Vidar is an information-stealing trojan that can steal browser cookies, browser history, saved passwords, cryptocurrency wallets, text files, Authy 2FA databases, and screenshots of the active Windows screen.
This information will then be uploaded to a remote server for attackers to collect. After sending the data, the collection of files will be deleted from the infected machine, leaving behind a directory full of empty folders.
Once the threat actors receive the stolen information, they sell the credentials to other threat actors or use them to breach the accounts used by the victim.
If you have received similar emails and believe that you have been affected by this malware distribution campaign, it is essential that you immediately scan your computer for malware and remove anything found.
To prevent further attacks, you should change your password on all of your accounts, especially those associated with your e-commerce sites, bank accounts, and email addresses.
Finally, carefully examine your e-commerce site for source code injected into HTML templates, new accounts with elevated privileges, or site source code changes.
[ad_2]
Source link
