[ad_1]

The National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), and Office of the Director of National Intelligence (ODNI) have released a joint report that highlights the most likely risks and potential threats in security implementations. 5G network slicing. .
The report also provides mitigation guidance and a framework for developing defense and prevention strategies implemented by 5G network operators, integrators and vendors.
The 5G Network Slicing Report relies on Potential threat vectors for 5G infrastructurea document released last year by the cross-industry Enduring Security Framework (ESF) working group focused on managing risks and threats to the security and stability of US national security systems.
5G network slicing
5G network slicing is a configuration architecture that allows multiple virtualized and independent networks to be created on top of a common physical infrastructure.
Each network slice is an isolated end-to-end network dedicated to meeting particular requirements for each application.
Potential applications for network slices include autonomous vehicle fleets, virtual and augmented reality solutions, industrial automation systems, and more.
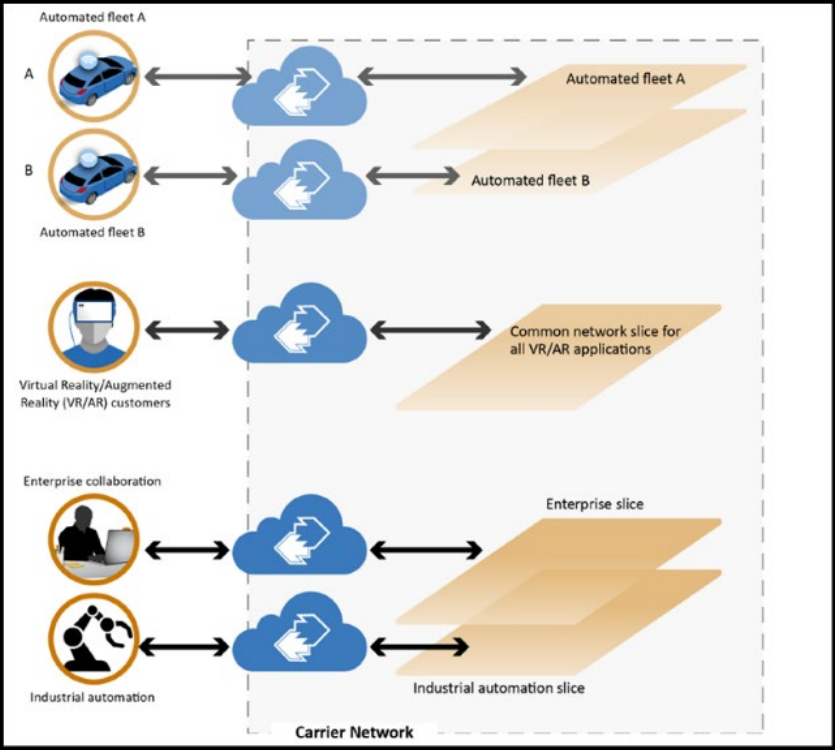
Network slice users for each of these applications are authenticated for that particular network zone, providing data and security isolation for the larger 5G infrastructure and other slices.
Network slicing is made possible through Network Functions Virtualization (NFV), one of the key benefits of a 5G network, providing different users with operational efficiency, resilience and better quality of service and support .
NFV essentially removes the need for hardware like routers and firewalls and virtualizes them into cloud-based servers. It also moves all network functions to the air interface or the cloud, and dynamically allocates bandwidth to meet each user’s performance requirements.
Additionally, NFV provides better monitoring and logging options, allowing network engineers to detect anomalies and more effectively prevent security breaches.
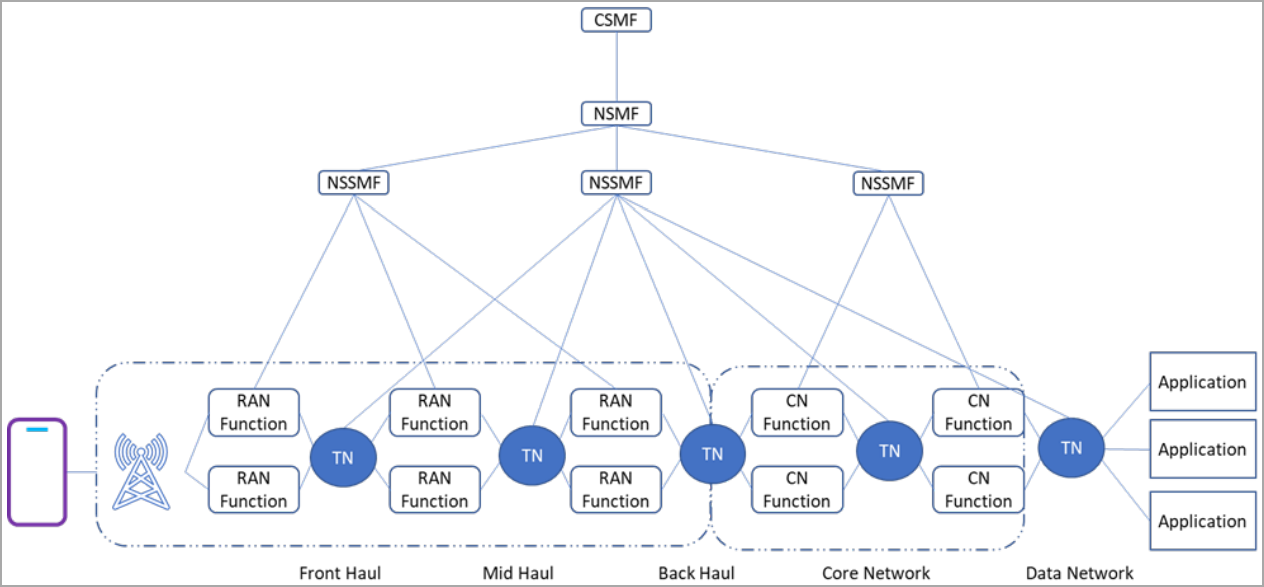
Mobile network operators are implementing 5G network slicing through specialized network management and network orchestration (MANO) systems.
“The MANO system [shown below] supports design and creation of slices, activation, deactivation, and termination across the radio access network (RAN), core network, and transport network domains,” the guide explains.
Most Important Threats
The CISA guidelines highlight the complexity of managing network slices, leading to critical security vulnerabilities.
“While there are standards defining specifications for how network operators build their 5G network, there are no clear specifications for how network operators should develop and implement security for the cutting of the network”, mentions the newspaper.
“Mismanagement of network slices can allow malicious actors to access data from different network slices or deny access to priority users.”
The three most relevant threat vectors for 5G network slicing are denied service (DoS) attacks on centralized control elements, attacks exploiting misconfigured system controls, and middle man (MitM) attacks on unencrypted network channels.
In the case of DoS attacks, the threat actors disrupt the service, thereby rendering the network slice unavailable to legitimate users.
MitM attacks would not only threaten to leak confidential information and expose user data, but could also allow an intermediary to modify transmitted messages, leading to misinformation.
Attacks taking advantage of misconfigurations could have a wide range of implications, as the adversary could exploit them to disable system monitors and security features.
Chaining together multiple attack types is also possible, delivering potentially devastating attacks that could extend beyond a single network slice.
CISA provides an example of such an attack where a malicious actor conducts an International Mobile Subscriber Identity (IMSI) caching attack on an autonomous vehicle service, degrading its performance and reliability.
The attacker uses IMSI caching to infer precise vehicle location, cargo information, and routes.
Next, the threat actor deploys a DoS attack on the network signaling location to disrupt the link between the autonomous vehicle and its controller, and then launches a configuration attack to disable security features or modify VNF policies.
If the operator does not have robust security measures in place to prevent unauthorized policy changes, the attacker could expand their access to other network slices on the same infrastructure.
Mitigation Recommendations
CISA suggests operators apply network management and monitoring in four logical layers (shown below) to identify and address any potentially malicious disruptions as soon as possible.
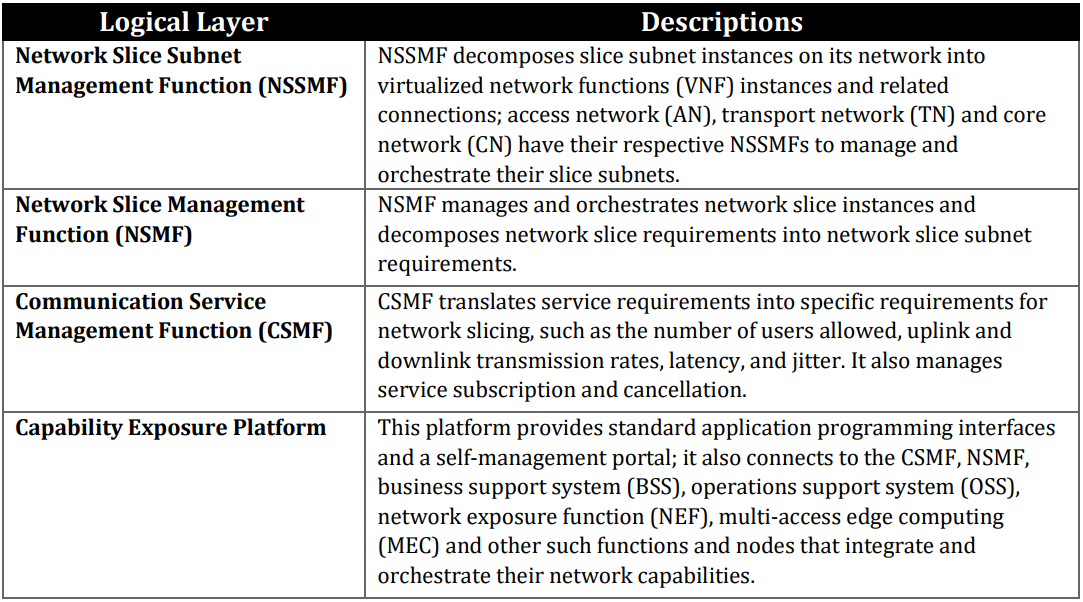
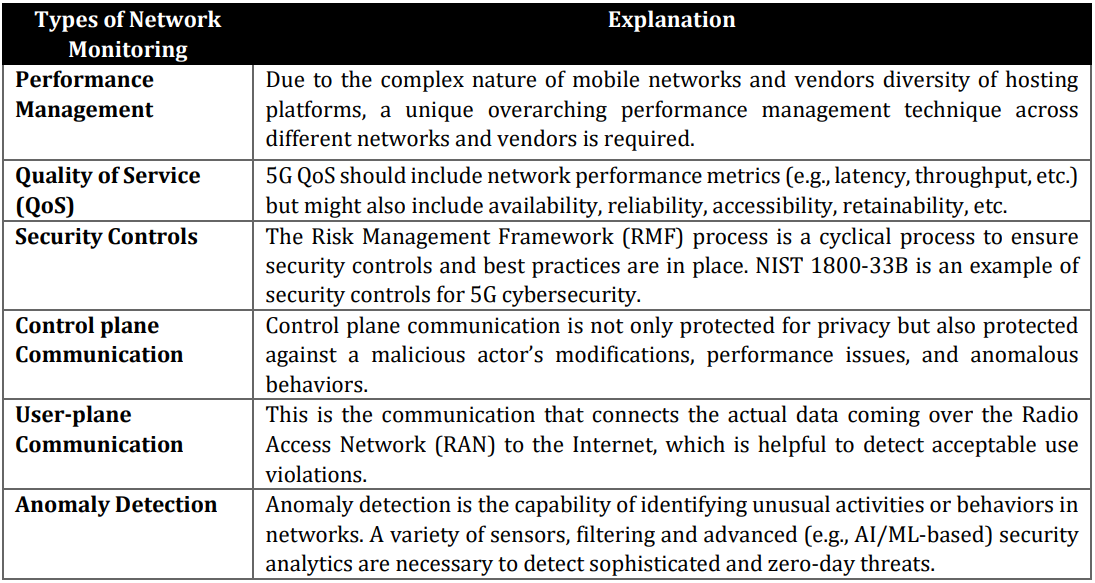
Additionally, the guidelines suggest that carriers use multiple network monitoring solutions, as these generate different data that can be used to better understand unauthorized network activities.
The document promotes the principles of Zero Trust architecture where all connected users are constantly verified and all network requests are validated.
This makes intruder activities less likely to go unnoticed or have a damaging impact, as no user is inherently trustworthy, so they must be stopped at one of multiple data inspection points .
Common components of the Zero Trust strategy include multi-factor authentication, data encryption, multi-layered security for access control, cross-domain boundaries, and instance isolation.
[ad_2]
Source link
